|
Abnormal Security
(abnormal_security_threat)
|
| email.message_id |
Message ID |
Unique identifier of the email |
| srcip |
Source IP |
Source IP address |
| email.recipient.addresses |
Recipient Address(es) |
All recipients of the email, including those in the 'To', 'CC' (carbon copy), and 'BCC' (blind carbon copy) fields. |
| email.to.addresses |
To Address(es) |
Primary intended recipients of the email. These are the email addresses explicitly listed in the 'To' field of the email. |
| email.from.address |
From Address |
Email address that appears in the 'From' field of the email. It is the address that the recipient sees as the sender of the email. |
| email.subject |
Email Subject |
Subject line of the email |
| abnormal_security.sentTime |
Sent Time |
Time the email was sent |
| abnormal_security.receivedTime |
Received Time |
Time the email was received |
| abnormal_security.attackStrategy |
Attack Strategy |
Strategy used in the attack |
| abnormal_security.attackType |
Attack Type |
Type of attack |
| abnormal_security.attackVector |
Attack Vector |
Vector used in the attack |
| abnormal_security.remediationStatus |
Remediation Status |
Status of the remediation |
| abnormal_security.autoRemediated |
Auto-Remediated |
Whether the email was auto-remediated or not |
| abnormal_security.summaryInsights |
Summary Insights |
Summary insights about the email |
| abnormal_security.urlCount |
URL Count |
Number of URLs in the email |
| abnormal_security.attachmentCount |
Attachment Count |
Number of attachments in the email |
| abnormal_security.abxPortalUrl |
ABX Portal URL |
URL to the ABX portal for more details |
| url_list |
URL List |
List of URLs in the email |
|
|
Acronis (Antimalware protection)
(acronis_cyber_protect)
|
| event.threat.name |
Alert Type |
Alert type |
| acronis_cyber_protect.details.threatName |
Acronis Threat Name |
Acronis threat name |
| event.category |
Alert Category |
Alert category |
| host.name |
Host Name |
Host name |
| event.severity_str |
Acronis Severity Level |
Acronis severity level |
| file.name |
File Name |
File name |
| file.path |
File Path |
File path |
| file.hash.sha1 |
File SHA1 |
File SHA1 |
| file.hash.md5 |
File MD5 |
File MD5 |
| file.hash.sha256 |
File SHA256 |
File SHA256 |
|
|
Acronis (EDR)
(acronis_cyber_protect)
|
| event.threat.name |
Alert Type |
Alert type |
| event.category |
Alert Category |
Alert category |
| host.name |
Host Name |
Host name |
| event.severity_str |
Acronis Severity Level |
Acronis severity level |
| acronis_cyber_protect.details.redirectLink |
Acronis Alert Redirect Link |
Acronis alert redirect link |
| acronis_cyber_protect.details.verdict |
Acronis Alert Verdict |
Acronis alert verdict |
|
|
Acronis (Email security)
(acronis_cyber_protect)
|
| event.threat.name |
Alert Type |
Alert type |
| event.category |
Alert Category |
Alert category |
| event.severity_str |
Acronis Severity Level |
Acronis severity level |
| email.from.address |
Email From Address |
Email from address |
| email.subject |
Email Subject |
Email Subject |
|
|
Acronis (URL filtering)
(acronis_cyber_protect)
|
| event.threat.name |
Alert Type |
Alert type |
| acronis_cyber_protect.details.threatName |
Acronis Threat Name |
Acronis threat name |
| event.category |
Alert Category |
Alert category |
| host.name |
Host Name |
Host name |
| event.severity_str |
Acronis Severity Level |
Acronis severity level |
| url |
URL |
URL |
| process.pid |
Process ID |
Process ID |
| process.executable |
Process Path |
Process path |
|
|
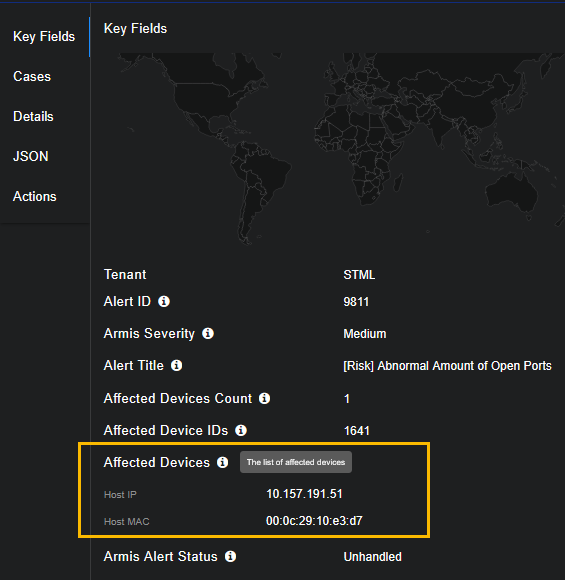
Armis
(armis)
|
| armis.alertId |
Alert ID |
Alert ID assigned by Armis |
| armis.severity |
Armis Severity |
Original severity from Armis |
| armis.title |
Alert Title |
Title of the alert |
| armis.policyTitle |
Policy Title |
Title of the policy that triggered the alert |
| armis.affectedDevicesCount |
Affected Devices Count |
Number of devices affected by the alert |
| armis.deviceIds |
Affected Device IDs |
IDs of the affected devices |
| host_list |
Affected Devices |
List of affected devices |
| ip |
Host IP |
Host IP address |
| mac |
Host MAC |
Host MAC address |
| armis.status |
Armis Alert Status |
Current status of the alert from Armis |
|
|
Avanan (Delivered)
(avanan) 
|
| email.from.address |
From Address |
Who the email is from |
| email.to.addresses |
To Address(es) |
Primary intended recipient of the email |
| email.sender.address |
Sender Address |
Who actually sent the email on behalf of the primary sender |
| email.recipient.addresses |
Recipient Address(es) |
Who received the email (including CC and BCC) |
| email.subject |
Email Subject |
Email subject |
| url_list |
URL List |
URL(s) in the email |
| domain_list |
Email Links Domain(s) |
Email links domain(s) |
| file_list |
File List |
File name of the malicious file |
| name |
File Name |
File name |
| hash.md5 |
Host Hash |
File hash |
| threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
Avanan (Quarantined)
(avanan) 
|
| email.from.address |
From Address |
Who the email is from |
| email.to.addresses |
To Address(es) |
Primary intended recipient of the email |
| email.sender.address |
Sender Address |
Who actually sent the email on behalf of the primary sender |
| email.recipient.addresses |
Recipient Address(es) |
Who received the email (including CC and BCC) |
| email.subject |
Email Subject |
Email subject |
| url_list |
URL List |
URL(s) in the email |
| domain_list |
Email Links Domain(s) |
Email links domain(s) |
| file_list |
File List |
File name of the malicious file |
| name |
File Name |
File name |
| hash.md5 |
Host Hash |
File hash |
| threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
AWS GuardDuty
(aws_guardduty)
|
| aws_guardduty.Title |
Alert Title |
AWS GuardDuty alert title |
| host_list |
Host IP Address(es) |
Private IP addresses of the network interfaces of the resource instance |
| user.name |
User Name |
User name associated with the access key details of the resource |
| event.threat.name |
Threat Name |
Threat name |
| event.severity |
AWS GuardDuty Severity Score |
AWS GuardDuty severity score |
| cloud.resource.type |
Cloud Resource Type |
Cloud resource type |
| cloud.resource.id |
Cloud Resource ID |
Cloud resource ID |
| cloud.resource.name |
Cloud Resource Name |
Cloud resource name |
|
|
Bitdefender IP
(bitdefender_ip)
|
| host.name |
Host Name |
Host name |
| host.ip |
Host IP Address |
Host IP address |
| srcip |
Source IP |
Source IP address |
|
|
Bitdefender Threat
(bitdefender_threat)
|
| host.name |
Host Name |
Host name |
| host.ip |
Host IP Address |
Host IP address |
| event.threat.name |
Threat Type |
Threat type |
|
|
Bitdefender URL
(bitdefender_url)
|
| host.name |
Host Name |
Host name |
| host.ip |
Host IP Address |
Host IP address |
| url |
URL |
URL |
|
|
Blackberry CylancePROTECT
(cylance_protect)
|
| host.name |
Host Name |
Computer name |
| host.ip |
Host IP Address |
Host IP address |
| file_name |
File Name |
File name |
| file_path |
File Path |
File path |
| process_name |
Process Name |
Process name |
|
|
Broadcom SES Incident
(broadcom_ses)
|
| event.severity |
Broadcom SES Severity |
Original severity from Broadcom SES |
| broadcom.incident_uid |
Broadcom SES Incident ID |
Unique identifier for the Broadcom SES incident |
| broadcom.events |
Event List |
User activities and process executions detected in this incident |
| device_name |
Device Name |
Device name |
| device_ip |
Device IP |
Device IP address |
| user.name |
User Name |
User name |
| process.pid |
Process ID |
Process ID |
| process.file.path |
Process Path |
Process path |
| process.file.name |
Process Name |
Process name |
| process.file.sha1 |
File SHA1 Hash |
SHA1 hash of the malicious file |
| process.file.md5 |
File MD5 Hash |
MD5 hash of the malicious file |
| process.file.sha2 |
File SHA256 Hash |
SHA256 hash of the malicious file |
| parent.pid |
Parent Process ID |
Parent process ID |
| parent.file.path |
Parent Process Path |
Parent process path |
| parent.file.sha1 |
Parent File SHA1 Hash |
SHA1 hash of the parent file |
| parent.file.sha2 |
Parent File SHA256 Hash |
SHA256 hash of the parent file |
| parent.file.md5 |
Parent File MD5 Hash |
MD5 hash of the parent file |
| file.name |
File Name |
File name |
| process_list |
Process Threat Intelligence |
