Stellar Cyber Overview
![]() Learn more at Stellar Cyber Academy.
Learn more at Stellar Cyber Academy.
The following link takes you to a course on the Stellar Cyber Academy technical training portal where you can learn more about this topic by watching the suggested lessons.
(2024) SOC ANALYST - Intro to Features In Stellar Cyber UI (02h:24m)
Familiarize yourself with the main features and layout of the Stellar Cyber Platform UI, focusing on essential tools for security investigations. Understand how to navigate and leverage views such as Case Management and Threat Hunting to streamline your analysis workflow.
Learn to use Case views, including the Top Cases, Case Table, and Kill Chain views, to prioritize and manage investigations. Explore how Stellar Cyber automatically correlates related events into cases, enhancing efficiency and providing a comprehensive picture for triaging high-risk incidents.
Watch a demonstration on interacting with cases in the Stellar Cyber UI. Learn to filter, sort, and explore cases, focusing on using the Top Cases view and other filtering options to facilitate investigation workflows.
See how to investigate a case using the UI tools in Stellar Cyber, including detailed analysis options and visualizations. Learn how to track the progression of an attack across different kill chain stages and use available resources to gain insights into security incidents.
Explore the Alerts view, learning how to filter, sort, and manage alerts within the Stellar Cyber Platform. Understand how machine learning drives alert generation and prioritization, and how to use these alerts to create custom cases.
Review available views for managing alerts, including the Alerts Table and Threat Hunting view. Learn to leverage MITRE ATT&CK data and custom filtering options to enhance your threat investigation and tune alert settings for focused analysis.
