Log Parser Ports
To receive and parse logs from devices on your network, Stellar Cyber modular sensors require open inbound ports. These ports are already open on modular sensors by default. If there are any firewalls in the data path between the log sources and a modular sensor, you must also open the appropriate ports on the firewalls. This topic lists the supported log parsers and related details, including the port each parser uses. Log parsers are organized in the following categories:
Also see: Firewall Requirements and Common Log Formats
Unless otherwise noted, the ports listed are applicable for both UDP and TCP.
During installation, the timezone for sensors are automatically set to UTC+0. Since the logs for some security products may only include the local time without a timezone, Stellar Cyber recommends that you set the sensor timezone to the same timezone as your security product.
Choosing an Ingestion Port
Modular sensors listen on port 514 by default. They then analyze the logs to determine the source device. In some cases, Stellar Cyber has specific ports to process industry standard log formats, as well as specialized parsers to process vendor-specific logs in a more detailed manner. Identifying a more specific port for a log type than port 514 provides the following benefits:
-
It speeds up data ingestion and log parsing and increases sensor performance because the sensor already knows the source device.
-
It retains the correct log source when the sensor forwards normalized logs as Interflow records to the Stellar Cyber Open XDR platform.
Use the following as a guide:
-
If the logs are in standard Common Event Format (CEF), Log Event Extended Format (LEEF), or JavaScript Object Notation (JSON) format, forward to the data to the port specific to that standard as listed in Generic Log Parsers.
-
If the logs are in standard Syslog format use the port applicable for that vendor.
-
If the logs are in a specialized format such as a Syslog and use regular expressions, key-value pairs, or comma-separated values (csv), use the Vendor-specific ports.
Using the Port Relay Feature to Minimize Open Ports
It's a best practice in Stellar Cyber to send logs to their vendor-specific parsers, when available. In releases previous to 4.3.5, this was accomplished by referring to the list of supported vendor-specific ports, pointing your log sources to that port on the sensor IP address, and opening the port in your firewall.
This approach is still available and can be used. As an alternative, however, you can configure your sensors to accept log traffic on the generic syslog ports of 514 (non-TLS) or 6514 (TLS) and relay that traffic to vendor-specific ports internally based on the source traffic's IP address.
You do this differently depending on the release your sensors are running:
-
For sensors running 4.3.5, you configure port relay in the sensor CLI using the instructions below.
-
For sensors running 4.3.6, you configure port relay in the System | Log Sources page. In 4.3.6, CLI configuration is deprecated and only the Log Sources page is used.
Configuring Port Relay in the CLI ()
You configure the port relay feature for sensors running
-
Find the IP address of your log source.
-
Use the Log Parser Portstopic to find the parser port for your log source.
-
Connect to the sensor CLI.
-
Use the set logforwarder device-ip command to make an entry on the sensor for your log source and the corresponding destination port. The syntax is as follows:
set logforwarder device-ip <IP Address> parser-port <Integer> ingestion-port <514|6514 default=514>So, for example, if you are sending Azure MFA logs from 10.33.5.5 to the sensor, you could either send them directly to port 5528 as you did in previous releases, or you could send them to the standard syslog port of 514 and use the following command on the sensor to relay them internally to 5528:
set logforwarder device-ip 10.33.5.5 parser-port 5528This command tells the sensor to relay logs received on port 514 (the default, which is why it is not explicitly specified in the command above) from 10.33.5.5 to the vendor-specific parser port of 5528 for Azure MFA.
You can also use the ingestion-port argument if you want to listen for a source on the generic TLS syslog port instead of the default of 514. For example, for Netfilter logs sent from 10.31.2.2, you would use the following command to relay them from 6514 to their vendor-specific parser port of 5544:
set logforwarder device-ip 10.31.2.2 parser-port 5544 ingestion-port 6514
Notes on Using the Port Relay Feature
Keep in mind the following tips when using the port relay feature:
-
Keep in mind that the sending log source must be on the same subnet as the receiving sensor. There must be no proxy capable of changing the log source IP between the sending log source and the receiving sensor.
-
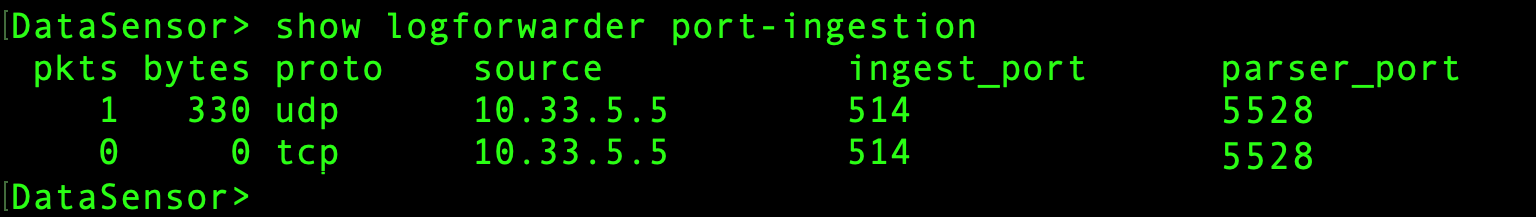
When you create a port relay entry, the sensor listens for both UDP and TCP traffic from the specified source. You can see this with the show logforwarder port-ingestion command. For example:
-
The show logforwarder port-ingestion command is also a useful tool for troubleshooting port relay entries. You can see packet and byte counts for relayed traffic and determine whether traffic is reaching the sensor.
-
You can remove port relay entries using unset logforwarder device-ip <IP Address>.
-
The CLI warns you if you try to add an unsupported parser port. It still adds the unsupported port but lists it in the show logforwarder port-ingestion output as inactive.
Generic Log Parsers
This table includes all supported generic log parser formats, the required firewall port, device type, and the associated Stellar Cyber index.
Use the msg_origin.source field in the Interflow to find the logs when threat hunting in the specified index.
In the Interflow, there are also fields for msg_origin.processor.type, which is always log_forwarder for log parsers, and msg_origin.processor.name, which stores specific components of the parser, such as the parser type (cef, leef).
When the Stellar Cyber Platform processes logs, it decides the index based on the data in the logs. For example, in the table the Index for LEEF is Traffic (srcip), Syslog (otherwise). This means that the index will be Traffic if a source IP address is detected, or Syslog if not, in that order.
