Introduction to Stellar Cyber
Stellar Cyber Open XDR is a purpose built platform for unified Security Operations (SecOps). Stellar Cyber was designed to deliver the most performant and easy-to-use approach to defending the entire attack surface. Stellar Cyber takes a platform approach to unifying SecOps, which specifically means building multiple native capabilities into the platform while maintaining an open system such that Stellar Cyber can intelligently command and control (collect and respond) through the rest of the security stack. This allows security teams to get value from Stellar Cyber Open XDR immediately because it works with existing tools and has intelligence (in the form of alerts and auto-correlation) built-in, and to consolidate capabilities where possible based on what Stellar Cyber natively offers. This combination of native and open is ultimately what drives a more performant and easy-to-use approach to SecOps, all the while keeping SecOps teams future-proofed against changing investments.
-
Native Capabilities: Sensors (includes deep packet inspection, IDS, Malware Sandbox; for NDR), Bi-Directional Integrations, Data Lake/Data Modeling, AI Engine, Threat Intelligence, and Automated Response.
-
Open System: Hundreds of integrations with other tools, products, and data sources, including:
-
All top EDRs supported
-
All top Cloud providers supported
-
All top identity providers supported
-
Top Use Cases
Stellar Cyber Open XDR is a modular platform in the sense that you can choose which features and capabilities to leverage. However, given that the platform is purpose-built for unified SecOps, it is best leveraged when deployed in its entirety. Here are some common use cases for deploying Stellar Cyber to deliver value to SecOps teams:
SOC Platform
The SOC Platform use case represents leveraging Stellar Cyber in its entirety, most specifically to be used as both a NG-SIEM and NDR that intelligently correlates data. Leveraging Stellar Cyber as a SOC Platform entails deploying sensors, connecting to every available data source, running reporting, and setting up automation. This offers the best approach to high-performance detection and response while allowing teams to consolidate multiple capabilities onto one platform.
Legacy SIEM Replacement
Stellar Cyber Open XDR has NG-SIEM functionality built in, which is the combination of Integrations, a Data Lake, Reporting, and Threat Hunting. Stellar Cyber is commonly used to replace legacy SIEMs that are found to be too expensive (both on license costs and supporting human resources) and too slow when it comes to detection and response. Stellar Cyber excels at having a robust package of built-in intelligence in the form of alerts, auto-correlation, reports, and playbook templates. For this reason, when compared to legacy SIEMs, users find Stellar Cyber both faster to deliver value and more future-proof.
Complement SIEM
SecOps teams often want to keep their existing SIEM, either because it is working effectively or the license terms don’t allow for it to be changed. In this scenario, Stellar Cyber is commonly brought in to complement the existing SIEM by bringing it new alerts and correlation. In this use case, Stellar Cyber operates in front of the existing SIEM, consuming data and running all available alerting strategies, and then sending those alerts to the SIEM so existing workflows are not interrupted. This not only adds significant new intelligence to the existing SIEM, but it also helps decrease SIEM costs if Stellar Cyber is relied on for the heavier data processing.
NDR
When touching the SIEM in any way is not a SecOps priority, NDR is a common way to obtain much of the value from the Stellar Cyber Open XDR platform with a painless deployment. Purely deploying NDR involves deploying network and endpoint sensors in every relevant environment (that is, both on-premises and cloud), connecting a few high value contextual data sources (for example, EDR, Identity), and letting the AI Engine detect and correlate network risks and anomalies. Stellar Cyber can be operated independently of other SecOps tools from its UI, or it can send alerts to other systems for a more cohesive approach to detection workflows. Since Stellar Cyber offers more than just NDR, it is common for many SecOps teams to add more telemetry sources to their instance which essentially begins to cover more SIEM-like workflows. This is a useful approach for tool consolidation and is seamless because Stellar Cyber operates on a single license for all features.
High Level Platform Overview
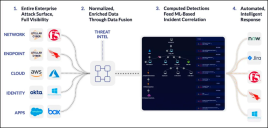
Stellar Cyber’s platform objective is to deliver the most performant and easy-to-use approach to defending the entire attack surface. Conceptually, there are four parts to the platform to accomplish that, as illustrated and described below:
1. Collect - Entire Enterprise Attack Surface, Full Visibility
Stellar Cyber Open XDR has hundreds of integrations spanning from API Connectors to Log Source Integrations. Additionally, Stellar Cyber has its own Sensors that package in DPI, IDS, and Malware Sandbox functionality. All three of these sources in conjunction provide visibility over the entire attack surface.
2. Data Processing - Normalized, Enriched Data Through Data Fusion
Regardless of the data source, Stellar Cyber converts all data into the same data model called Interflow. A standard normalized data model is critical for Machine Learning (ML) because source data looks different across environments and vendors and has to be controlled to deploy intelligence reliably. Additionally, Stellar Cyber enriches data with Threat Intelligence and entity information to create valuable records for detection.
3. Detection - Computed Detections Feed ML-Based Case Correlation
Alerts in Stellar Cyber are generated either from Machine Learning or simpler analytic methods (that is, rules). Stellar Cyber creates novel Alerts in its platform based on input data sources and also leverages Alerts from source tools through various Alert Pathways. For example, alerts generated by an EDR can become Alerts in Stellar Cyber after some processing if that EDR is integrated with Stellar Cyber. Stellar Cyber then automatically correlates all Alerts into Cases in real time. A case represents potentially related activity, either high risk behavior or a real attack.
4. Response - Automated, Intelligent Response
Stellar Cyber users can respond back through a Connector, such as an EDR or Identity provider, in one of two ways. First, mid-investigation, the full response action menu is available so a user does not have to move to another screen. Second, users can leverage automated playbooks to take certain actions based on any criteria to automate as many common workflows as possible
Refer to Stellar Cyber Architecture for a more detailed overview of the product architecture.