Threat intelligence information for processes |
| threat_indicator.labels |
Threat Labels |
Threat intelligence labels for this process hash |
| threat_indicator.sources |
Threat Sources |
Threat intelligence sources that identified this process hash |
| parent.threat_indicator.labels |
Parent Threat Labels |
Threat intelligence labels for the parent process hash |
| parent.threat_indicator.sources |
Parent Threat Sources |
Threat intelligence sources that identified the parent process hash |
|
|
CrowdStrike
(crowdstrike)
|
| host.name |
Computer Name |
Computer name |
| hostip |
Host IP Address |
Host IP address |
| user.name |
User Name |
User name |
| file.name |
File Name |
File name |
| file.path |
File Path |
File path |
| process.command_line |
Command Line |
Command line |
|
|
Cybereason
(cybereason)
|
| user_list |
User Names |
User names |
| file.name |
File Name |
File name |
| process.name |
Process Name |
Process name |
| host_list |
Host IP Address(es) |
Host IP address(es) |
|
|
Cynet
(cynet)
|
| host.ip |
Host IP Address |
Host IP address |
| event.threat.name |
Threat Name |
Event threat name |
| file.name |
File Name |
File name |
|
|
Deep Instinct
(deepinstinct)
|
| deep_instinct.msp_name |
MSP Name |
MSP name |
| event.id |
Event ID |
Event ID |
| deep_instinct.type |
Type |
Deep Instinct event type |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP Address |
Host IP address |
| file.path |
File Path |
File path |
| file.file_hash |
File Hash |
File hash |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
| deep_instinct.action |
Event Action |
Deep Instinct event action |
| deep_instinct.threat_type |
Deep Instinct Threat Type |
Deep Instinct threat type |
| event.severity_str |
Original Deep Instinct Severity |
Original Deep Instinct severity |
|
|
ESET Cloud Office Security
(eset_cloud_office_security)
|
| eset.Tenant |
ESET Tenant |
ESET Cloud Office Security tenant name |
| eset.OperationId |
ESET Operation ID |
ESET Cloud Office Security operation ID |
| eset.ScanResult |
ESET Threat Type |
ESET Cloud Office Security threat type |
| eset.Action |
ESET Event Action |
ESET Cloud Office Security event action |
| file.name |
File Name |
File name |
| file.hash.sha1 |
File SHA1 Hash |
SHA1 hash of the malicious file |
| srcip |
Source IP |
Email sender source IP address |
| email.from.address |
Sender Address |
Sender IP address |
| email.to.addresses |
Recipient Address(es) |
Recipient IP address(es) |
| email.subject |
Email Subject |
Email subject |
|
|
ESET Protect
(eset_protect_filtered_websites_event)
|
| srcip |
Source IP |
Source IP address |
| dstip |
Destination IP |
Destination IP address |
| eset.rule_id |
ESET Protect Rule ID |
ESET Protect rule ID |
| eset.event_type |
ESET Protect Event Type |
ESET Protect event type |
| event.severity_str |
ESET Protect Event Severity |
ESET Protect event severity |
| event.threat.name |
ESET Protect Threat Name |
ESET Protect threat name |
| process.executable |
Process Path |
Process path |
| user.name |
User Name |
User name |
| host.name |
Host Name |
Host name |
| file.hash.sha1 |
File SHA1 Hash |
File SHA1 hash |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
ESET Protect
(eset_protect_firewall_aggregated_event)
|
| srcip |
Source IP |
Source IP address |
| dstip |
Destination IP |
Destination IP address |
| eset.event_type |
ESET Protect Event Type |
ESET Protect event type |
| event.severity_str |
ESET Protect Event Severity |
ESET Protect event severity |
| event.threat.name |
ESET Protect Threat Name |
ESET Protect threat name |
| process.executable |
Process Path |
Process path |
| user.name |
User Name |
User name |
|
|
ESET Protect
(eset_protect_inspect_alert)
|
| host.ip |
Host IP |
Host IP address |
| host.name |
Host Name |
Host name |
| eset.event_type |
ESET Protect Event Type |
ESET Protect event type |
| eset.rulename |
ESET Protect Rule Name |
ESET Protect rule name |
| process.executable |
Process Path |
Process path |
| user.name |
User Name |
User name |
| event.severity_str |
ESET Protect Event Severity |
ESET Protect event severity |
| eset.eiconsolelink |
ESET Protect Console Link |
ESET Protect console link |
| eset.source_uuid |
ESET Protect Source UUID |
ESET Protect source UUID |
| file.hash.sha1 |
File SHA1 Hash |
File SHA1 hash |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File Hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File Hash reputation source(s) |
|
|
ESET Protect
(eset_protect_threat_event)
|
| host.ip |
Host IP |
Host IP address |
| host.name |
Host Name |
Host name |
| eset.event_type |
ESET Protect Event Type |
ESET Protect event type |
| process.executable |
Process Path |
Process path |
| user.name |
User Name |
User name |
| event.severity_str |
ESET Protect Event Severity |
ESET Protect event severity |
| eset.source_uuid |
ESET Protect Source UUID |
ESET Protect source UUID |
| file.hash.sha1 |
File SHA1 Hash |
File SHA1 hash |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File Hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File Hash reputation source(s) |
|
|
Fortinet Lacework
(laceworkt)
|
| fortinet_lacework.START_TIME |
Start Time |
Time and date when the hourly aggregation time period starts |
| fortinet_lacework.END_TIME |
End Time |
Time and date when the hourly aggregation time period ends |
| event.threat.name |
Alert Type |
Type of the alert |
| fortinet_lacework.EVENT_ID |
Event ID |
Unique identifier generated for this event by Lacework FortiCNAPP |
| fortinet_lacework.EVENT_MODEL |
Event Model |
Data model used for generating the alert |
| fortinet_lacework.EVENT_ACTOR |
Event Actor |
Event actor that categorizes the type of an alert such as application, process, files, etc |
| fortinet_lacework.ENTITY_MAP.User |
User(s) |
User(s) |
| KEY.username |
User Name |
User's name |
| PROPS.hostname |
Host Name |
User's host name |
| fortinet_lacework.ENTITY_MAP.CT_User |
CloudTrail User(s) |
CloudTrail user(s) |
| KEY.username |
User Name |
User's name |
| PROPS.account |
User Account |
User's account |
| fortinet_lacework.ENTITY_MAP.SourceIpAddress |
Source IP Address(es) |
Source IP address(es) |
| KEY.ip_addr |
IP Address |
IP address |
| fortinet_lacework.ENTITY_MAP.FileExePath |
File Path(s) |
File path(s) |
| KEY.exe_path |
File Path |
File path |
| fortinet_lacework.ENTITY_MAP.Process |
Process(es) |
Process(es) |
| PROPS.hostname |
Host Name |
Host name |
| PROPS.cmdline |
Command Line |
Command line |
| PROPS.pid |
PID |
Unique identifier of the process |
| fortinet_lacework.ENTITY_MAP.Machine |
Machine(s) |
Machine(s) |
| PROPS.hostname |
Host Name |
Host name |
| PROPS.internal_ip_addr |
IP Address |
IP address |
|
|
Google Workspace Alert
(google_workspace_alert)
|
| source |
Alert Source |
Alert source
|
| type |
Alert Type |
Alert type |
| rule.name |
Rule Name |
Alert rule name |
| host.ip |
Login IP Address |
IP address associated with the warning event |
| data.email |
Data Email |
Email of the user to which this event belongs |
| securityInvestigationToolLink |
Investigation Tool Link |
Google Workspace security investigation tool link |
| user.id |
User ID |
User ID |
| user.name |
User Name |
User name |
| email.from.address |
Email From Address |
Email from IP address |
| email.recipient.addresses |
Email Recipient Addresses |
Email recipient addresses |
|
|
Huntress
(huntress_incident)
|
| huntress.organization_name |
Organization Name |
Huntress organization name |
| huntress.security_products |
Originating Security Products |
Originating security products |
| huntress.incident_report_url |
Incident Report URL |
Huntress incident report URL |
| huntress.user_url |
User URL |
Huntress user URL |
| huntress.host_url |
Host URL |
Huntress host URL |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| user_name |
User Name |
User name |
| event.threat_list |
Huntress Event Threat List |
Huntress event threat list |
| name |
Threat Name |
Huntress Event Threat Name |
| severity |
Threat Severity |
Huntress Event Threat Severity |
|
|
HYAS Protect
(hyas_protect_block) 
|
| srcip |
Client IP |
Client IP address |
| dns.question.name |
Domain |
Domain |
| hyas_protect.registrar |
Domain Registrar |
Domain registrar |
| domain_creation |
Domain Creation Date |
Domain creation date |
| hyas_protect.verdictStatus |