Following are the firewall ports to open for generic log formats, along with other useful details.
|
Standard |
Port |
msg_origin.source | Index | Comments |
|---|---|---|---|---|
| CEF | 5143 | cef_device_vendor |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) The following vendor records are also indexed in IDPS/Malware Sandbox Events, with the threat field being normalized from logs as indicated below:
|
Stellar Cyber recommends using CEF, if available. |
| CEF2 | 5175 | cef_device_vendor | Traffic (srcip), Syslog (otherwise) | - |
| Generic capture | 5201 | generic_capture | Syslog | - |
| Generic syslog | 514 | - | - | Use only if you must use a log forwarder. |
| HTTP JSON | 5200 (tcp) | httpjson | Syslog | When you configure your log forwarding for the HTTP JSON parser on this port, you must append /httpjson at the end of the URL of the target sensor. Example: http://<sensor-ip>:5200/httpjson |
| JSON stream | 5142 | json | Syslog | |
| JSON beats | 5044 | beats | Syslog | - |
| LEEF | 5522 | vendor | Traffic (srcip), Syslog (otherwise) | LEEF is primarily useful for logs from QRadar, for which LEEF was developed. |
|
Linux Syslog |
5555 |
linux_syslogs |
Syslog |
|
|
RFC 3164 |
5140 | syslog | Syslog | - |
| RFC 5424 |
5141 |
syslog | Syslog | - |
| RFC 5424 Enhanced |
5589 |
syslog_rfc5424 | Syslog |
|
Vendor-specific Log Parsers
This table includes all supported vendor-specific parsers, the port on which parsers listen for log messages, log formats, device types, message types, and their associated Stellar Cyber indices.
The Log Format column states the format that log sources use when sending data to Stellar Cyber modular sensors. For information about the common log formats that Stellar Cyber parsers support, see Common Log Formats.
The msg_origin.source column specifies the vendor's product. Use the field in the Interflow to find the logs when threat hunting in the specified index. The msg_origin.category column specifies the overall category. In the Interflow, there are also fields for msg_origin.processor.type, which is always log_forwarder for log parsers, and msg_origin.processor.name, which stores specific components of the parser, such as the parser name.
The Index column indicates the fields that must be present (and not null) for the logged data to be entered into the respective index. In some cases, no specific field is required, so just the index name is listed. For many parsers, the remaining data that is not mapped to a specific index is "otherwise" and mapped into the Syslog index. For example, for FortiAnalyzer logs received on port 5542, data is added to the IDPS/Malware Sandbox Events index if the incoming field vendor.attack_name is not null. Data is added to the Traffic index if dstip is not null. The remaining data is added to the Syslog index. Use the dev_type field in the Interflow to find logs when threat hunting in the specified index.
| RFC 3164 = RFC 3164: The BSD Syslog Protocol | KVP = key-value pairs |
| RFC 5424 = RFC 5424: The Syslog Protocol | JSON = JavaScript Object Notation |
| CEF = Common Event Format | HTTP JSON = HTTP protocol headers followed by JSON content |
| LEEF = Log Event Extended Format (used primarily for QRadar) | ( ) = optional |
| regex = regular expressions | + = and |
Example: The log format RFC 3164 + (regex) means that logs include syslog messages formatted as specified in RFC 3164: The BSD Syslog Protocol and that regular expressions can be applied if needed. Log messages formatted according to RFC 3164 have a priority value, which encodes facility and severity, a timestamp, a hostname, and the log message. Regular expressions might optionally be applied to the log message to perform additional operations such as parsing complex messages, filtering logs, and extracting specific fields.
|
Parser Name |
Port |
Log Format |
msg_origin.source |
msg_origin.category |
Index |
|---|---|---|---|---|---|
|
(OpnSense) Zenarmor plugin logs |
5604 |
Sunny Valley Networks custom format |
sunny_valley_networks_zenarmor |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| AAA - Core (CEF) |
5143 |
CEF |
netiq_advance_auth |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Accops | 5526 |
Accops custom format |
accops |
vpn |
Traffic (srcip), Syslog (otherwise) |
| Ahnlab AIPS |
5647 |
custom LEEF (RFC 3164 or RFC 5424) |
ahnlab_aips |
idps |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Ahnlab Cloud Protection Platform |
5755 |
CEF |
ahnlab_cpp |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| AhnLab EMS |
5657 |
regex + KVP |
ahnlab_ems |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| AhnLab EPP |
5640 |
regex + JSON |
ahnlab_epp |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| AhnLab Policy Center | 5571 |
AhnLab custom format |
ahnlab_policy_center |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| AhnLab TrusGuard | 5558 |
grave accent-separated ( ` ) KVP |
ahnlab_trusguard |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
AirGap Ransomware Kill Switch |
5602 |
AirGap custom format |
airgap_ransomware_kill_switch |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| AirWatch | 5143 |
CEF |
airwatch |
iot |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| AIX | 5523 |
IBM custom format for AIX |
aix |
unixlogs |
Traffic (event_time: time format of hour:minute:second), Syslog (otherwise) |
|
Alcatel-Lucent Switch |
5677 |
Alcatel-Lucent custom format |
alcatel_lucent_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Aliyun / AliCloud | 5545 |
RFC 3164 or RFC 5424 + regex |
aliyun |
paas |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Amazon Web Services WAF |
5735 |
RFC 3164 + Logstash header + JSON |
aws_waf |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Android |
5605 |
Google custom format for Android |
android |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Apache HTTP Server (HTTPD) |
5663 |
RFC 3164 + custom header + regex |
apache_httpd |
weblogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Appgate VPN |
5743 |
RFC 3164 + regex + JSON |
appgate_vpn |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| AQTRONiX WebKnight |
5658 |
AQTRONiX custom format |
aqtronix_webknight |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Aqua Cloud Native Application Protection Platform (CNAPP 2022.4) |
5656 |
RFC 3164 + regex + KVP |
aquasecurity_cnapp |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Arbor Peakflow SP |
5598 |
Arbor Networks custom format |
arbor_peakflow_sp |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Arista Networks Data Center Switch Router |
5747 |
RFC 3164 (with time zone and year in timestamp) |
arista_data_center_switch_router |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Array Networks APV Series Load Balancing & App Delivery |
5680 |
