Configuring CyberCNS Connectors
This connector allows Stellar Cyber to ingest logs from CyberCNS and add the records to the data lake. It integrates with the CyberCNS API to get vulnerability information.
Connector Overview: CyberCNS
Capabilities
-
Collect: Yes
-
Respond: No
-
Native Alerts Mapped: No
-
Runs on: DP
-
Interval: Configurable
Collected Data
|
Content Type |
Index |
Locating Records |
|---|---|---|
|
Vulnerabilities |
Scans |
Domain
|
<Domain Name> where <Domain Name> is a variable from the configuration of this connector |
Response Actions
N/A
Third Party Native Alert Integration Details
N/A
Required Credentials
-
Domain Name, Tenant Name, Client ID, Client Secret
Let us know if you find the above overview useful.
Adding a CyberCNS Connector
To add a CyberCNS connector:
Obtaining CyberCNS Credentials
Before you configure the connector in Stellar Cyber, you must obtain the following CyberCNS credentials:
-
Client ID
-
Client Secret
-
Log in to CyberCNS as an administrative user.
-
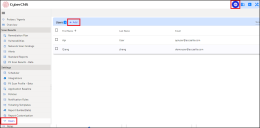
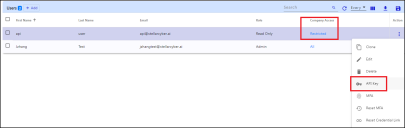
Navigate to Settings | Users and click Add.
-
You can add a user to All Companies or to Specific Companies.
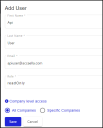
To add a user to All Companies:
-
Enter the First Name, Last Name, and Email.
-
Choose a Role, for example, readOnly.
-
Click All Companies.
-
Click Save.
-
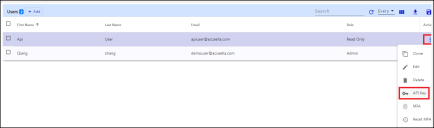
Under Action, click the three vertical dots icon and choose API Key.
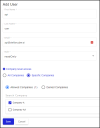
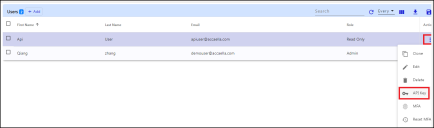
To add a user to Specific Companies:
-
-
Copy the API key.
Store the API key in a safe location. It cannot be retrieved later although it can be regenerated.
Adding the Connector in Stellar Cyber
To add a CyberCNS connector in Stellar Cyber:
-
Log in to Stellar Cyber.
-
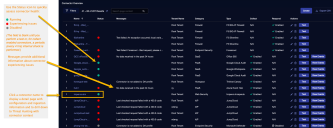
Click System | Integration | Connectors. The Connector Overview appears.
-
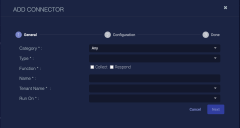
Click Create. The General tab of the Add Connector screen appears. The information on this tab cannot be changed after you add the connector.
The asterisk (*) indicates a required field.
-
Choose Vulnerability Scanner from the Category drop-down.
-
Choose CyberCNS from the Type drop-down.
-
For this connector, the supported Function is Collect, which is enabled already.
-
Enter a Name.
This field does not accept multibyte characters.
-
Choose a Tenant Name. The Interflow records created by this connector include this tenant name.
-
Choose the device on which to run the connector.
-
(Optional) When the Function is Collect, you can create Log Filters. For information, see Managing Log Filters.

-
Click Next. The Configuration tab appears.
The asterisk (*) indicates a required field.
-
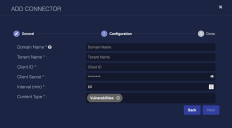
Enter the Domain Name. For example, portaluseast2.mycybercns.com or portaluswest2.mycybercns.com.
Do not include the http/https prefix.
-
Enter the Tenant Name. This is the name of the CyberCNS tenant.
-
Enter the Client ID you noted above in Obtaining CyberCNS Credentials.
-
Enter the Client Secret you noted above in Obtaining CyberCNS Credentials.
-
Choose the Interval (min). This is how often this connector retrieves data from CyberCNS. The default interval is 60 minutes.
-
Choose the Content Type you would like to collect. The logs for Vulnerabilities are supported.
-
Click Next. The final confirmation tab appears.
-
Click Submit.
To pull data, a connector must be added to a Data Analyzer profile if it is running on the Data Processor.
The new connector is immediately active.
Testing the Connector
When you add (or edit) a connector, we recommend that you run a test to validate the connectivity parameters you entered. (The test validates only the authentication / connectivity; it does not validate data flow).
For connectors running on a sensor, Stellar Cyber recommends that you allow 30-60 seconds for new or modified configuration details to be propagated to the sensor before performing a test.
-
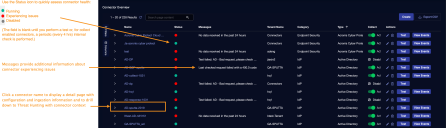
Click System | Integrations | Connectors. The Connector Overview appears.
-
Locate the connector that you added, or modified, or that you want to test.
-
Click Test at the right side of that row. The test runs immediately.
Note that you may run only one test at a time.
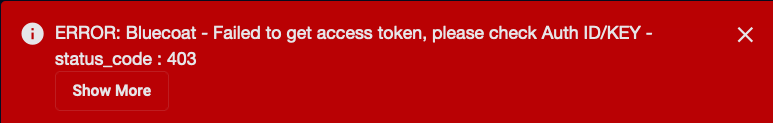
Stellar Cyber conducts a basic connectivity test for the connector and reports a success or failure result. A successful test indicates that you entered all of the connector information correctly.
To aid troubleshooting your connector, the dialog remains open until you explicitly close it by using the X button. If the test fails, you can select the button from the same row to review and correct issues.
The connector status is updated every five (5) minutes. A successful test clears the connector status, but if issues persist, the status reverts to failed after a minute.
Repeat the test as needed.
Verifying Ingestion
To verify ingestion:
-
Click Investigate | Threat Hunting. The Interflow Search tab appears.
-
Change the Indices for the type of content you collected. For Vulnerabilities change the Indices to Scans. The table immediately updates to show ingested Interflow records.