HYAS Protect Verdict Status |
HYAS Protect verdict status:
-
Allow: allow
-
Block: block
-
Highly Suspicious: bad
-
Watch Engine: suspicious
|
| hyas_protect.reason.type |
HYAS Protect Reason Type |
HYAS Protect reason type |
| hyas_protect.reason.lists |
HYAS Protect Reason Lists |
HYAS Protect reason lists |
| id |
ID |
Reason ID |
| name |
Name |
Reason name |
| datatype |
Datatype |
Reason data type |
| dns.resolved_ip |
Resolved IP(s) |
Resolved IP address(es) |
| dns.answers |
DNS Answer(s) |
DNS answer(s) |
| name |
Domain name |
Domain name to which this resource record pertains. If a chain of CNAME is being resolved, each answer’s name should be the one that corresponds with the answer’s data. |
| type |
Data Type |
Type of data contained in this resource record |
| data |
Data |
Data in this resource record |
|
|
HYAS Protect
(hyas_protect_bad) 
|
| srcip |
Client IP |
Client IP address |
| dns.question.name |
Domain |
Domain |
| hyas_protect.registrar |
Domain Registrar |
Domain registrar |
| domain_creation |
Domain Creation Date |
Domain creation date |
| hyas_protect.verdictStatus |
HYAS Protect Verdict Status |
HYAS Protect verdict status:
-
Allow: allow
-
Block: block
-
Highly Suspicious: bad
-
Watch Engine: suspicious
|
| hyas_protect.reason.type |
HYAS Protect Reason Type |
HYAS Protect reason type |
| hyas_protect.reason.lists |
HYAS Protect Reason Lists |
HYAS Protect reason lists |
| id |
ID |
Reason ID |
| name |
Name |
Reason name |
| datatype |
Datatype |
Reason data type |
| dns.resolved_ip |
Resolved IP(s) |
Resolved IP address(es) |
| dns.answers |
DNS Answer(s) |
DNS answer(s) |
| name |
Domain name |
Domain name to which this resource record pertains. If a chain of CNAME is being resolved, each answer’s name should be the one that corresponds with the answer’s data. |
| type |
Data Type |
Type of data contained in this resource record |
| data |
Data |
Data in this resource record |
|
|
HYAS Protect
(hyas_protect_suspicious) 
|
| srcip |
Client IP |
Client IP address |
| dns.question.name |
Domain |
Domain |
| hyas_protect.registrar |
Domain Registrar |
Domain registrar |
| domain_creation |
Domain Creation Date |
Domain creation date |
| hyas_protect.verdictStatus |
HYAS Protect Verdict Status |
HYAS Protect verdict status:
-
Allow: allow
-
Block: block
-
Highly Suspicious: bad
-
Watch Engine: suspicious
|
| hyas_protect.reason.type |
HYAS Protect Reason Type |
HYAS Protect reason type |
| hyas_protect.reason.lists |
HYAS Protect Reason Lists |
HYAS Protect reason lists |
| id |
ID |
Reason ID |
| name |
Name |
Reason name |
| datatype |
Datatype |
Reason data type |
| dns.resolved_ip |
Resolved IP(s) |
Resolved IP address(es) |
| dns.answers |
DNS Answer(s) |
DNS answer(s) |
| name |
Domain name |
Domain name to which this resource record pertains. If a chain of CNAME is being resolved, each answer’s name should be the one that corresponds with the answer’s data. |
| type |
Data Type |
Type of data contained in this resource record |
| data |
Data |
Data in this resource record |
|
|
LimaCharlie Events
(limacharlie_alert)
|
| srcip_host |
Source Host |
Name of the workstation |
| srcip |
Source IP |
IP address of the source |
| srcport |
Source IP Port |
Port of the source IP address |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| limacharlie.detect.event.ACTION |
Action |
Event action |
| limacharlie.detect.event.REGISTRY_KEY |
Registry Key |
Registry key |
| limacharlie.detect.event.REGISTRY_VALUE |
Registry Value |
Registry value |
| process.name |
Process File Path |
File path of the process |
| process.hash.sha256 |
Process File Hash |
File hash of the process |
| process.threat_indicator.labels |
Process File Hash Reputation Label(s) |
Process file hash reputation label(s) |
| process.threat_indicator.sources |
Process File Hash Reputation Source(s) |
Process file hash reputation source(s) |
| event.severity_str |
LimaCharlie Severity |
Original severity of the LimaCharlie alert |
| limacharlie.detect.event.EVENT.EventData.TargetUserSid |
SID |
SID of the target user |
| file.path |
File Path |
Path of the file |
| file.hash.sha256 |
File Hash |
SHA256 hash of the file |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
| process.command_line |
Process Command Line |
Command line of the process |
| process.pid |
Process ID |
Process ID |
| user.name |
User Name |
User name |
| limacharlie.detect.event.EVENT.System.EventID |
Event ID |
Event ID |
| limacharlie.detect.event.EVENT.EventData.LogonType |
Logon Type |
Logon type |
| limacharlie.detect.event.EVENT.EventData.ProcessName |
Process Name |
Process name |
| limacharlie.detect.event.PARENT.FILE_PATH |
Parent Process File Path |
File path of the parent process |
| limacharlie.detect.event.PARENT.HASH |
Parent Process File Hash |
File hash of the parent process |
| process.parent.threat_indicator.labels |
Parent Process File Hash Reputation Label(s) |
Reputation label(s) of the parent process file hash |
| process.parent.threat_indicator.sources |
Parent Process File Hash Reputation Source(s) |
Reputation source(s) of the parent process file hash |
| process.parent.command_line |
Parent Process Command Line |
Command line of the parent process |
| process.parent.pid |
Parent Process ID |
Parent process ID |
| limacharlie.detect.event.PARENT.USER_NAME |
Parent User Name |
User name of the parent process |
| limacharlie.link |
LimaCharlie Alert Link |
LimaCharlie alert link |
| limacharlie.source_rule |
Source Rule |
Source rule that LimaCharlie used to generate the alert |
| limacharlie.detect_mtd.references |
Rule References |
References of the rule |
|
|
Microsoft Defender for Endpoint
(ms_defender_atp)
|
| host.name |
Host Name |
Host name |
| host.ip |
Host IP Address |
Host IP address |
| user.name |
User Name |
User name |
| user.domain |
User Domain |
User domain |
| threat |
Threat Name |
Threat name |
| file_list |
File List |
File list |
| process_list |
Process List |
Process list |
|
|
Microsoft Entra ID (formerly Azure Active Directory)
(azure_ad_risk_detection)
|
| userDisplayName |
User Name |
User name |
| ipAddress |
Host IP Address |
Host IP address |
| riskEventType |
Event Type |
Risk event type |
|
|
Microsoft Defender for Cloud
(microsoft_defender_cloud)
|
| microsoft_defender_cloud.AlertUri |
Microsoft Defender for Cloud Alert URI |
Microsoft Defender for Cloud alert URI |
| event.severity_str |
Microsoft Defender for Cloud Severity |
Original severity from Microsoft Defender for Cloud |
| microsoft_defender_cloud.AlertDisplayName |
Microsoft Defender for Cloud Alert Name |
Microsoft Defender for Cloud alert name |
| cloud.resource.name |
Cloud Resource Name |
Cloud resource name |
| cloud.resource.type |
Cloud Resource Type |
Cloud resource type |
| cloud.resource.id |
Cloud Resource ID |
Cloud resource ID |
| srcip_list |
Source IP List |
Source IP address list |
| srcip |
Source IP |
Source IP address |
| user.name |
User Name |
User name |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP Address |
Host IP address |
| file.name |
File Name |
File name |
| file.path |
File Path |
File path |
| file.hash.md5 |
File MD5 Hash |
File MD5 hash |
| file.hash.sha256 |
File SHA256 Hash |
File SHA256 hash |
| process.executable |
Process Executable |
Process executable |
| process.id |
Process ID |
Process ID |
| process.command_line |
Process Command Line |
Process command line |
| process.parent.name |
Parent Process Name |
Parent process name |
| process.parent.executable |
Parent Process Executable |
Parent process executable |
| process.parent.id |
Parent Process ID |
Parent process ID |
| process.parent.command_line |
Parent Process Command Line |
Parent process command line |
| microsoft_defender_cloud.ExtendedProperties |
Extended Properties |
Extended properties |
| microsoft_defender_cloud.ExtendedProperties.Potential causes |
Potential Causes |
Potential causes |
| microsoft_defender_cloud.ExtendedProperties.Recommended actions |
Recommended Actions |
Recommended actions |
| microsoft_defender_cloud.ExtendedProperties.Event of Interest |
Event of Interest |
Event of interest |
| microsoft_defender_cloud.RemediationSteps |
Remediation Steps |
Remediation steps |
|
|
Microsoft Defender for Cloud Apps
(ms_defender_for_cloud_apps) 
|
| microsoft_defender_for_cloud_apps.URL |