regex (specific to log_id) |
array_networks_apv |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Array Networks ASF 1800 |
5675 |
regex + KVP |
array_networks_asf_1800 |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Array Networks Secure Access Gateway | 5537 |
RFC 3164 |
array_sag |
vpn |
Traffic (srcip), Syslog (otherwise) |
| Aruba ClearPass Policy Manager (CEF) | 5143 |
CEF |
aruba_clear_pass |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Aruba Switch | 5577 |
RFC 3164 or RFC 5424 + KVP |
aruba_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Automox | 5183 |
Automox custom format |
automox |
patch |
Syslog |
|
Avanan |
5681 |
RFC 5424 + custom regex |
avanan |
|
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Avanan (HTTP JSON) |
5200 (TCP only) |
HTTP JSON |
avanan |
|
Syslog |
|
Avaya Switch |
5607 |
Avaya custom format |
avaya_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Aviatrix Firewall |
5762 |
RFC 3164 |
aviatrix_firewall |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
AWS WAF (HTTP JSON) |
5200 (TCP only) |
HTTP JSON |
aws_waf |
waf |
Syslog |
|
AXGATE Next Generation Firewall |
5703 |
RFC 3164 + KVP |
axgate_ngfw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Azure ATP (CEF) | 5143 |
CEF |
azure_atp |
iam |
Traffic (srcip, srcport, dstip, dstports, and proto), Syslog (otherwise) |
| Azure MFA | 5528 |
custom RFC 3164 |
azure_mfa |
iam |
Traffic (srcip), Syslog (otherwise) |
| Barracuda email | 5559 |
JSON |
barracuda_email |
|
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Barracuda firewall | 5524 |
Barracuda Networks custom format |
barracuda_fw |
firewall |
IDPS/Malware Sandbox Events (sub_dev_type: fw_threat or fw_av), Traffic (srcip), Syslog (otherwise) |
| Barracuda WAF | 5524 |
Barracuda Networks custom format |
barracuda_waf |
waf |
IDPS/Malware Sandbox Events (sub_dev_type: fw_threat or fw_av), Traffic (srcip), Syslog (otherwise) |
|
BeyondTrust BeyondInsight |
5621 |
regex + KVP |
beyondtrust_beyondinsight |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
BeyondTrust PasswordSafe |
5692 |
RFC 3164 + KVP |
beyondtrust_passwordsafe |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Bitdefender (HTTP JSON) (Syslog JSON) |
5200 (TCP only) 5142 |
HTTP JSON or syslog JSON |
bitdefender |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| BlackBerry CylancePROTECT & CylanceOPTICS | 5177 |
KVP |
cylance |
endpoint |
Traffic (srcip), Syslog (otherwise) |
| BlueCoat Proxy SG | 5576 |
Broadcom custom format |
bluecoat_proxysg |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Brocade switch (system & admin logs) | 5548 |
RFC 3164 + regex |
brocade_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Calyptix UTM | 5161 |
KVP |
calyptix |
firewall |
IDPS/Malware Sandbox Events (ids.signature), Traffic (srcip), Syslog (otherwise) |
|
Centos Audit |
5673 |
KVP |
centos_audit |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Centrify | 5165 |
KVP |
centrify |
iam |
Syslog |
| Cerberus FTP Logs |
5635 |
regex |
cerverus_ftp |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Check Point - Application Control (CEF) |
5143 |
CEF |
fw_checkpoint |
firewall |
IDPS/Malware Sandbox Events (threat, normalized from attack_information), Traffic (srcip, srcport,dstip,dstport, and proto), Syslog (otherwise) |
| Check Point - URL Filtering (CEF) |
5143 |
CEF |
fw_checkpoint |
firewall |
IDPS/Malware Sandbox Events (threat, normalized from attack_information), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| CheckPoint appliance | 5174 |
KVP |
fw_checkpoint_appliance |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| CheckPoint firewall | 5519 |
RFC 5424 + KVP inside structured data (SD) |
fw_checkpoint |
firewall |
Traffic (srcip), Syslog (otherwise) |
|
5618 |
regex + KVP |
checkpoint_harmony_ep |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
|
CheckPoint SmartCenter |
5741 |
RFC 5424 |
checkpoint_smartcenter |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
5143 |
CEF |
fw_checkpoint |
firewall |
IDPS/Malware Sandbox Events (threat, normalized from attack_information), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) | |
|
Cisco ACI |
5717 |
cisco_aci |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
| Cisco ASA | 5518 |
Cisco Systems custom format |
fw_cisco_asa |
firewall |
Traffic (srcip), Syslog (otherwise) |
|
Cisco Catalyst Firewal l |
5702 |
regex + description |
cisco_catalyst_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Cisco Catalyst SD-WAN |
5746 |
NetFlow v9 |
cisco_sd_wan |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Cisco CUCM | 5532 |
syslog + regex |
cisco_cucm |
voip |
Syslog |
| Cisco ESA | 5562 |
Cisco Systems custom format |
cisco_esa |
|
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Cisco ESA | 5164 (deprecated) |
Cisco Systems custom format |
openldap_style |
|
Syslog |
| Cisco Firepower | 5168 |
KVP |
ips_fire_power |
firewall |
Traffic (srcip), Syslog (otherwise) |
| Cisco IKE | 5176 |
KVP |
ciscovpn |
vpn |
Syslog |
| Cisco IronPort | 5163 |
Cisco Systems custom format |
cisco_ironport |
|
Syslog |
| Cisco ISE | 5157 |
KVP |
ciscoise |
asset |
Syslog |
| Cisco MDS | 5563 |
RFC 3164 + regex |
cisco_mds |
netlogs |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Cisco Meraki | 5172 |
syslog + regex |
meraki |
firewall |
Traffic (srcip), Syslog (otherwise) IDPS/Malware Sandbox Events (threat), (device_event_category,msg,signature,event_severity), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Cisco NetFlow | 2055 (UDP only) |
NetFlow v5 and v9 |
netflow |
traffic |
Traffic |
| Cisco routers and switches | 5158 |
Cisco Systems custom format |
cisco_router_switch |
netlogs |
Syslog |
|
Cisco Secure Network Analytics (Stealthwatch) |
5719 |
RFC 3164 + KVP |
cisco_secure_network_analytics |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Cisco UCS | 5579 |
RFC 5424 + (regex) |
cisco_ucs |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Cisco Umbrella | 5521 |
CSV |
cisco_umbrella |
dnssec |
Syslog |
| Cisco VPN | 5156 |
Cisco Systems custom format |
ciscovpn |
vpn |
Syslog |
| Cisco WLC | 5531 |
syslog (regex) |
cisco_wlc |
wireless |
Syslog |
|
Citrix Access Gateway |
5688 |
Citrix Systems custom format |
citrix_access_gateway |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Citrix NetScaler | 5166 |
KVP |
netscaler |
netmgmt |
Syslog |
|
Citrix NetScaler (CEF) |
5143 |
CEF |
netscaler |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Citrix XenServer |
5732 |
RFC 3164 + regex |
citrix_xenserver |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Clavister NetWall |
5760 |
regex + KVP |
clavister_netwall |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Commvault Commserve |
5740 |
regex + KVP |
