Installing a Modular Sensor in GCP
This topic describes how to install a Modular Sensor in a Google Cloud Platform (GCP) environment. Refer to the following sections for details:
- About Modular Sensors
- Site Preparation
- Configuring and Launching the Instance
- Applying a Token to the Installed Sensor
- Configuring a Static IP Address (Optional)
- Configuring Packet Mirroring in GCP
Use our example as a guideline, as you might be using a different software version.
About Modular Sensors
A modular sensor lets you easily add the features you like to your sensor. This helps simplify your deployment and lets you manage the VM requirements for the sensors based on the modular features they use.
Modular Sensors always include log ingestion. From there, you can enable features from network sensors and security sensors as part of your modular sensor profile:
-
A network sensor monitors the virtual environment, the physical environment if connected to the span port of a physical switch, or the LAN segment via a mirror port on a switch. The sensor monitors network and server response times and can identify applications.
The network sensor converts that information to metadata and forwards it to the DP as Interflow. The DP can then provide security, DDoS, and breach attempt detections.
-
A security sensor operates as a network sensor and adds:
- sandbox
- anti-virus
- IDS
Keep in mind that VM resource requirements increase as you add more features to the Modular Sensor Profile. Refer to Modular Sensor Specifications for details on the resources required to run different combinations of features in a Modular Sensor Profile, as well as how to use the show module and show module request CLI commands to compare provisioned resources against those required to run specific feature combinations. Stellar Cyber only enables a Modular Sensor Profile on a sensor if the host VM's resources can support it.
Site Preparation
Click to see the minimum system requirements for installing a modular sensor.
You must have:
- One IP address with access to a default gateway
- A Stellar Cyber license that can be applied to the sensor
To prepare for the installation:
- Open firewall ports for network or security sensor features you are enabling in the modular sensor profile.
- Open firewall ports for log ingestion.
- Contact Stellar Cyber support (support@stellarcyber.ai) for access to the image. You must provide:
- The GCP Gmail account name
Do this at least a day before installing, so we have time to deploy the images to your account.
Configuring and Launching the Instance
To configure and launch the instance:
Use our example as a guideline, as you might be using a different software version.
-
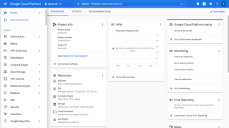
Log in to your Google Cloud Platform Dashboard.
-
Use the dropdown in the toolbar to select the Project where you want to deploy the DP.
-
Select the Compute Engine | VM instances entry from the left navigation panel.
-
Click the Create Instance button.
-
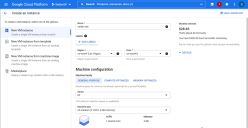
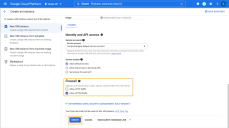
Supply a Name, Region, and Zone for the instance.
-
Choose a Machine type for the instance. You can either choose one of the preconfigured GCP machine types or create a Custom machine type, so long as the instance meets the minimum specifications.
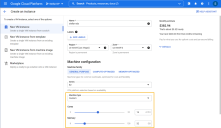
Note that Stellar Cyber recommends that in a GCP deployment, you increase the standard provisioning if you are enabling network or security sensor features in your modular sensor profile as follows:
-
Network Sensor Features Enabled – 4 virtual cores, 16 GB memory.
-
Security Sensor Features Enabled – 16 virtual cores, 32 GB memory.
In the example below, we are creating a Custom Machine Type with 16 virtual cores and 32 GB of memory to serve as the foundation for a Security Sensor:
-
-
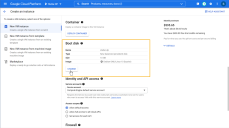
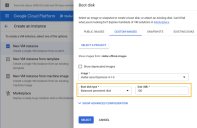
Scroll down to the Boot disk section and click the CHANGE button.
-
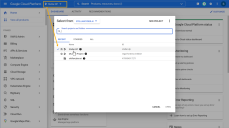
Click on the CUSTOM IMAGES tab.
-
Click the SELECT A PROJECT button and choose the stellar-official-images project.
The stellar-official-images entry won't appear until we've made images available to your account. If you don't see the stellar-official-images entry, make sure your region is the same one where you asked Customer Success to deploy the images. If you still don't see the entry, contact Customer Success.
-
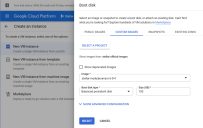
Select the entry for your sensor version and type from the Images dropdown.
-
Set the Boot disk type to Balanced persistent disk, choose a size of 100 GB, and click Select.
You are returned to the Create an instance wizard.
-
Click the Create button to create the instance.
You can launch the image but you cannot copy it. This means that the VM must be deployed in the GCP region where the image was authorized.