Microsoft Defender for Cloud Apps URL |
Microsoft Defender for Cloud Apps URL |
| event.threat_list |
Risk category |
Threat list |
| name |
Risk category |
Microsoft Defender for Cloud Apps risk category |
| event.severity_str |
Microsoft Defender for Cloud Apps Severity |
Original severity value from Microsoft Defender for Cloud Apps |
| microsoft_defender_for_cloud_apps.isPreview |
Preview |
Alerts that have been recently released as GA |
| user.id |
User ID |
User ID of entity that was involved in this alert |
| user.name |
Username |
Username of entity that was involved in this alert |
| srcip |
Source IP Address |
Source IP address of attack that was involved in this alert |
| srcip_host |
Source Host |
Name of the source workstation involved in this alert |
| dstip_host |
Destination Host |
Name of the destination workstation involved in this alert |
| observables |
Entities |
List of observables related to the alert |
| name |
Entity name |
Entity name |
| type |
Entity type |
Entity type |
| id |
Entity ID |
Entity ID |
|
|
Microsoft Defender XDR
(microsoft_defender_xdr)
|
| event.severity_str |
Severity |
Alert severity |
| event.threat.name |
Threat Name |
Threat name |
| microsoft_graph_security_api.evidence |
Evidence |
Evidence |
| type |
Type |
Evidence type |
| userAccount.userPrincipalName |
User Name |
User's name |
| userAccount.azureAdUserId |
User ID |
User's ID |
| fileDetails.fileName |
File Name |
File name |
| fileDetails.filePath |
File Path |
File path |
| fileDetails.sha256 |
SHA256 |
SHA256 hash |
| fileDetails.md5 |
MD5 |
MD5 hash |
| fileDetails.sha1 |
SHA1 |
SHA1 hash |
| hostName |
Host Name |
Host name |
| ipInterfaces |
IP Interfaces |
IP interfaces of the device during the time of the alert |
| ipAddress |
IP Address |
IP address |
|
|
Microsoft Office 365
(microsoft_365)
|
| event.threat.name |
Threat Name |
Threat name |
| event.severity_str |
Microsoft 365 Severity Level |
Microsoft 365 severity level |
| event.category |
Category |
Microsoft 365 alert category |
| Source |
Source |
Microsoft 365 alert source |
| AlertType |
Alert Type |
Microsoft 365 alert type
|
| event_summary.alert_entity_list |
Alert Entity List |
Microsoft 365 Alert entity list |
| username |
User Name |
User name |
|
|
Microsoft Sentinel
(ms_sentinel_incident)
|
| microsoft_sentinel.Title |
Incident Title |
Microsoft Sentinel incident title |
| microsoft_sentinel.ModifiedBy |
Modified By |
Microsoft Sentinel modified by |
| microsoft_sentinel.AdditionalData.alertsCount |
Alerts Count |
Microsoft Sentinel additional data alerts count |
| microsoft_sentinel.IncidentUrl |
Incident Link |
Microsoft Sentinel incident link |
| microsoft_sentinel.SourceSystem |
Source System |
Microsoft Sentinel source system |
| microsoft_sentinel.AlertIds |
Alert IDs |
Microsoft Sentinel alert IDs |
|
|
Mimecast Attachment Protect
(mimecast_attachment_protect)
Mimecast API 1.0
|
| srcip |
Source IP Address |
Source IP address of the original message that contained the malicious file |
| file.name |
File Name |
File name of the malicious file |
| mimecast.fileExt |
File Extension |
File extension of the malicious file |
| mimecast.Size |
File Size |
Size (in bytes) of the malicious file |
| mimecast.sizeAttachment |
File Size |
Size (in bytes) of the malicious file |
| file.hash.md5 |
File MD5 Hash |
MD5 hash of the malicious file |
| file.hash.sha1 |
File SHA1 Hash |
SHA1 hash of the malicious file |
| file.hash.sha256 |
File SHA256 Hash |
SHA256 hash of the malicious file |
| mimecast.fileMime |
File MIME Type |
Detected MIME type of the malicious file |
| email.sender.address |
Sender Address |
Sender address |
| email.recipient.addresses |
Recipient Address(es) |
Recipient address(es) |
| email.subject |
Email Subject |
Email subject |
| mimecast.senderDomain |
Sender Domain |
Sender domain |
| mimecast.Route |
The Route of the Message |
Route of the message |
| mimecast.route |
The Route of the Message |
Route of the message |
|
|
Mimecast AV
(mimecast_av)
Mimecast API 1.0
|
| srcip |
Source IP Address |
Source IP address of the original message |
| file.name |
File Name |
File name |
| mimecast.fileExt |
File Extension |
File extension |
| mimecast.fileExtension |
File Extension |
File extension |
| mimecast.Size |
Email Size |
Total size of the email |
| mimecast.emailSize |
Email Size |
Total size of the email |
| file.hash.md5 |
File MD5 Hash |
File MD5 hash |
| file.hash.sha1 |
File SHA1 Hash |
File SHA1 hash |
| file.hash.sha256 |
File SHA256 Hash |
File SHA256 hash |
| mimecast.fileMime |
File MIME Type |
File MIME type |
| email.sender.address |
Sender Address |
Sender address |
| mimecast.senderDomain |
Sender Domain |
Sender domain |
| email.recipient.addresses |
Recipient Address(es) |
Recipient address(es) |
| email.subject |
Email Subject |
Email subject |
| mimecast.Route |
The Route of the Message |
Route of the message |
| mimecast.route |
The Route of the Message |
Route of the message |
| mimecast.Virus |
Virus Signature |
Virus signature |
| mimecast.virusFound |
Virus Signature |
Virus signature |
|
|
Mimecast Impersonation Protect
(mimecast_email_impersonation_protect)
Mimecast API 1.0
Mimecast API 2.0
|
| mimecast.aCode |
Mimecast aCode |
Unique ID used to track the email through the different log types from Mimecast |
| srcip |
Source IP Address |
Source IP address of the original message |
| email.sender.address |
Sender Address |
Sender address |
| email.recipient.addresses |
Recipient Address(es) |
Recipient address(es) |
| email.subject |
Email Subject |
Email subject |
| event.threat.name |
Alert Definition |
Alert definition |
| mimecast.Hits |
Number of Items Flagged |
Number of items flagged for the message |
| mimecast.Route |
The Route of the Message |
Route of the message |
|
|
Mimecast Internal Email Protect
(mimecast_internal_email_protect)
Mimecast API 1.0
Mimecast API 2.0
|
|
mimecast.aCode
|
Mimecast aCode |
Unique ID used to track the email through the different log types from Mimecast |
|
mimecast.processingId
|
Mimecast aCode |
Unique ID used to track the email through the different log types from Mimecast |
| srcip |
Source IP Address |
Source IP address of the sending mail server |
| url |
Clicked URL |
URL the user clicked |
| event.threat.name |
URL Category |
URL category |
| email.sender.address |
Sender Address |
Sender address |
| email.recipient.addresses |
Recipient Address(es) |
Recipient address(es) |
| email.subject |
Email Subject |
Email subject |
| mimecast.Route |
The Route of the Message |
Route of the message |
|
|
Mimecast Malicious Receipt Log
(mimecast_receipt_with_virus)
Mimecast API 1.0
Mimecast API 2.0
|
|
mimecast.aCode
|
Mimecast aCode |
Unique ID used to track the email through the different log types from Mimecast |
|
mimecast.processingId
|
Mimecast aCode |
Unique ID used to track the email through the different log types from Mimecast |
| srcip |
Source IP Address |
Source IP address of the sending mail server |
| email.sender.address |
Sender Address |
Sender address |
| email.recipient.addresses |
Recipient Address(es) |
Recipient address(es) |
| email.subject |
Email Subject |
Email subject |
|
mimecast.Error
|
Errors Occurred |
Information about any errors that occurred during receipt |
|
mimecast.receiptErrors
|
Errors Occurred |
Information about any errors that occurred during receipt |
|
mimecast.Dir
|
Email Direction |
Direction of the email based on the sending and receiving domains |
|
mimecast.direction
|
Email Direction |
Direction of the email based on the sending and receiving domains |
|
mimecast.Virus
|
Virus Signature |
Virus signature |
|
mimecast.virusFound
|
Virus Signature |
Virus signature |
|
mimecast.Act
|
Action |
Action taken at the receipt stage |
|
mimecast.action
|
Action |
Action taken at the receipt stage |
|
mimecast.RejInfo
|
Rejection Information |
Rejection information if the email was rejected at the receipt stage |
|
mimecast.rejectionInfo
|
Rejection Information |
Rejection information if the email was rejected at the receipt stage |
|
mimecast.RejType
|
Rejection Type |
Rejection type if the email was rejected at the receipt stage |
|
mimecast.rejectionType
|
Rejection Type |
Rejection type if the email was rejected at the receipt stage |
|
mimecast.TlsVer
|
TLS Version |
TLS version used if the email was received using TLS |