commvault_commserve |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Commvault Metallic ThreatWise |
5736 |
RFC 3164 + regex |
commvault_metallic_threatwise |
mdr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Comodo- CIS CCS (CEF) |
5143 |
CEF |
comodo |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ConnectWise ScreenConnect |
5744 |
RFC 5424 (with custom structured data using KVP) |
connectwise_screenconnect |
remote_access |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
CoreLight Sensor |
5575 |
JSON |
corelight_sensor |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| CoSoSys Endpoint Protection |
5654 |
RFC 5424 + custom KVP |
cososys |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Cribl default (Syslog JSON) |
5142 |
|
json |
xdr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Cribl / NXLog (Syslog JSON) |
5142 |
JSON |
microsoft |
endpoint |
Windows Events |
| CrowdStrike (Beats) | 5044 |
JSON |
crowdstrike |
endpoint |
Syslog |
| CrowdStrike (CEF) | 5143 |
CEF |
crowd_strike_falcon_host |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
CyberArk PTA (CEF) |
5143 |
CEF |
cyberark |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Cygna Labs Cygna Auditor |
5718 |
RFC 5424 + JSON |
cygna_labs_cygna_auditor |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Cynerio |
5727 |
RFC 5424 with syslog messages in structured data (SD) |
cynerio |
iot |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Cynet (CEF) |
5143 |
CEF |
cynet |
xdr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| D-Link | 5189 |
D-Link custom format |
dlink |
wireless |
Traffic (srcip), Syslog (otherwise) |
| DBSafer | 5181 |
CSV |
dbsafer |
dlp |
Syslog |
|
Deep Instinct |
5628 |
regex + KVP |
deep_instinct |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Dell EMC Powerstore |
5683 |
RFC 3164 + local header (RFC 5424) + message |
dell_powerstore |
storage |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Dell iDRAC | 5566 |
RFC 5424 + KVP |
dell_idrac |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Dell Switch | 5578 |
Dell Technologies custom format |
dell_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
DHCP (Beats) |
5044 |
JSON |
dhcp |
netmgmt |
Traffic (srcmac), Syslog (otherwise) |
| DHCPD (ISC DHCP) | 5554 |
RFC 3164 + regex |
dhcpd |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| DNSVault RPZdb |
5639 |
regex + JSON |
dnsvault_rpzdb |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Dragos (CEF) | 5539 |
CEF |
dragos |
otsec |
Traffic (srcip), Syslog (otherwise) |
|
DrayTek Firewall |
5593 |
DrayTek custom format |
draytek_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ECS Suricata (HTTP JSON) |
5200 (TCP only) |
HTTP JSON |
suricata |
ndr |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ECS Windows (HTTP JSON) |
5200 (TCP only) |
HTTP JSON |
microsoft_windows |
endpoint |
Windows Events (winlogevent) |
| eDictionary - eDictionary (CEF) |
5143 |
CEF |
edictionary |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| EfficientIP SOLIDserver DDI |
5761 |
RFC 3164 (hostname) |
efficient_ip_solidserver |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Egnyte (Syslog JSON) (HTTP JSON) |
5142 5200 (TCP only) |
syslog JSON or HTTP JSON |
egnyte |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Ericom ZTEdge |
5603 |
Ericom Software custom format |
ericom_ztedge |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| ESET PROTECT |
5655 |
RFC 5424 + JSON |
eset_protect |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Exium SASE (HTTP JSON) |
5200 (TCP only) |
HTTP JSON |
exium_sase |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| ExtraHop (CEF) | 5143 |
CEF |
extrahop |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Extreme AirDefense |
5612 |
regex + KVP |
extreme_airdefense |
idps |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Extreme Controller |
5666 |
RFC 3164 |
extreme_controller |
wireless |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ExtremeCloud IQ Site Engine |
5614 |
regex + KVP |
extreme_site_engine |
asset |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Extreme Networks X690 |
5699 |
regex |
extreme_x690 |
asset |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
F5 - ASM (CEF) |
5143 |
CEF |
f5 |
waf |
IDPS/Malware Sandbox Events (threat, normalized from attack_type), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| F5 BIG-IP | 5162 |
F5 custom format |
f5_big_ip |
firewall |
IDPS/Malware Sandbox Events (IDS signature), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| F5 BIG-IP Telemetry (HTTP JSON) | 5200 (TCP only) |
HTTP JSON |
f5_big_ip |
firewall |
Syslog |
| F5 IPI | 5536 | f5_threat_intelligence |
firewall |
IDPS/Malware Sandbox Events (dev_type: /threat/), Traffic (dstip), Syslog (otherwise) | |
| F5 iRule | 5536 |
same as F5 IPI |
f5_irule | firewall | IDPS/Malware Sandbox Events (dev_type: /threat/), Traffic (dstip), Syslog (otherwise) |
| F5 L7 DDoS | 5536 |
same as F5 IPI |
f5_l7ddos | firewall | IDPS/Malware Sandbox Events (dev_type: /threat/), Traffic (dstip), Syslog (otherwise) |
| F5 Mitigation | 5536 |
same as F5 IPI |
f5_ddos | firewall | IDPS/Malware Sandbox Events (dev_type: /threat/), Traffic (dstip), Syslog (otherwise) |
| F5 NGINX | 5151 |
F5 custom format |
nginx |
weblogs |
Syslog |
| F5 Silverline | 5536 |
same as F5 IPI |
f5_silverline |
firewall |
IDPS/Malware Sandbox Events (dev_type: /threat/), Traffic (dstip), Syslog (otherwise) |
| F5 VPN | 5187 |
CSV |
f5_vpn |
vpn |
Syslog |
| F5 WAF | 5536 |
same as F5 IPI |
f5_waf |
waf |
IDPS/Malware Sandbox Events (dev_type: /threat/), Traffic (dstip), Syslog (otherwise) |
|
FatPipe Networks SD-WAN |
5583 |
FatPipe Networks custom format |
fatpipe_sd_wan |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Firepower Management Center |
5759 |
RFC 3164 + regex |
firepower_management_center |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Forcepoint - DLP (CEF) |
5143 |
CEF |
forcepoint_dlp |
dlp |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Forcepoint - Firewall (CEF) |
5143 |
CEF |
forcepoint |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Forcepoint Security (CEF) | 5143 |
CEF |
forcepoint |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Forescout | 5154 |
Forescout Technologies custom format |
forescout |
asset |
Syslog |
|
FortiADC |
5725 |
syslog priority + KVP |
fortinet_fortiadc |
netlogs |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Fortinet FortiAnalyzer | 5542 |
KVP |
forti_analyzer |
ndr |
IDPS/Malware Sandbox Events (vendor.attack_name), Traffic (dstip), Syslog (otherwise) |
|
Fortinet FortiAuthenticator |
5671 |
RFC 3164 |
fortinet_fortiauthenticator |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Fortinet FortiEDR |
5661 |
RFC 5424 + KVP |
