About the Threat Intelligence Platform
This topic covers a feature that is not available for all customers yet. See Early Access Program Features and Topics Under Development.
Stellar Cyber's Threat Intelligence Platform (TIP) provides multiple threat intelligence feeds that bring in Indicators of Compromise (IoCs). TIP provides primary operations on the IoCs, such as import and export, as well as a variety of feeds. Using TIP, you can collect IoCs from the sources you like and you can create your own feeds.
In the 5.2.0 release, the minimum requirements are 6 GB memory, 4 CPU cores, and 10 GB storage available.
User Interface
The user interface for the System | Integrations | Threat Intelligence Platform page has two tabs, one for IoCs and one for feeds.
The IoCs tab displays all the latest IoCs that are present in storage, along with data associated with each IoC, such as expiration date, source, and confidence score.
The Feeds tab displays the threat intelligence feeds, which have three types:
-
Built-in feeds are provided by Stellar Cyber. They include AlienVault OTX, DHS, Emerging Threat (ET) Pro IP, ET Pro Domain, ET Pro Rules, PhishTank, Abuse.ch (urlhaus and SSL certs), OpenPhish, as well as Stellar Cyber's Emerging Threat feed.
-
Premium feeds include Cybersixgill and Anomali ThreatStream. They are provided by Stellar Cyber. You configure them in TIP with credentials that you purchase.
-
Custom feeds include TAXII and TSV. You configure them in TIP with credentials that you provide, for example, credentials for a TAXII server or credentials to access a TSV file.
To manage IoCs, see Managing IoCs in the Threat Intelligence Platform.
To configure and manage Feeds, see Configuring Feeds in the Threat Intelligence Platform.
To manage role-based access control at the System level, see Configuring Role-Based Access Control.
The Threat Intelligence Platform (TIP) is configured globally for an organization.
Architecture
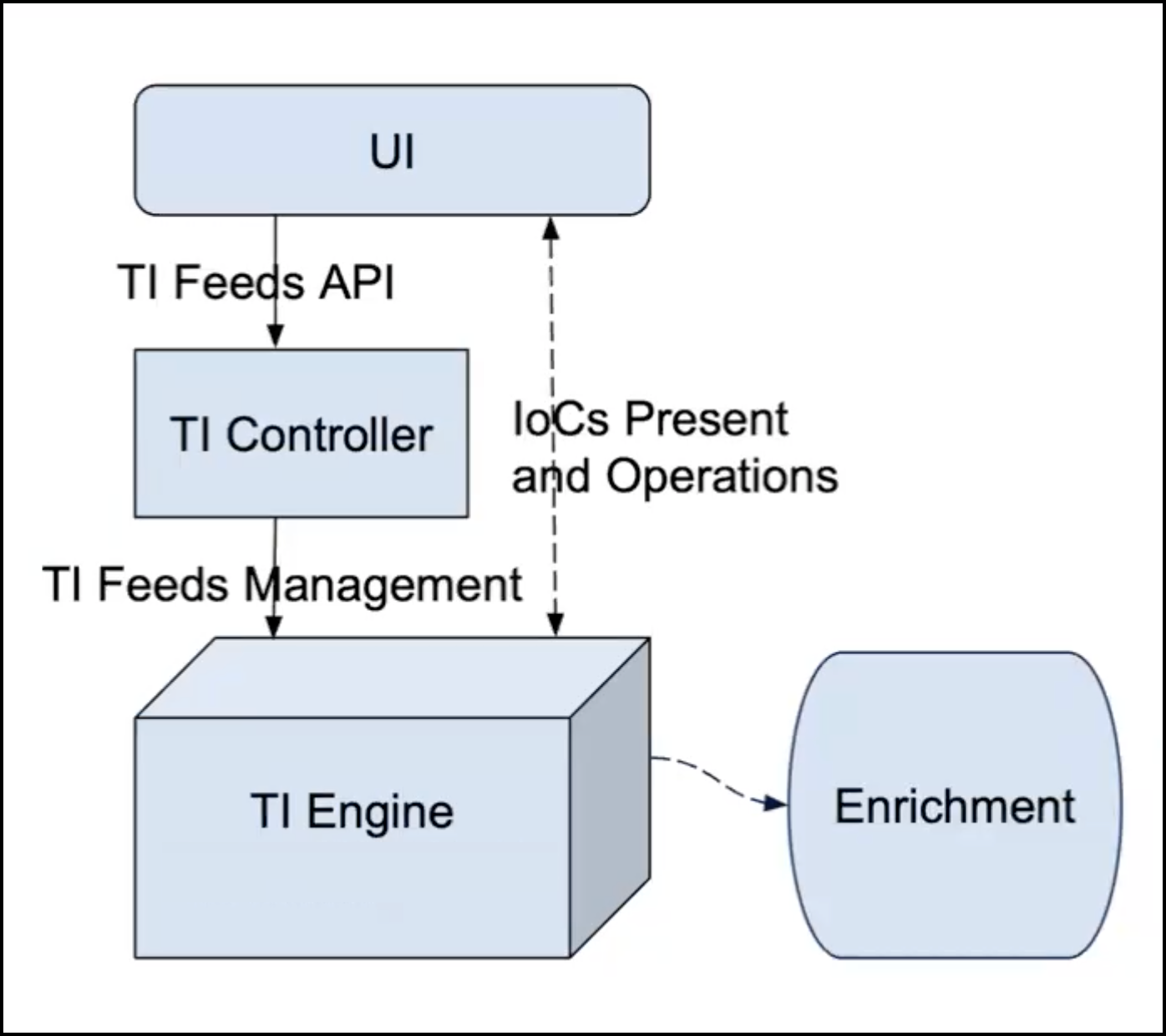
The following simplified architecture diagram shows the user interface (UI), Threat Intelligence (TI) Controller, and TI Engine.
The user interface sends data to the TI Controller through the TI Feeds API. The TI Controller performs management of the feeds for the TI Engine. Feeds management includes actions such as, Create, Delete, Enable/Disable, as well as the configuration of feeds.
The solid lines in the diagram are for control flow and the dotted lines are for data flow. For example, the UI communicates with the TI Engine to fetch and push IoCs, and for other operations, such as import and export of IoCs.
All the feeds run periodically to push IoCs. The interval period is configurable for Premium and Custom feeds.
The IOCs from the feeds are used in the enrichment of Stellar Cyber's Interflow records, such as for reputation.