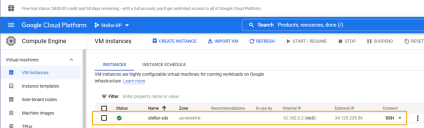
The VM is now running in the GCP cloud and appears in the Compute engine | VM instances list, as illustrated below. Copy the External IP address so you can use it to connect to the Sensor's console in the next section.
Applying a Token to the Installed Sensor
The next step is to obtain and apply the token used to authorize and configure the installed sensor.
Obtaining a Token for the Installation
Tokens are required to authorize and configure the installation of a sensor image downloaded from the DP in the System | Deployment | Sensor Installation page. Tokens point the installed sensor to the correct DP, assign the specified tenant, and authorize the sensor installation.
Use the following procedure to obtain a token in the Tokens tab:
-
Navigate to the System | Deployment | Sensor Installation page and click on the Tokens tab.
-
If a token already exists for the target tenant for the sensor installation, you can either use the Copy button to copy it to the clipboard or use the Download button to download it as a file.
-
Copy the token if you plan on applying it by pasting it into a
set token string <token>command in the CLI. -
Download the token as a file if you plan on hosting the file on an HTTP server and referring to it in a
set token url <token url>command.
Refer to Assigning Tokens for a summary of the different ways in which tokens can be applied to a sensor installation.
-
-
If there is not already an unexpired token for the target tenant, click the Generate button.
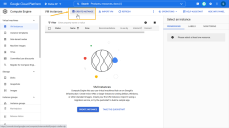
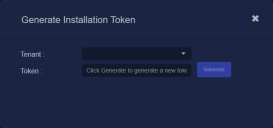
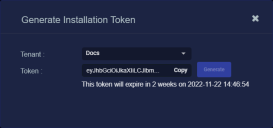
The Generate Installation Token dialog appears:
-
Select the tenant for the token from the Tenant dropdown. This is the tenant to which all sensors authorized with this token will be automatically assigned. The dropdown lists all tenants configured for your organization in the System | Tenants page.
-
Click the Generate button.
The system generates the token and displays its contents in the Token field. The dialog also updates to display the expiration date for the token, as illustrated below.
-
You can use the Copy button to copy the token to the clipboard immediately, or simply close the dialog and retrieve the token from the Tokens tab later on.
Applying the Token to the Sensor
Tokens are required to complete the installation of a sensor image downloaded from the DP in the Download Image tab.
You apply tokens to sensors as the last step in the overall installation procedure:
- Log in to your new Sensor. The default username/password is aella/changeme. You are immediately prompted to change the password.
-
Apply the token to the installed sensor from the sensor CLI with the
set tokencommand using one of the options in the table below:You only need to use one of the options in the table below. These are just two different ways to do the same thing – apply the token.
Option 1. Copy and Paste the Token String
Copy the token string from the Tokens tab and paste it into the CLI command. The syntax is as follows:
set token string <pasted string>Option 2. Host the Token on an HTTP Server
Download the token as a file from the Tokens tab, upload it to an HTTP server, and reference it in the
set tokencommand. The syntax is as follows:set token url http://<url to token>You can also use an HTTPS server. In that case, the specified URL must also include the username and password for the server using the following syntax:
set token url https://<user:password>@URL> -
The CLI reports that the Sensor token is successfully set.
If you receive an error message instead, it's possible that the token has expired. Refer to the Tokens tab to see the expiration date. If you are using the File technique, it's also possible that an extra space or line may have crept into your text file – check the file to make sure it includes only the token text.
-
Wait a minute or so. Then, verify that the token was successfully applied using any combination of the following techniques:
-
Check the System | Sensors tab in the user interface to see that the sensor has registered itself successfully.
-
Verify that the
show systemcommand shows all services as running. -
Verify that the
show receivercommand displays a receiver. -
Verify that the
show jsoncommand reports some data sent in theBYTE_SENTcolumn.
-
Configuring a Static IP Address (Optional)
By default, the sensor uses DHCP for the management port's IP address. For ease of troubleshooting, however, Stellar Cyber recommends that you reconfigure the management port to use a static IP address. The procedure is as follows:
- Log in to your sensor. The default username/password is aella/changeme, but you changed this when you applied the token in the previous section.
-
You can set IP parameters manually using commands similar to the following (substitute your own IP parameters for the ones shown in bold below):
set interface management ip 192.168.14.100/255.255.255.0
set interface management gateway 192.168.14.1
set interface management dns 8.8.8.8
-
Verify the IP settings with the
show interfacescommand. - Log out with the
quitcommand.
Configuring Packet Mirroring in GCP
Refer to Configuring GCP Packet Mirroring for details on how to use packet mirroring for packet acquisition in GCP environments.