|
mimecast.tlsVersion
|
TLS Version |
TLS version used if the email was received using TLS |
|
mimecast.Cphr
|
TLS Cipher |
TLS cipher used if the email was received using TLS |
|
mimecast.tlsCipher
|
TLS Cipher |
TLS cipher used if the email was received using TLS |
|
|
Mimecast URL Protect
(mimecast_url_protect)
Mimecast API 1.0
|
| srcip |
Source IP Address |
Source IP address of the sending mail server |
| url |
Clicked URL |
URL the user clicked |
| event.threat.name |
URL Category |
URL category |
| event.reason |
Reason |
Event reason |
| email.sender.address |
Sender Address |
Sender address |
| email.recipient.addresses |
Recipient Address(es) |
Recipient address(es) |
| email.subject |
Email Subject |
Email subject |
| mimecast.action |
Mimecast Action |
Mimecast action |
| mimecast.senderDomain |
Sender Domain |
Sender domain |
| mimecast.route |
The Route of the Message |
Route of the message |
|
|
Netskope Alert (Breach)
(netskope_protect_breach)
|
| netskopewsg.type |
Netskope Alert Type |
Netskope alert type |
| netskopewsg.breach_id |
Netskope Breach ID |
Netskope breach ID |
| netskopewsg.alert_name |
Alert Name |
Alert name |
| srcip |
Source IP |
Source IP address |
| dstip |
Destination IP |
Destination IP address |
| host.ip |
Host IP (User's IP) |
Host IP address (user's IP address) |
| user.name |
User Name |
User name associated with Netskope account |
| netskopewsg.matched_username |
Matched User Name |
Email address associated with the breached access method |
| url |
URL |
URL |
| event.severity_str |
Netskope Alert Severity |
Netskope alert severity |
| netskopewsg.breach_score |
Netskope Breach Score |
Netskope breach score |
| file.hash.sha256 |
File SHA256 Hash |
SHA256 hash of the file |
| file.hash.md5 |
File MD5 Hash |
MD5 hash of the file |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
Netskope Alert (Connection)
(netskope_protect_connection)
|
| netskopewsg.type |
Netskope Alert Type |
Netskope alert type |
| netskopewsg.connection_id |
Netskope Connection ID |
Netskope connection ID |
| srcip |
Source IP |
Source IP address |
| dstip |
Destination IP |
Destination IP address |
| host.ip |
Host IP (User's IP) |
Host IP address (user's IP address) |
| user.name |
User Name |
User name |
| url |
URL |
URL |
| event.severity_str |
Netskope Alert Severity |
Netskope alert severity |
| file.hash.sha256 |
File SHA256 Hash |
SHA256 hash of the file |
| file.hash.md5 |
File MD5 Hash |
MD5 hash of the file |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
Netskope Alert
(netskope_protect)
|
| netskopewsg.type |
Netskope Alert Type |
Netskope alert type |
| netskopewsg.breach_id |
Netskope Breach ID |
Netskope breach ID |
| netskopewsg.alert_name |
Alert Name |
Alert name |
| srcip |
Source IP |
Source IP address |
| dstip |
Destination IP |
Destination IP address |
| host.ip |
Host IP (User's IP) |
Host IP address (user's IP address) |
| host.name |
Host Name |
Host name |
| user.name |
User Name |
User name associated with Netskope account |
| netskopewsg.matched_username |
Matched User Name |
Email address associated with the breached access method |
| netskopewsg.activity |
Activity |
Activity |
| netskopewsg.action |
Action |
Action |
| netskopewsg.policy |
Policy Name |
Policy name |
| netskopewsg.app |
Application |
Application |
| url |
Application URL |
Application URL |
| event.severity_str |
Netskope Alert Severity |
Netskope alert severity |
| netskopewsg.breach_score |
Netskope Breach Score |
Netskope breach score |
| file.hash.sha256 |
File SHA256 Hash |
SHA256 hash of the file |
| file.hash.md5 |
File MD5 Hash |
MD5 hash of the file |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
Netskope Alert (Malsite)
(netskope_protect_malsite)
|
| netskopewsg.type |
Netskope Alert Type |
Netskope alert type |
| event.threat.name |
Malsite Category |
Malsite category |
| netskopewsg.malsite_id |
Malsite ID |
Malsite ID |
| srcip |
Source IP |
Source IP address |
| dstip |
Destination IP |
Destination IP address |
| host.ip |
Host IP (User's IP) |
Host IP address (user's IP address) |
| user.name |
User Name |
User name |
| url |
Malsite URL |
Malsite URL |
| event.severity_str |
Netskope Alert Severity |
Netskope alert severity |
| file.hash.sha256 |
File SHA256 Hash |
SHA256 hash of the file |
| file.hash.md5 |
File MD5 Hash |
MD5 hash of the file |
| file.threat_indicator.labels |
File Hash Reputation Label(s) |
File hash reputation label(s) |
| file.threat_indicator.sources |
File Hash Reputation Source(s) |
File hash reputation source(s) |
|
|
Oracle Cloud Infrastructure (OCI) CloudGuard
(oci_cloudguard)
|
| event.type |
Problem Type |
Problem type |
| event.threat.name |
Threat Name |
Threat name |
| event.severity_str |
OCI Severity Level |
OCI CloudGuard severity level |
| cloud.resource.type |
Cloud Resource Type |
Cloud resource type |
| cloud.resource.id |
Cloud Resource ID |
Cloud resource ID |
| cloud.resource.name |
Cloud Resource Name |
Cloud resource name |
| oracle.data.additionalDetails.problemRecommendation |
Problem Recommendation |
Problem recommendation from OCI |
|
|
Palo Alto Networks Cortex XDR(PAN NGFW)
(palo_alto_cortex_xdr_ngfw)
|
| palo_alto_networks.name |
Alert Name |
Alert name |
| palo_alto_networks.source |
Source |
Alert source |
| palo_alto_networks.category |
Category |
Alert category |
| event.severity_str |
Palo Alto Networks Cortex XDR Alert Severity |
Palo Alto Networks Cortex XDR alert severity |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| palo_alto_networks.alert_id |
Alert ID |
Alert ID |
| palo_alto_networks.action_pretty |
Action |
Action taken |
| palo_alto_networks.agent_version |
Agent Version |
Agent version |
| palo_alto_networks.resolution_status |
Status |
Resolution status |
| palo_alto_networks.events |
Network Events |
Network events |
| event_type |
Event Type |
Event type |
| fw_rule |
Rule Name |
Firewall rule name |
| fw_rule_id |
Rule ID |
Firewall rule ID |
| action_local_ip |
Local IP |
Local IP address |
| action_local_port |
Local Port |
Local port |
| action_remote_ip |
Remote IP |
Remote IP address |
| action_remote_port |
Remote Port |
Remote port |
| action_country |
Remote Country |
Remote country |
| dst_action_country |
Dest Country |
Destination country |
| fw_device_name |
Device Name |
Firewall device name |
| fw_serial_number |
Serial Number |
Firewall serial number |
| fw_interface_from |
From Interface |
From interface |
| fw_interface_to |
To Interface |
To interface |
| fw_app_id |
App ID |
Application ID |
| fw_app_category |
App Category |
App category |
| fw_app_subcategory |
App Subcategory |
App subcategory |
| fw_app_technology |
App Technology |
App technology |
|
|
Palo Alto Networks Cortex XDR(XDR Agent)
(palo_alto_cortex_xdr_agent)
|
| palo_alto_networks.name |
Alert Name |
Alert name |
| palo_alto_networks.source |
Source |
Alert source |
| palo_alto_networks.category |
Category |
Alert category |
| event.severity_str |
Palo Alto Networks Cortex XDR Alert Severity |
Palo Alto Networks Cortex XDR alert severity |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| palo_alto_networks.alert_id |
Alert ID |
Alert ID |
| palo_alto_networks.action_pretty |
Action |
Action taken |
| palo_alto_networks.agent_version |
Agent Version |
Agent version |
| palo_alto_networks.resolution_status |
Status |
Resolution status |
| palo_alto_networks.events |
Events |
Related events |
| event_type |
Event Type |
Event type |
| user_name |
User Name |
User name |
| action_process_image_name |
Action Process |
Action process |
| actor_process_image_name |
Actor Process |
Actor process |
| action_process_image_sha256 |
Process SHA256 |
Process SHA256 |
| actor_process_image_sha256 |
Actor SHA256 |
Actor process SHA256 |
| action_process_image_command_line |
Command Line |
Process command line |
| actor_process_command_line |
Actor Command Line |
Actor command line |
| actor_process_image_path |
Actor Process Path |
Actor process path |
| actor_process_image_md5 |
Actor MD5 Hash |
Actor process MD5 |
| actor_process_signature_vendor |
Actor Signature Vendor |
Actor process signature vendor |
| actor_process_signature_status |
Actor Signature Status |
Actor process signature status |
| actor_process_os_pid |
Actor Process PID |
Actor process PID |
| actor_thread_thread_id |