Watch a demonstration on triaging and investigating alerts in different views, including the Kill Chain and Alerts Table views. See how to interact with alerts, apply filters, and conduct threat-hunting activities efficiently.
Discover techniques for using the Threat Hunting view to identify and investigate unknown threats in your network. Learn how to filter data by entity and behavior, and leverage visualizations to enhance threat detection and analysis.
Dive into the User Behavior and Asset Analytics tools in the Stellar Cyber UI to add context to your investigations. Understand how to assess user activity and analyze assets for behavioral anomalies to support threat detection.
Follow a demonstration on using behavioral analytics to monitor user activity and asset interactions. Learn to investigate unusual behavior patterns and leverage data insights to enhance security operations.
The first time you access a link on the portal during a session, you must log in to access content.
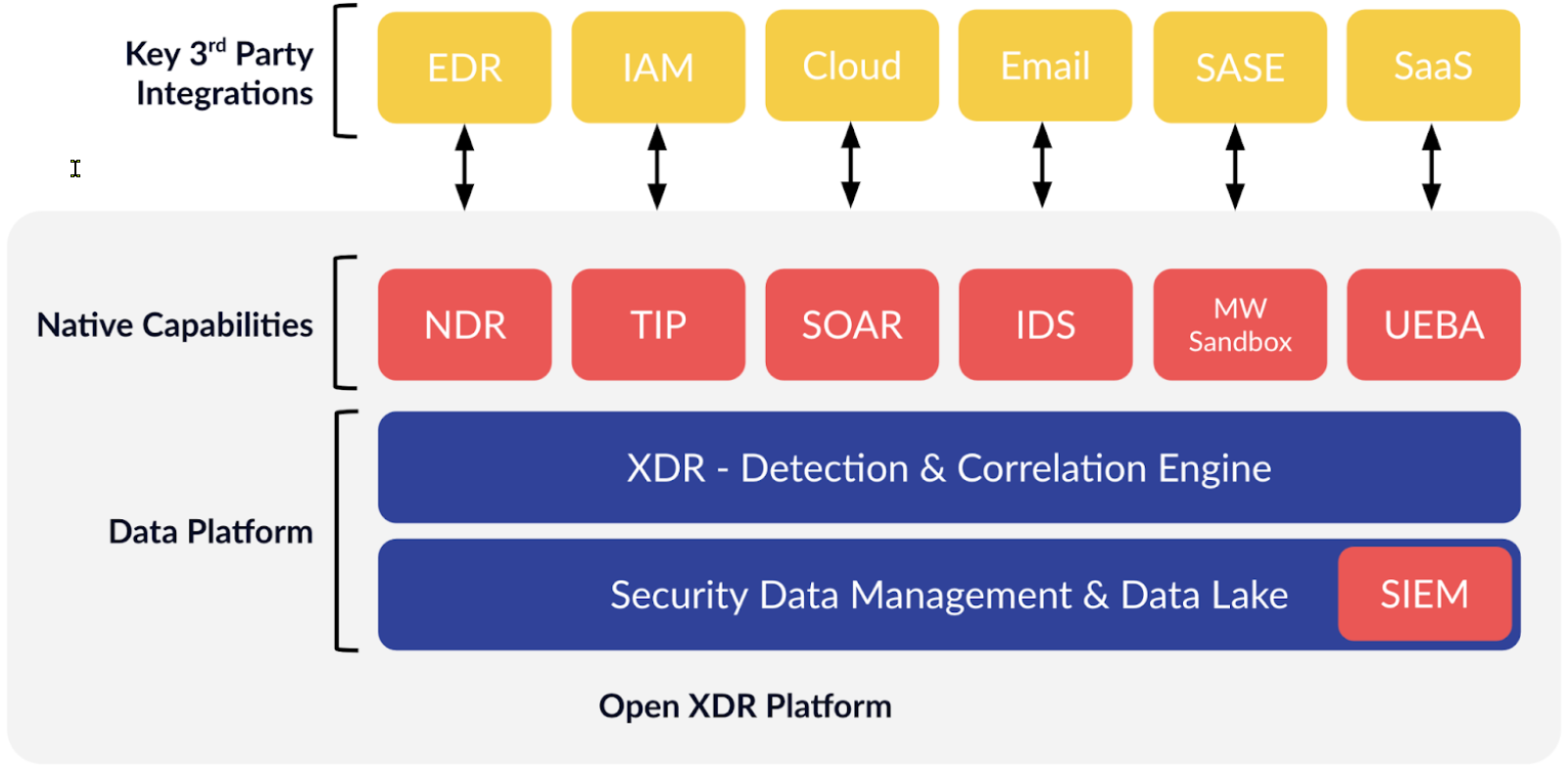
Stellar Cyber Open XDR is a platform for performing end-to-end threat detection and response, combining multiple capabilities – NG-SIEM, NDR, TIP, IDS, SOAR, and UEBA – into a single user experience.
Stellar Cyber allows security teams to gain full visibility into their IT, OT, and security environments, with turnkey automated detection and response across all data sources. This allows security teams to detect more alerts faster, future-proof their Security Operations, and free up human resources for more proactive security work.
Architecture Overview
Stellar Cyber is built on a Security Data Lake and a Detection and Correlation Engine. These are the platform components that allow collection from any source, detection on any source, and correlation across any sources. Additional native capabilities are built into the platform to provide comprehensive detection and response.
