Configuring Threat Intelligence
You must have Root scope to use this feature.
The System | Integration | Threat Intelligence page lets you specify an external threat intelligence feed used by Stellar Cyber to identify developing security threats. An external feed specified in this page augments the dynamic threat intelligence synchronization provided automatically by Stellar Cyber, where multiple different feeds are regularly collected, parsed, and distributed to the Stellar Cyber solution.
You can choose one of the following types of additional threat intelligence feeds:
-
Third-party Threat Intelligence Platform (TIP). In this release, the only supported third-party feed is Anomali ThreatStream. Stellar Cyber uses data from this feed type to enrich its existing alerts.
-
Custom IoC file hosted on a customer-managed server and linked via URL from the System | Integration | Threat Intelligence page. Stellar Cyber generates Emerging Threat alerts based on matching IP addresses, URLs, and domains from this feed type.
Threat Intelligence Configuration
Use the following procedure to configure an external threat intelligence feed:
Gather Prerequisites
-
If you are using a customer-managed IoC file hosted on your own server, create the file using the proper name and syntax and validate it using Python scripts provided by Stellar Cyber. The file is essentially a table listing URLs, IP addresses, and fully-qualified domains with an associated severity score. Stellar Cyber uses this table to generate Emerging Threat alerts on matching values detected in incoming data.
-
If you are using Anomali ThreatStream, make sure you have the following information:
-
URL for the ThreatStream API
-
Username and password or API key
The password should not include non-ASCII special characters.
-
Add the External Threat Feed in Stellar Cyber
-
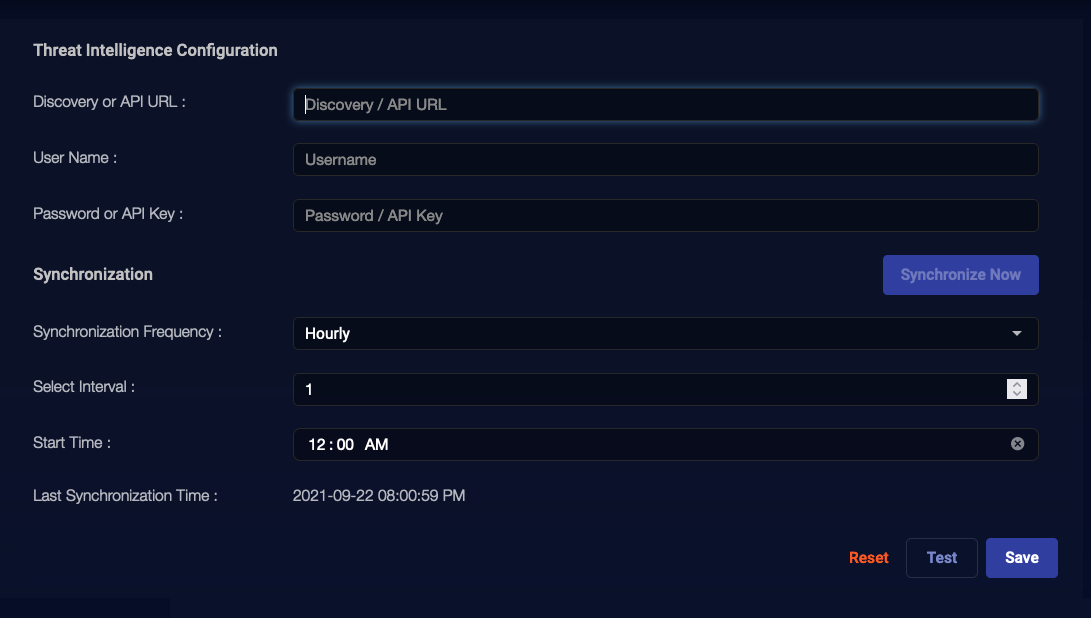
Navigate to the System | Integration | Threat Intelligence tab in Stellar Cyber.
-
Supply the URL to your Anomali ThreatStream feed or customer-managed IoC file in the Discovery or API URL field:
-
Anomali ThreatStream Feed: Enter a URL for the Anomali ThreatStream server. Include the schema (usually https) and port, if required. For example:
https://api.threatstream.com:9998.
The URL can be either a generic API URL or one configured for a custom feed .
-
Customer-managed IoC File: Enter a URL pointing directly to an allthreat.tsv file you host on a server you manage for Stellar Cyber to ingest. The URL must end with the /allthreat.tsv suffix. Refer to Creating, Validating, and Maintaining a Custom IoC File for details on creating, validating, and maintaining the allthreat.tsv file.
-
- Enter the username of the account to be used for authentication in the User Name field.
- Enter a password or a ThreatStream API key for the specified user account in the Password or API key field.
-
Set Synchronization options for the threat intelligence feed:
-
Synchronize Now – Click to synchronize immediately. When you click this button, Stellar Cyber immediately retrieves data from the provided URL. This is a contrast to the Test button, which only verifies connection to the provided URL.
-
Synchronization Frequency – Select how often Stellar Cyber downloads data from the community. Can be hourly, daily, or weekly.
-
Select Interval – Select the number of intervals between downloads.
-
Start Time – The time the download starts. Synchronization will begin after all related operations are done; this may take approximately 15 minutes.
-
Last Synchronization Time – This field is read-only and shows the time of the last synchronization.
Disabling the synchronization interval is not recommended. Doing so causes the local Data Analyzer AI information-base to age out of date and as a result possibly not detect new security events.
-
-
Finalize the configuration by clicking Save to apply your changes. While you are modifying your parameters, you can also Reset the configuration to the original values and Test the connection to the provided URL.
The Test button only verifies that it can reach the provided URL. It does not retrieve data. You can use the Synchronize Now button to retrieve data immediately. However, keep in mind that if there is no data to retrieve, the Synchronize Now button will not inform you of this.