Actor Thread ID |
Actor thread ID |
| causality_actor_process_image_name |
Causality Actor Process Name |
Causality actor process name |
| causality_actor_process_image_path |
Causality Actor Process Path |
Causality actor process path |
| causality_actor_process_command_line |
Causality Actor Command Line |
Causality actor process command line |
| causality_actor_process_image_sha256 |
Causality Actor SHA256 |
Causality actor process SHA256 |
| causality_actor_process_signature_vendor |
Causality Actor Signature Vendor |
Causality actor process signature vendor |
| causality_actor_process_signature_status |
Causality Actor Signature Status |
Causality actor process signature status |
| causality_actor_process_execution_time |
Causality Actor Execution Time |
Causality actor process execution time |
| action_process_image_path |
Action Process Path |
Action process path |
| action_process_signature_vendor |
Action Process Signature Vendor |
Action process signature vendor |
| action_process_signature_status |
Action Process Signature Status |
Action process signature status |
| action_file_name |
Action File Name |
Action file name |
| action_file_path |
Action File Path |
Action file path |
| action_file_sha256 |
Action File SHA256 |
Action file SHA256 |
| action_file_md5 |
Action File MD5 |
Action file MD5 |
|
|
Palo Alto Networks Cortex XDR(XDR Analytics BIOC)
(palo_alto_cortex_xdr_analytics_bioc)
|
| palo_alto_networks.name |
Alert Name |
Alert name |
| palo_alto_networks.category |
Category |
Alert category |
| palo_alto_networks.alert_type |
Alert Type |
Alert yype |
| event.severity_str |
Palo Alto Networks Cortex XDR Alert Severity |
Palo Alto Networks Cortex XDR alert severity |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| palo_alto_networks.alert_id |
Alert ID |
Alert ID |
| palo_alto_networks.matching_service_rule_id |
Rule ID |
Matching rule ID |
| palo_alto_networks.matching_status |
Match Status |
Matching status |
| palo_alto_networks.action_pretty |
Action |
Action taken |
| palo_alto_networks.source |
Source |
Alert source |
| palo_alto_networks.agent_version |
Agent Version |
Agent version |
| palo_alto_networks.agent_os_type |
OS Type |
Operating System type |
| palo_alto_networks.agent_os_sub_type |
OS Version |
OS version |
| palo_alto_networks.resolution_status |
Status |
Resolution status |
| palo_alto_networks.mitre_tactic_id_and_name |
MITRE Tactics |
MITRE tactics |
| palo_alto_networks.mitre_technique_id_and_name |
MITRE Techniques |
MITRE techniques |
| palo_alto_networks.events |
Events |
Related events |
| event_type |
Event Type |
Event type |
| user_name |
User Name |
User name |
| action_process_image_name |
Action Process |
Action process |
| action_process_image_command_line |
Command Line |
Process command line |
| actor_process_image_path |
Actor Process Path |
Actor process path |
| action_process_image_sha256 |
Process SHA256 |
Process SHA256 |
| action_process_signature_vendor |
Action Process Signature Vendor |
Action process signature vendor |
| action_process_signature_status |
Action Process Signature Status |
Action process signature status |
| action_process_causality_id |
Action Process Causality ID |
Action process causality ID |
| actor_process_image_name |
Actor Process |
Actor process |
| actor_process_command_line |
Actor Command Line |
Actor command line |
| actor_process_image_path |
Actor Process Path |
Actor process path |
| actor_process_image_sha256 |
Actor SHA256 |
Actor process SHA256 |
| actor_process_image_md5 |
Actor MD5 Hash |
Actor process MD5 |
| actor_process_signature_vendor |
Actor Signature Vendor |
Actor process signature vendor |
| actor_process_signature_status |
Actor Signature Status |
Actor process signature status |
| actor_process_os_pid |
Actor Process PID |
Actor process PID |
| actor_process_instance_id |
Actor Process Instance ID |
Actor process instance ID |
| actor_process_causality_id |
Actor Process Causality ID |
Actor process causality ID |
| causality_actor_process_image_name |
Causality Actor Process Name |
Causality actor process name |
| causality_actor_process_image_path |
Causality Actor Process Path |
Causality actor process path |
| causality_actor_process_command_line |
Causality Actor Command Line |
Causality actor process command line |
| causality_actor_process_image_sha256 |
Causality Actor SHA256 |
Causality actor process SHA256 |
| causality_actor_process_image_md5 |
Causality Actor MD5 |
Causality actor process MD5 |
| causality_actor_process_signature_vendor |
Causality Actor Signature Vendor |
Causality actor process signature vendor |
| causality_actor_process_signature_status |
Causality Actor Signature Status |
Causality actor process signature status |
| causality_actor_process_execution_time |
Causality Actor Execution Time |
Causality actor process execution time |
| causality_actor_causality_id |
Causality Actor Causality ID |
Causality actor causality ID |
| os_actor_process_image_name |
OS Actor Process Name |
OS actor process name |
| os_actor_process_image_path |
OS Actor Process Path |
OS actor process path |
| os_actor_process_command_line |
OS Actor Command Line |
OS actor process command line |
| os_actor_process_image_sha256 |
OS Actor SHA256 |
OS actor process SHA256 |
| os_actor_process_signature_vendor |
OS Actor Signature Vendor |
OS actor process signature vendor |
| os_actor_process_signature_status |
OS Actor Signature Status |
OS actor process signature status |
| os_actor_process_os_pid |
OS Actor Process PID |
OS actor process PID |
| os_actor_process_instance_id |
OS Actor Process Instance ID |
OS actor process instance ID |
| os_actor_process_causality_id |
OS Actor Process Causality ID |
OS actor process causality ID |
| os_actor_thread_thread_id |
OS Actor Thread ID |
OS actor thread ID |
| event_timestamp |
Event Timestamp |
Event timestamp |
| association_strength |
Association Strength |
Association strength |
| event_sub_type |
Event Sub Type |
Event sub type |
| agent_install_type |
Agent Install Type |
Agent install type |
| agent_host_boot_time |
Agent Host Boot Time |
Agent host boot time |
| contains_featured_host |
Contains Featured Host |
Contains featured host |
| contains_featured_ip |
Contains Featured IP |
Contains featured IP address |
| contains_featured_user |
Contains Featured User |
Contains featured user |
| action_country |
Action Country |
Action country |
|
|
Palo Alto Networks Cortex XDR(XDR BIOC)
(palo_alto_cortex_xdr_bioc)
|
| palo_alto_networks.name |
Alert Name |
Alert name |
| palo_alto_networks.category |
Category |
Alert category |
| palo_alto_networks.bioc_category_enum_key |
BIOC Category |
BIOC category |
| palo_alto_networks.alert_type |
Alert Type |
Alert type |
| event.severity_str |
Palo Alto Networks Cortex XDR Alert Severity |
Palo Alto Networks Cortex XDR alert severity |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| palo_alto_networks.alert_id |
Alert ID |
Alert ID |
| palo_alto_networks.case_id |
Case ID |
Case ID |
| palo_alto_networks.matching_service_rule_id |
Rule ID |
Matching rule ID |
| palo_alto_networks.matching_status |
Match Status |
Matching status |
| palo_alto_networks.action_pretty |
Action |
Action taken |
| palo_alto_networks.source |
Source |
Alert source |
| palo_alto_networks.agent_version |
Agent Version |
Agent version |
| palo_alto_networks.agent_os_type |
OS Type |
Operating System type |
| palo_alto_networks.agent_os_sub_type |
OS Version |
OS version |
| palo_alto_networks.resolution_status |
Status |
Resolution status |
| palo_alto_networks.bioc_indicator |
BIOC Indicator |
BIOC indicator details |
| palo_alto_networks.mitre_tactic_id_and_name |
MITRE Tactics |
MITRE tactics |
| palo_alto_networks.mitre_technique_id_and_name |
MITRE Techniques |
MITRE techniques |
| palo_alto_networks.events |
Events |
Related events |
| event_type |
Event Type |
Event type |
| user_name |
User Name |
User name |
| action_process_image_name |
Action Process |
Action process |
| action_process_image_command_line |
Command Line |
Process command line |
| actor_process_image_path |
Actor Process Path |
Actor process path |
| action_process_image_sha256 |
Process SHA256 |
Process SHA256 |
| action_process_signature_vendor |
Action Process Signature Vendor |
Action process signature vendor |