fortinet_fortiedr |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Fortinet Forticloud FortiClient EMS Cloud Endpoint Management Services |
5682 |
regex + KVP |
fortinet_forticlient_ems |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Fortinet FortiGate | 5517 |
KVP |
fw_fortigate |
firewall |
Traffic (action), Syslog (otherwise) |
|
Fortinet Fortigate (CEF) |
5143 |
CEF |
fw_fortigate |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Fortinet FortiMail |
5616 |
regex + KVP |
forti_mail |
|
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Fortinet FortiSandbox |
5648 |
Fortinet custom format |
fortinet_fortisandbox |
asset |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Fortinet FortiWeb |
5642 |
sylog priority + KVP |
fortinet_fortiweb |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| FreeRADIUS |
5750 |
RFC 3164 + regex |
freeradius |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| FutureSystems WeGuardia SSL plus (SSL VPN) |
5651 |
regex + pipe-separated ( | ) KVP |
future_systems_weguardia_ssl_plus |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Graylog |
5569 |
(RFC 3164) regex (for Graylog format) |
graylog |
endpoint |
Windows Events (winlogevent), IDPS/Malware Sandbox (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Guardicore (CEF) |
5143 |
CEF |
guardicore |
cloudsec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
HanDreamnet VIPM |
5676 |
regex + KVP |
handreamnet_vipm |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
HAProxy |
5713 |
RFC 5424 + JSON |
haproxy |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Hewlett Packard UNIX |
5585 |
regex + KVP |
hp-ux |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Hillstone | 5514 |
Hillstone Networks custom format |
fw_hillstone |
firewall |
IDPS/Malware Sandbox Events log_type: threat), Traffic (log_type: traffic), |
|
HPE Nimble Storage |
5731 |
RFC 3164 + KVP |
hpe_nimble |
storage |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
HPE Switch |
5595 |
Hewlett Packard Enterprise custom format for switches |
hpe_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| HTTP ThreatLocker Zero Trust EPP |
5754 |
HTTP JSON (in an array) |
threat_locker_zero_trust |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| HTTP Winlogbeat |
5752 |
HTTP JSON |
winlogbeat |
endpoint |
Winlogevent (winlogevent), Syslog (otherwise) |
| IBM AS400 |
5632 |
ibm_i |
ibm_os_logs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
|
Impero ContentKeeper |
5670 |
syslog priority + JSON |
impero_contentkeeper |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Imperva - SecureSphere (CEF) |
5143 |
CEF |
imperva_secure_sphere |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Incapsula SIEM Integration (CEF) |
5143 |
CEF |
incapsula |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Indusface Web Application Firewall |
5582 |
JSON |
indusface_waf |
waf |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Infoblox Data Connector (CEF) |
5143 |
CEF |
infoblox |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Infoblox Network Identity OS (NIOS) |
5587 |
Infoblox custom format |
infoblox_nios |
dnssec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Infocyte HUNT (CEF) |
5143 |
CEF |
infocyte |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
IPFIX |
4739 (UDP only) |
NetFlow v5, v9, v10 |
ipfix |
traffic |
Traffic |
|
IRONSCALES (CEF) |
5143 |
CEF |
ironscales_irontraps |
|
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Ivanti Connect Secure |
5756 |
RFC 5424 + regex |
ivanti_connect_secure |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Ivanti Endpoint Manager |
5757 |
RFC 5424 + regex |
ivanti_endpoint_manager |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Ivanti Pulse Secure |
5712 |
RFC 5424 + JSON |
ivanti_pulse_secure |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Jsonar Database Security Tool |
5586 |
JSON |
jsonar_db_security_tool |
dblogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Juniper SRX | 5173 |
KVP |
fw_juniper_srx |
firewall |
Traffic (srcip), Syslog (otherwise) |
| Juniper SSG | 5516 |
Juniper Networks custom format |
fw_juniper_ssg |
firewall |
Traffic (srcip), Syslog (otherwise) |
|
Juniper Switch |
5591 |
Juniper Networks custom format |
juniper_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
KasperskyLab (CEF) |
5143 |
CEF |
kasperskylab |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Kaspersky Security Center |
5723 |
RFC 5424 + KVP |
kaspersky_security_center |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
KeeperSecurity Enterprise |
5710 |
RFC5425 + JSON |
keeper_security_enterprise |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Kemp Technologies Load Master LB |
5695 |
RFC 5424 + Description |
kemp_technologies_load_master_lb |
weblogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Keycloak |
5653 |
RFC 5424 + KVP (values can be JSON) |
keycloak |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Kubernetes (HTTP JSON) |
5200 (TCP only) |
JSON |
kubernetes |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Lancope - StealthWatch (LEEF) |
5522 |
LEEF |
lancope_stealthwatch |
firewall |
Traffic (srcip), Syslog (otherwise) |
|
LanScope Cat |
5588 |
MOTEX custom format |
lanscope_cat |
endpoint |
Syslog |
|
Lepide |
5607 |
Lepide Software custom parser |
lepide |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Libraesva Email Security Gateway (ESG) |
5742 |
RFC 3164 + regex |
libraesva_esg |
|
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise |
|
Linux Audit |
5697 |
Linux Audit custom format |
linux_audit |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Linux Syslog | 5555 |
RFC 3164 or RFC 5424 + regex |
linux_syslog |
unixlogs |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| LiquidFiles |
5753 |
RFC 3164 + JSON |
liquid_files |
miscs |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Logstash Suricata |
5629 |
regex + KVP (JSON values) |
logstash_suricata |
ndr |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Mailboarder Agent |
5580 |
RFC 3164 + regex |
mailboarder_agent |
|
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Mako Networks firewall | 5547 |
RFC 3164 + regex |
mako_fw |
firewall |
Traffic (dstip), Syslog (otherwise) |
|
ManageEngine ADAudit Plus |
5679 |
regex + KVP |
manageengine_adaudit_plus |
iam |
Windows Events |
| ManageEngine ADAuditPlus (CEF) | 5143 |
CEF |
manageengine |
iam |
Windows Events |
|
McAfee (CEF) |
5143 |
CEF |
If Web Gateway is in the product name, dev_type is set to: mcafee_web_gateway Otherwise the value is determined from the CEF vendor field |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
McAfee Advanced Threat Defense |
5584 |
JSON |
mcafee_atd |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| McAfee ePolicy Orchestrator | 5533 |
RFC 5424 + XML |
mcafee_epo |
endpoint |