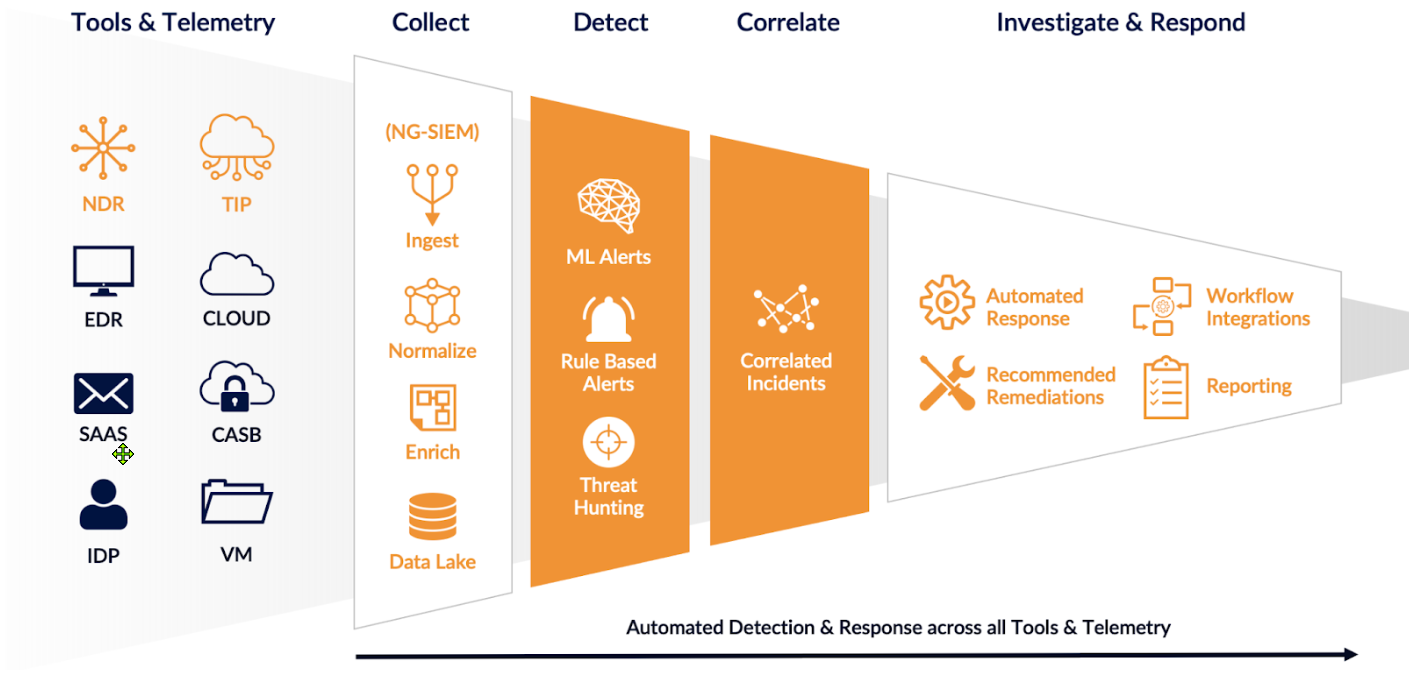
Data is collected, normalized, enriched, detected, and correlated across all sources. Data can be collected from API-based connector and log sources or Stellar Cyber sensors can be used to create visibility. Normalization and enrichment happens across all data, either at the edge (sensors) or centrally. Finally, detections based on both Machine Learning and Rules reveal threats and send the results to the correlation engine for automated investigation. The figure below illustrates the high level data flow in Stellar Cyber:
You can find more details on the architecture in Stellar Cyber Architecture.
Benefits
-
Get immediate time to value through integrations, detections, and correlations that work straight out of the box.
-
Implement best practices by getting immediate broad detection coverage and data source collection profiles.
-
Automate manual workflows with a data and automation pipeline that spans collection, detection, correlation, and response.
-
Future-proof your IT and security investments through Open XDR, integrations, and normalization across any data source.
-
Improve analyst efficiency by operating out of a platform that combines multiple capabilities into a single user experience.
Key Features
-
Automatic Case Correlation: Native, third-party, and custom alerts are correlated together into Cases, automating investigations and providing immediate context.
-
Multi-Modal Detections: Unsupervised ML, Supervised ML, rules, and edge detections (for example, IDS).
-
Simplified Data Collection: Hundreds of built-in integrations with the ability to collect from on-premise or cloud-based sources.
-
Native Sensors: Network-based device and server sensors create visibility across all environments, collect log sources, and run IDS and Malware Sandbox at the edge.
-
Response: Bi-directional integrations to IT and security products take automated or manual actions directly from Stellar Cyber.
-
Multi-Tenancy: Logical partitioning of tenants within a single customer instance for MSSPs or business unit separation.
Getting Started
The Getting Started Guide provides an overview of how to use the Knowledge Base and quick starts for both Analysts and Administrators.