| action_process_signature_status |
Action Process Signature Status |
Action process signature status |
| action_process_causality_id |
Action Process Causality ID |
Action process causality ID |
| action_process_instance_id |
Action Process Instance ID |
Action process instance ID |
| actor_process_image_name |
Actor Process |
Actor process |
| actor_process_command_line |
Actor Command Line |
Actor command line |
| actor_process_image_path |
Actor Process Path |
Actor process path |
| actor_process_image_sha256 |
Actor SHA256 |
Actor process SHA256 |
| actor_process_image_md5 |
Actor MD5 Hash |
Actor process MD5 |
| actor_process_signature_vendor |
Actor Signature Vendor |
Actor process signature vendor |
| actor_process_signature_status |
Actor Signature Status |
Actor process signature status |
| actor_process_os_pid |
Actor Process PID |
Actor process PID |
| actor_process_instance_id |
Actor Process Instance ID |
Actor process instance ID |
| actor_process_causality_id |
Actor Process Causality ID |
Actor process causality ID |
| actor_thread_thread_id |
Actor Thread ID |
Actor thread ID |
| causality_actor_process_image_name |
Causality Actor Process Name |
Causality actor process name |
| causality_actor_process_image_path |
Causality Actor Process Path |
Causality actor process path |
| causality_actor_process_command_line |
Causality Actor Command Line |
Causality actor process command line |
| causality_actor_process_image_sha256 |
Causality Actor SHA256 |
Causality actor process SHA256 |
| causality_actor_process_image_md5 |
Causality Actor MD5 |
Causality actor process MD5 |
| causality_actor_process_signature_vendor |
Causality Actor Signature Vendor |
Causality actor process signature vendor |
| causality_actor_process_signature_status |
Causality Actor Signature Status |
Causality actor process signature status |
| causality_actor_process_execution_time |
Causality Actor Execution Time |
Causality actor process execution time |
| causality_actor_causality_id |
Causality Actor Causality ID |
Causality actor causality ID |
| os_actor_process_image_name |
OS Actor Process Name |
OS actor process name |
| os_actor_process_image_path |
OS Actor Process Path |
OS actor process path |
| os_actor_process_command_line |
OS Actor Command Line |
OS actor process command line |
| os_actor_process_image_sha256 |
OS Actor SHA256 |
OS actor process SHA256 |
| os_actor_process_signature_vendor |
OS Actor Signature Vendor |
OS actor process signature vendor |
| os_actor_process_signature_status |
OS Actor Signature Status |
OS actor process signature status |
| os_actor_process_os_pid |
OS Actor Process PID |
OS actor process PID |
| os_actor_process_instance_id |
OS Actor Process Instance ID |
OS actor process instance ID |
| os_actor_process_causality_id |
OS Actor Process Causality ID |
OS actor process causality ID |
| os_actor_thread_thread_id |
OS Actor Thread ID |
OS actor thread ID |
| event_timestamp |
Event Timestamp |
Event timestamp |
| association_strength |
Association Strength |
Association strength |
| dst_association_strength |
Dst Association Strength |
Destination association strength |
| event_sub_type |
Event Sub Type |
Event sub type |
| agent_install_type |
Agent Install Type |
Agent install type |
| agent_host_boot_time |
Agent Host Boot Time |
Agent host boot time |
| contains_featured_host |
Contains Featured Host |
Contains featured host |
| contains_featured_ip |
Contains Featured IP |
Contains featured IP address |
| contains_featured_user |
Contains Featured User |
Contains featured user |
| action_country |
Action Country |
Action country |
|
|
Palo Alto Networks Cortex XDR(XDR IOC)
(palo_alto_cortex_xdr_ioc_alerts)
|
| palo_alto_networks.name |
Alert Name |
Alert name |
| palo_alto_networks.category |
IOC Category |
IOC category |
| palo_alto_networks.bioc_category_enum_key |
IOC Type |
IOC type |
| event.severity_str |
Palo Alto Networks Cortex XDR Alert Severity |
Palo Alto Networks Cortex XDR alert severity |
| host.name |
Host Name |
Host name |
| host.ip |
Host IP |
Host IP address |
| palo_alto_networks.alert_id |
Alert ID |
Alert ID |
| palo_alto_networks.matching_service_rule_id |
Rule ID |
Matching rule ID |
| palo_alto_networks.matching_status |
Match Status |
Matching status |
| palo_alto_networks.action_pretty |
Action |
Action taken |
| palo_alto_networks.source |
Source |
Alert source |
| palo_alto_networks.agent_version |
Agent Version |
Agent version |
| palo_alto_networks.agent_os_type |
OS Type |
Operating System type |
| palo_alto_networks.agent_os_sub_type |
OS Version |
OS version |
| palo_alto_networks.resolution_status |
Status |
Resolution status |
| palo_alto_networks.events |
Events |
Related events |
| event_type |
Event Type |
Event type |
| user_name |
User Name |
User name |
| action_process_image_name |
Action Process |
Action process |
| actor_process_image_name |
Actor Process |
Actor process |
| action_process_image_sha256 |
Process SHA256 |
Process SHA256 |
| actor_process_image_sha256 |
Actor SHA256 |
Actor process SHA256 |
| action_process_image_command_line |
Command Line |
Process command line |
| actor_process_command_line |
Actor Command Line |
Actor command line |
| actor_process_image_path |
Actor Process Path |
Actor process path |
| actor_process_image_md5 |
Actor MD5 Hash |
Actor process MD5 |
| actor_process_signature_vendor |
Actor Signature Vendor |
Actor process signature vendor |
| actor_process_signature_status |
Actor Signature Status |
Actor process signature status |
| actor_process_os_pid |
Actor Process PID |
Actor process PID |
| actor_thread_thread_id |
Actor Thread ID |
Actor thread ID |
| causality_actor_process_image_name |
Causality Actor Process Name |
Causality actor process name |
| causality_actor_process_image_path |
Causality Actor Process Path |
Causality actor process path |
| causality_actor_process_command_line |
Causality Actor Command Line |
Causality actor process command line |
| causality_actor_process_image_sha256 |
Causality Actor SHA256 |
Causality actor process SHA256 |
| causality_actor_process_signature_vendor |
Causality Actor Signature Vendor |
Causality actor process signature vendor |
| causality_actor_process_signature_status |
Causality Actor Signature Status |
Causality actor process signature status |
| causality_actor_process_execution_time |
Causality Actor Execution Time |
Causality actor process execution time |
| action_process_image_path |
Action Process Path |
Action process path |
| action_process_signature_vendor |
Action Process Signature Vendor |
Action process signature vendor |
| action_process_signature_status |
Action Process Signature Status |
Action process signature status |
| action_file_name |
Action File Name |
Action file name |
| action_file_path |
Action File Path |
Action file path |
| action_file_sha256 |
Action File SHA256 |
Action file SHA256 |
| action_file_md5 |
Action File MD5 |
Action file MD5 |
|
|
Proofpoint TAP
(proofpoint_tap)
|
| srcip |
Source IP Address |
Source IP address |
| url |
Malicious URL |
Malicious URL that was clicked |
| email.subject |
Email Subject |
Email subject |
| email.sender.address |
Sender Address |
Who actually sent the email on behalf of the primary sender |
| email.from.address |
From Address |
Who the email is from |
| email.recipient.addresses |
Recipient Address(es) |
Who received the email (including CC and BCC) |
| email.to.addresses |
To Address(es) |
Primary intended recipient of the email |
| email.x_mailer |
X-Mailer |
X-Mailer content |
| event.threat_list |
Proofpoint Event Threat List |
Threat category: Threat artifact |
| name |
Threat Name |
Proofpoint threat name |
| category |
Threat Category |
Proofpoint threat category |
| attachment |
Threat Attachment |
Proofpoint threat attachment |
| severity |
Proofpoint Threat Severity |
Proofpoint threat severity |
| url |
Proofpoint Threat URL |
Proofpoint threat URL |
|
|
Recorded Future Alert
(recorded_future_normal_alert)
|
| recorded_future.rule.name |
Rule Name |
Rule name |
| recorded_future.owner_organisation_details.organisations |
Organizations as defined by Recorded Future |
Organizations as defined by Recorded Future |
| organisation_name |
Organization Name |
Organization name |
| recorded_future.log.triggered |
Alert Time |
Alert time |