Traffic (srcip), Syslog (otherwise) |
| McAfee Firewall | 5169 |
KVP |
mcafee_firewall |
firewall |
Traffic (srcip), Syslog (otherwise) |
| McAfee Network Security | 5527 |
McAfee custom format |
mcafee_ns |
ipds |
Traffic (srcip), Syslog (otherwise) |
|
McAfee Proxy |
5739 |
RFC 3164 + KVP |
mcafee_proxy |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
MCAS SIEM Agent (CEF) |
5143 |
CEF |
mcas |
firewall |
Windows Events |
| Medigate |
5631 |
RFC 5424 + regex + JSON; or RFC 3164 + regex + JSON |
medigate |
iotsec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Melapress WordPress |
5714 |
melapress_wordpress |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
| Menlo Security MS-XL50M |
5630 |
regex (RFC 5424) + KVP |
menlo |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Microsoft IIS |
5636 |
SSV |
microsoft_iis |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Microsoft IIS (Syslog JSON) | 5142 |
syslog + JSON |
json |
weblogs |
Syslog |
|
Microsoft Office 365 |
5627 |
JSON |
office365 |
office_suite |
Windows Events |
| Microsoft Windows Event |
5646 |
regex + XML |
microsoft_windows_event |
endpoint |
Windows Events (winlogevent), Syslog (otherwise) |
|
Microsoft Windows via Graylog |
5569 |
(syslog header) + regex or JSON |
microsoft_windows |
endpoint |
Windows Events (winlogevent) |
| MicroWorld eScan |
5645 |
regex + KVP |
microworld_escan |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| MikroTik firewall and router | 5553 |
RFC 3164 + regex |
mikrotik |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Minerva Labs (CEF) |
5143 |
CEF |
minerva_labs |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
MONITORAPP AI WAF 4.1 |
5613 |
MONITORAPP custom format |
monitorapp_ai_waf |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| MONITORAPP WAF 1.0 | 5535 |
syslog (regex) |
monitor_app |
websec |
Traffic (srcip), Syslog (otherwise) |
|
Nasuni |
5592 |
Nasuni custom format |
nasuni |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
NetApp |
5608 |
NetApp custom format |
netapp |
dblogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Netfilter | 5544 |
RFC 3164 + KVP |
netfilter |
netlogs |
Traffic (dstip), Syslog (otherwise) |
| Netgear Full Managed Switches M4300 |
5749 |
RFC 3164 + regex |
netgear_full_managed_switches |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| NetIQ - Identity Manager |
5143 |
CEF |
netiq_identity_manager |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| NetIQ Access Manager | 5167 |
JSON |
access_manager |
iam |
Syslog |
| NetIQ SSO | 5171 |
KVP |
netiqsso |
iam |
Syslog |
| Netman Smart NAC |
5650 |
regex + pipe-separated ( | ) values |
netman_smart_nac |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| NetMotion |
5641 |
RFC 5424 |
absolute_netmotion |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Nutanix NX |
5724 |
RFC 3164 + vendor header + KVP |
nutanix_nx |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
NVIDIA Mellanox Switch |
5734 |
NVIDIA custom format |
nvidia_mellanox_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
NXLog (Also see Crib, above) |
5601 |
JSON (regex) |
nxlog |
paas |
Windows Events (winlogevent), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
OneLogin |
5581 |
JSON |
one_login |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| OpenCanary |
5638 |
regex + JSON |
opencanary |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
OpenLDAP (for Cisco ESA, use 5562) |
5164 |
OpenLDAP custom format |
openldap_style |
|
Syslog |
| OpenShift | 5573 |
RFC 5424 + (regex, JSON values) |
redhat_openshift |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| OpenVPN |
5643 |
OpenVPN custom format |
openvpn |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
OPNsense |
5660 |
RFC 3164 |
opnsense |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Oracle DB | 5170 |
CSV |
oracle |
dblogs |
Traffic (srcip), Syslog (otherwise) |
|
Oracle Solaris |
5664 |
RFC 3164 or RFC 5424 + regex |
oracle_solaris |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Ordr Connected Device Security |
5622 |
syslog + regex + JSON |
ordr_cds |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
PacketFence |
5686 |
regex + description |
packetfence |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Palo Alto Networks Next Generation Firewall (LEEF) | 5522 |
LEEF |
fw_palo_alto |
firewall |
Traffic (srcip), Syslog (otherwise) |
| Palo Alto Networks - Traps Agent (CEF) |
5143 |
CEF |
palo_alto_networks_traps_agent |
xdr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Palo Alto Networks Next-Generation Firewall and Panorama (BSD syslog and CSV) |
5515 |
BSD syslog + CSV |
fw_palo_alto |
firewall |
Traffic (type: traffic), IDPS/Malware Sandbox Events (type: threat), Syslog (otherwise) |
|
Palo Alto Networks Firewall via Graylog |
5569 |
(syslog header) + regex or JSON |
fw_palo_alto |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Palo Alto Networks Prisma Cloud (Compute Edition) |
5720 |
RFC 3164 (with RFC 5424 for timestamp) + KVP |
palo_alto_networks_prisma_cloud |
cloudsec |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Penta Security WAPPLES WAF | 5560 |
KVP |
penta_security_wapples |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Pentera Appliance |
5737 |
regex + KVP |
pentera_appliance |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Peplink XDR |
5665 |
RFC 5424 + KVP |
peplink_xdr |
xdr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Perception Point X-Ray |
5667 |
RFC 5424 + KVP |
perceptionpoint_xray |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| pfSense Firewall | 5543 |
RFC 3164 or RFC 5424 |
pfsense_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog |
|
PIOLINK WEBFRONT-K |
5617 |
regex + KVP |
piolink_webfront_k |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
PNPSECURE NODESAFER
|
5711 |
(syslog priority + version + timestamp + hostname) + JSON |
pnpsecure_nodesafer |
dblogs |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| PrintChaser | 5179 |
CSV |
printchaser |
dlp |
Syslog |
| Pritunl |
5748 |
JSON |
pritunl |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Privacy-i | 5178 |
CSV |
privacy |
dlp |
Syslog |
| Proofpoint |
5596 |
Proofpoint custom format |
proofpoint |
|
Syslog |
|
Prophaze WAF |
5733 |
RFC 3164 + RFC 5424 timestamp + JSON |
prophaze_waf |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Pulse Secure | 5534 |
RFC 5424 + (regex) |
pulse_secure |
vpn |
Syslog |
|
QNAP QTS |
5726 |
RFC 3164 + log type + KVP |
qnap_qts |
storage |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Qumulo Core |
5704 |
RFC 5424 + CSV |
qumulo_core |
storage |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Radware Alteon |
5700 |
RFC 3164 or RFC 5424 + description |
radware_alteon |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
|
Radware DefensePro |
5619 |
Radware custom format |
radware_defense_pro |
idps |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Rapid7 | 5153 |
KVP |
rapid7 |
security_scan |
Syslog |
| RazLeeSecurity - Audit (CEF) |
5143 |
CEF |
ibm_raz_lee_security |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Relianoid WAF |
5730 |
RFC 3164 + regex |
relianoid_waf |
waf |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| RSA Authentication Manager | 5184 |
CSV |
rsa_auth |
nsa |
Syslog |
|
Ruckus ZoneDirector |
5662 |
RFC 3164 or RFC 5424 |
ruckus_zone_director |
wireless |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
RuiJie Switch |
5689 |
regex + (custom value) + timestamp + (hostname) + %facility-severity-mnemonic + description |
ruijie_switch |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| SafePC | 5180 |
CSV |
safepc |
cloudsec |
Syslog |
|
Sangfor EDR |
5701 |
regex + (RFC 3164) + JSON |
sangfor_edr |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Sangfor NGAF |
5637 |
regex + (RFC 3164 + KVP |
sangfor_ngaf |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Sectona PAM |
5721 |
regex + CSV |
sectona_pam |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| SECUi Firewall | 5561 |
RFC 5424 + KVP |
secui_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| SECUi MF2 Firewall | 5570 |
RFC 5424 + (regex) |
secui_mf2 |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| SECUi MFD | 5611 |
SECUi custom format |
secui_mfd |
idps |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Secureki APPM |
5693 |
RFC 3164 + regex |
secureki_appm |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Security Strategy Research (SSR) Metieye |
5572 |
SSR custom format |
ssr_metieye |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Secuwiz Secuway SSLVPN |
5652 |
Secuwiz custom format |
secuwiz_secuway_sslvpn |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
SentinelOne (CEF2) |
5175 |
CEF |
cef_device_vendor |
endpoint |
Traffic (srcip), Syslog (otherwise) |
|
SentinelOne Mgmt (CEF) |
5143 |
CEF |
sentinelone_endpoint |
endpoint |
IDPS/Malware Sandbox Events (threat, normalized from classification), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
SentinelOne Security Center (CEF) |
5143 |
CEF |
sentinelone_endpoint |
endpoint |
IDPS/Malware Sandbox Events (threat, normalized from classification), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
SentinelOne Singularity Mobile |
5623 |
syslog + regex + JSON |
sentineone_sm |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ServiceNow Now Platform |
5668 |
RFC 3164 + KVP |
servicenow_nowplatform |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ShareTech Firewall |
5609 |
ShareTech custom format or KVP |
sharetech_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Snare Agent |
5590 |
Prophecy International Holdings custom format |
snare_agent |
paas |
Windows Events (winlogevent), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Sniper IPS | 5182 |
KVP |
sniperips |
idps |
Traffic (srcip), Syslog (otherwise) |
| SonicWall - NSA 2400 (CEF) |
5143 |
CEF |
sonicwall_nsa |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| SonicWall Firewall | 5152 |
syslog + KVP |
sonicfw |
firewall |
IDPS/Malware Sandbox Events (IDS signature), Traffic (srcip), Syslog (otherwise) |
| SonicWall VPN | 5556 |
RFC 3164 + regex |
sonicwall_vpn |
vpn |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Sophos (CEF) |
5143 |
CEF |
sophos |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Sophos endpoint | 5565 |
regex + KVP |
endpoint_sophos |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Sophos endpoint (beats) | 5044 |
JSON (Beats) |
endpoint_sophos |
endpoint |
Traffic (srcip), Syslog (otherwise) |
| Sophos firewall | 5520 |
KVP |
fw_sophos |
firewall |
Data goes to the indicated index based on the log_type:
|
|
Sophos Web Appliance |
5626 |
Sophos custom format or KVP |
sophos_web_app |
websec |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Splashtop |
5698 |
regex + JSON |
splashtop |
asset |
Traffic (srcip, srcport, dstip, dstport, and proto) Syslog (otherwise) |
| Splunk Heavy Forwarder | 5188 |
Splunk custom format |
splunk_forwarder |
netmgmt |
Syslog |
|
Stormshield Net Security Firewall |
5625 |
Stormshield custom format or KVP |
stormshield_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Symantec Endpoint Protection | 5525 |
Symantec custom format |
symantec_ep |
endpoint |
Traffic (dstip), Syslog (otherwise) |
| Symantec Firewal | 5155 |
Symantec custom format |
symantec |
firewall |
Syslog |
| Symantec Messaging Gateway | 5567 |
Symantec custom format |
symantec_messaging_gateway |
|
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Symantec DLP (CEF) | 5143 |
CEF |
symantec |
symantec_dlp |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Synology Directory Server |
5597 |
Synology custom format |
synology_directory_server |
asset |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Syslog4Net |
5715 |
syslog (regex) |
syslog4net |
log_processing |
Windows Events (winlogevent), Syslog (otherwise) |
|
Thales Group CipherTrust Manager |
5674 |
RFC 3164 + local header + CEF header + message with JSON |
thales_cipher_trust_manager |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
ThreatLocker Zero Trust EPP |
5200 (TCP only) |
JSON (in an array) |
threat_locker_zero_trust_epp |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Trellix FireEye - CMS (CEF) |
5143 |
CEF |
fireeye_cms |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Trellix FireEye HX |
5644 |
regex |
fireeye_hx |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Trellix FireEye - MPS (CEF) |
5143 |
CEF |
fireeye_mps |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Trend Micro - Deep Security Agent (LEEF) | 5522 |
LEEF |
trendmicro_dsa |
endpoint |
Traffic (srcip), Syslog (otherwise) |
|
Trend Micro Apex Central (CEF) |
5143 |
CEF |
trendmicro_apex_central |
endpoint |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Trend Micro Interscan Messaging |
5678 |
TSV |
trend_micro_interscan_messaging |
saas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Trend Micro Proxy | 5540 |
syslog (regex) |
trendmicro_proxy |
websec |
Traffic (dstip), Syslog (otherwise) |
|
Trend Micro TippingPoint |
5672 |
syslog priority + syslog timestamp + TSV |
trend_micro_tippingpoint |
idps |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Tripwire Enterprise | 5186 |
KVP |
tripwire |
endpoint |
Syslog |
| Ubiquiti UAP-AC-Pro | 5552 |
RFC 3164 (with hostname) + regex |
ubiquiti |
netlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
UMV WSS (Web Server Safeguard) |
5709 |
RFC 3164 + regex |
umv_wss |
ndr |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Unix |
5633 |
(RFC 3164) + regex |
unix |
unixlogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Untangle Firewall (Syslog JSON) |
5142 |
syslog + JSON |
json |
firewall |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Varonis DatAdvantage (CEF) | 5143 |
CEF |
varonis_datadvantage |
dlp |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Vectra AI Platform |
5738 |
RFC 3164 + KVP |
vectra_ai_platform |
xdr |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Veeam Backup & Replication |
5751 |
RFC 5424 + regex, RFC 5424 + KVP |
veeam_backup_replication |
dlp |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Versa Networks Firewall | 5568 |
RFC 3164 or RFC 5424 + KVP |
versa_networks_fw |
firewall |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| VMware - Carbon Black (LEEF) | 5522 |
LEEF |
vmware_cb |
endpoint |
Traffic (srcip), Syslog (otherwise) |
|
VMware ESXi |
5600 |
VMware custom format |
vmware |
unixlogs |
Syslog |
|
VMware Horizon |
5687 |
RFC 5424 + description |
vmware_horizon |
paas |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| VMware NSX Edge Firewall |
5758 |
RFC 3164 + KVP (with Netfilter logs) |
vmware_nsx_edge_firewall |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| VMware NSX-T Data Center | 5574 |
regex + KVP (with JSON values) |
vmware_nsx_t |
endpoint (unless log type is dfwpktlogs, then category is firewall) |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
VMware UAG |
5620 |
VMware custom format |
vmware_uag |
iam |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
VMware Vcenter |
5615 |
VMware custom format |
vmware_vcenter |
itsm |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
VMWare VeloCloud SD-WAN |
5685 |
regex + KVP or message |
vmware_velocloud_sdwan |
netmgmt |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| WatchGuard - XTM | 5522 |
LEEF |
watchguard_fw |
firewall |
Traffic (srcip), Syslog (otherwise) |
| WatchGuard firewall security appliance | 5557 |
RFC 3164 + regex |
watchguard_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Wazuh SIEM |
5634 |
(regex) + JSON |
wazuh_siem |
endpoint |
Windows Events (winlogevent) , Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Windows DNS Server |
5599 |
Microsoft custom format |
windows_dns_server |
weblogs |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Windows Event NXLog |
5601 |
regex or JSON |
microsoft_windows |
endpoint |
Windows Events (winlogevent), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Windows System Security |
5610 |
Microsoft custom format |
windows_system_security |
endpoint |
Windows Events (winlogevent), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Wins IPS ONE-1 / Wins DDX | 5538 |
syslog with Splunk header + (regex) |
winsips |
idps |
IDPS/Malware Sandbox Events (vendor.attack_name), Syslog (otherwise) |
| WINS Sniper NGFW |
5649 |
regex + KVP |
wins_sniper_ngfw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Zeek (NXLog method) |
5142 |
JSON |
json |
json |
Syslog |
| Zix Mail | 5185 |
Zix custom format |
zix_mail |
|
Traffic (srcip), Syslog (otherwise) |
|
5143 |
CEF |
zscaler |
websec |
Syslog |
|
| Zscaler ZIA Firewall | 5549 |
JSON |
zscaler_zia_fw |
firewall |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Zscaler ZIA Web | 5550 |
JSON |
zscaler_zia_web |
weblogs |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
| Zscaler ZPA | 5551 |
JSON |
zscaler_zpa |
vpn |
IDPS/Malware Sandbox Events (threat), Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
|
Zyxel Firewall |
5594 |
regex + KVP |
zyxel_fw |
firewall |
Traffic (srcip, srcport, dstip, dstport, and proto), Syslog (otherwise) |
Parsers that Support Line Breaks in Messages Delivered over TCP
Most syslogs that are sent over TCP use ASCII LF (represented as \n) as a TRAILER character to terminate individual messages within the larger transmission. (This is the non-transparent-framing method described in section 3.4.2 in RFC 6587 - Transmission of Syslog Messages over TCP.) Unfortunately, if a log uses LF (\n) as a line break within a message, parsers recognize it as a TRAILER character and split it into multiple parts, depending on the number of line breaks involved. This results in the erroneous creation of multiple “messages” that are really just parts of one single message.
There are exceptions however. The following parsers can receive logs delivered over TCP with LF (\n) line breaks because these logs include fixed HEADER and TRAILER characters, which the parsers use to isolate messages:
-
Aliyun/AliCloud on port 5545
-
Avanan on port 5681
-
BeyondTrust BeyondInsight on port 5621
-
CheckPoint Firewall on port 5519
-
FortiADC on port 5725
-
Indusface Web Application Firewall on port 5582
-
Monitorapp on port 5535
-
Splunk Heavy Forwarder on port 5188
-
Veeam Backup & Replication on port 5751
-
Windows System Security on port 5610
-
The following HTTP JSON parsers that listen on TCP 5200 also support LF line breaks within syslog messages.
When only one product is sending logs to TCP 5200 on a sensor, the URL doesn’t need to include the product name to identify it. However, when there is more than one and you want to differentiate them, include the product name. Example for Avanan:
https://<sensor_ip_addr>:5200/httpjsonorhttps://<sensor_ip_addr>:5200/httpjson_avanan-
Avanan –
httpjsonorhttpjson_avanan -
Bitdefender –
httpjsonorhttpjson_bitdefender_multiple_event -
ECS Suricata –
httpjsonorhttpjson_ecsorhttpjson_ecs_suricata -
ECS Windows –
httpjsonorhttpjson_ecsorhttpjson_ecs_windows -
Egnyte –
httpjsonorhttpjson_egnyte -
Exium SASE –
httpjsonorhttpjson_exium_sase -
FS BIG-IP Telemetry –
httpjsonorhttpjson_fs_telemetry_streaming -
Kubernetes –
httpjsonorhttpjson_kubernetes -
ThreatLocker Zero Trust EPP –
httpjsonorhttpjson_threat_locker_zero_trust_epp
-
-
From 5.3.0, Stellar Cyber supports HTTP JSON on other ports besides 5200. The following parsers also receive logs formatted for HTTP JSON that contain LF line breaks within syslog messages:
-
HTTP ThreatLocker Zero Trust on port 5754
-
HTTP Winlogbeat on port 5752
-
In addition to the non-transparent-framing method to separate log messages, section 3.4.1 in RFC 6587 - Transmission of Syslog Messages over TCP describes another method: octet counting. The Fortinet FortiGate parser supports this as well as non-transparent-framing, checking the first character in a frame to determine which method is being used. If a log sent to the Fortinet FortiGate parser on TCP port 5517 contains an LF (\n) line break, then the octet counting method must be used. Otherwise, either method works.
In summary, only the parsers listed above can process logs that include \n and are sent over TCP. All parsers support logs sent over UDP because a UDP datagram contains just one syslog message inside; therefore, parsers don’t need to separate multiple syslog messages from a single transmission.