| recorded_future.url.portal |
Recorded Future Alert URL |
Recorded Future alert URL |
| recorded_future.rule.url.portal |
Recorded Future Alert Rule URL |
Recorded Future alert rule URL |
|
|
Recorded Future Playbook Alert
(recorded_future_playbook_alert)
|
| recorded_future.playbook_alert_id |
Playbook Alert ID |
Playbook alert ID |
| recorded_future.priority |
Alert Priority |
Alert priority |
| recorded_future.panel_status.case_rule_label |
Playbook Alert Rule Name |
Playbook alert rule name |
| recorded_future.title |
Alert Title |
Alert title |
| recorded_future.panel_status.entity_name |
Entity Name |
Entity name |
| recorded_future.panel_status.entity_id |
Entity ID |
Entity ID |
| recorded_future.owner_organisation_details.organisations |
Organizations as defined by Recorded Future |
Organizations as defined by Recorded Future |
| organisation_name |
Organization Name |
Organization name |
| recorded_future.panel_status.targets |
Alert Targets |
Alert targets |
| recorded_future.panel_status.targets_obj |
Alert Targets |
Alert targets |
| name |
Alert Target |
Alert target |
| recorded_future.actions_taken |
Actions Taken |
Actions taken |
| recorded_future.panel_status.subject |
Affected Subject |
Affected subject |
| recorded_future.panel_status.authorization_url |
Authorization URL |
Authorization URL |
| recorded_future.panel_evidence_summary.malware_family.name |
Malware Family |
Malware family |
| recorded_future.panel_evidence_summary.compromised_host.malware_file |
Malware File |
Malware file |
| recorded_future.panel_evidence_summary.compromised_host.exfiltration_date |
Exfiltration Date |
Exfiltration date |
| recorded_future.panel_evidence_summary.compromised_host.os_username |
Compromised Host OS |
Compromised host OS username |
| recorded_future.panel_evidence_summary.compromised_host.computer_name |
Compromised Host Computer Name |
Compromised host computer name |
| recorded_future.panel_evidence_summary.infrastructure.ip |
Infrastructure IP Address |
Infrastructure IP address |
| recorded_future.panel_evidence_summary.repository.name |
Repository Name |
Repository name |
| recorded_future.panel_evidence_summary.repository.owner.name |
Repository Owner |
Repository owner |
| recorded_future.panel_status.entity_criticality |
Critical Level for Entity |
Critical level for entity |
| recorded_future.panel_status.lifecycle_stage |
Lifecycle Stage |
Lifecycle stage |
| recorded_future.panel_overview.event_type |
Alert Event Type |
Alert event type |
| recorded_future.panel_overview.location |
Alert Location |
Alert location |
| recorded_future.panel_overview.facility_name |
Facility Name |
Facility name |
|
|
SentinelOne Cloud
(sentinelone)
|
| host.name |
Host Name |
Computer name |
| host.ip |
Host IP Address |
Host IP address |
| file.name |
File Name |
File name |
| file.path |
File Path |
File path |
| process.parent.name |
Parent Process Name |
Originator process name |
|
|
Sophos Alerts
(sophos_alerts)
|
| host.ip |
Host IP |
Host IP address |
| user.name |
User Name |
User name |
| event.severity_str |
Sophos Severity |
Original severity level from Sophos |
| sophos.type |
Sophos Event Type |
Sophos event type |
| sophos.data.endpoint_platform |
Endpoint Platform |
Endpoint platform |
| file.path |
File Path |
File path |
| file.hash.sha256 |
File SHA256 |
File SHA256 |
|
|
Sophos Events
(sophos_events)
|
| host.ip |
Host IP |
Host IP address |
| user.name |
User Name |
User name |
| sophos.user_id |
User ID |
User ID |
| event.severity_str |
Sophos Severity |
Original severity level from Sophos |
| sophos.type |
Sophos Event Type |
Sophos event type |
| sophos.endpoint_type |
Endpoint Platform |
Endpoint platform |
| file.path |
File Path |
File path |
| file.hash.sha256 |
File SHA256 |
File SHA256 |
|
|
Trellix (FireEye) Endpoint Security (AMSI)
(fireeye_amsi)
|
| fireeye.source |
Alert Type |
FireEye alert source type |
| event.threat.name |
Threat Name |
FireEye alert name |
| event.severity_str |
Severity |
Severity level |
| host.ip |
Host IP Address |
Host IP address |
| host.name |
Host Name |
Host name |
| file_list |
File List |
File list |
| process_list |
Process List |
Process list: Pid (process command line) |
| event.url |
Event URL |
FireEye event URL |
|
|
Trellix (FireEye) Endpoint Security (IOC)
(fireeye_ioc)
|
| fireeye.source |
Alert Type |
FireEye alert source type |
| host.ip |
Host IP Address |
Host IP address |
| host.name |
Host Name |
Host name |
| event.name |
Event Name |
Event name |
| file.name |
File Name |
File name |
| process.name |
Process Name |
Process name |
| event.url |
Event URL |
FireEye event URL |
|
|
Trellix (FireEye) Endpoint Security (MAL)
(fireeye_mal)
|
| fireeye.source |
Alert Type |
FireEye alert source type |
| event.threat.name |
Threat Name |
FireEye alert name |
| fireeye.infection_type |
Infection Type |
FireEye Infection Type |
| event.severity_str |
FireEye Severity Level |
FireEye severity level |
| host.ip |
Host IP Address |
Host IP address |
| host.name |
Host IP Address |
Host name |
| file.path |
File Path |
File path |
| file.hash.md5 |
File MD5 Hash |
File MD5 hash |
| file.hash.sha1 |
File SHA1 Hash |
File SHA1 hash |
| file.hash.sha256 |
File SHA256 Hash |
File SHA256 hash |
| process.executable |
Event Actor Process Path |
FireEye event actor process path |
| process.pid |
Event Actor Process Pid |
FireEye event actor process Pid |
| event.url |
Event URL |
FireEye event URL |
|
|
Trellix (FireEye) Endpoint Security (PROCGUARD)
(fireeye_procguard)
|
| fireeye.source |
Alert Type |
FireEye alert source type |
| event.threat.name |
Threat Name |
FireEye alert name |
| host.ip |
Host IP Address |
Host IP address |
| host.name |
Host Name |
Host name |
| file_list |
File List |
File list |
| process_list |
Process List |
Process list: Pid (process command line) |
| event.url |
Event URL |
FireEye event URL |
|
|
Trellix MVISION
(trellix_mvision)
|
| process.command_line |
Command Line |
Full command line that was executed by the process |
| process.pid |
Process ID |
Unique identifier of the process |
| process.executable |
Executable |
Executable file associated with the process |
| host.name |
Host Name |
Name of the host where the event occurred |
| user.name |
User Name |
Name of the user associated with the event |
| event.severity_str |
Trellix MVISION Severity |
Original severity from Trellix MVISION |
| event.threat.name |
Threat Name |
Name of the detected threat or activity |
|
|
Trend Micro Vision One
(trendmicro_visionone)
|
| event.threat.name |
Threat Name |
Threat name |
| event.severity_str |
Trend Micro Vision One Severity |
Original Trend Micro Vision One severity level |
| trendmicro_visionone.workbenchLink |
Trend Micro Vision One Workbench Link |
Trend Micro Vision One workbench link |
| host_list |
Host(s) |
Related host(s) |
| name |
Host Name |
Host name |
| ips |
Host IP(s) |
Host IP addresses |
| process_list |
Process(es) |
Related process(es) |
| file_list |
File(s) |
Related file(s) |
| name |
File Name |
File name |
| path |
File Path |
File path |
| hash.md5 |
File MD5 Hash |
File MD5 hash |
| hash.sha1 |
File SHA1 Hash |
File SHA1 hash |
| hash.sha256 |
File SHA256 Hash |
File SHA256 hash |
| trendmicro_visionone.alertProvider |
Alert Provider |
Trend Micro Vision One alert provider |
| user_list |
User(s) |
Related user(s) |
|
|
Varonis DatAdvantage
(varonis_datadvantage)
|
| event.type |
Event Type |
Event type |
| event.threat.name |
Threat Name |
Threat name |
| event.severity |
CEF Severity Level |
Original CEF severity level |
| user.name |
User Name |
User name |
| file.name |
File Name |
File name |
| file.path |
File Path |
File path |
|
|
VMware Carbon Black Cloud
(carbonblack)
|
| host.name |
Host Name |
Computer name |
| host.external_ip |
Host Name |
Host external IP address |
| host.ip |
Host Internal IP Address |
Host internal IP address |
| process.name |
Process Name |
Process name |
| event.description |
Event Reason |
Event reason |
|
|
Windows Defender Antivirus
(windows_defender_antivirus)
|
| event.ms_incident_id |
Incident ID |
Windows Defender incident ID |
| threat |
Threat Name |
Threat name |
| host.name |
Host Name |
Computer name |
| hostip |
Host IP Address |
Host IP address |
| file.path |
File Path |
File path |
| process.name |
Process Name |
Process name |
|