Configuring Receivers
Receivers are data objects in Stellar Cyber that represent the destination of data collected by Photon sensors and other data sources. Each Sensor Profile must refer to one or more receivers.
You must have Root scope to use this feature.
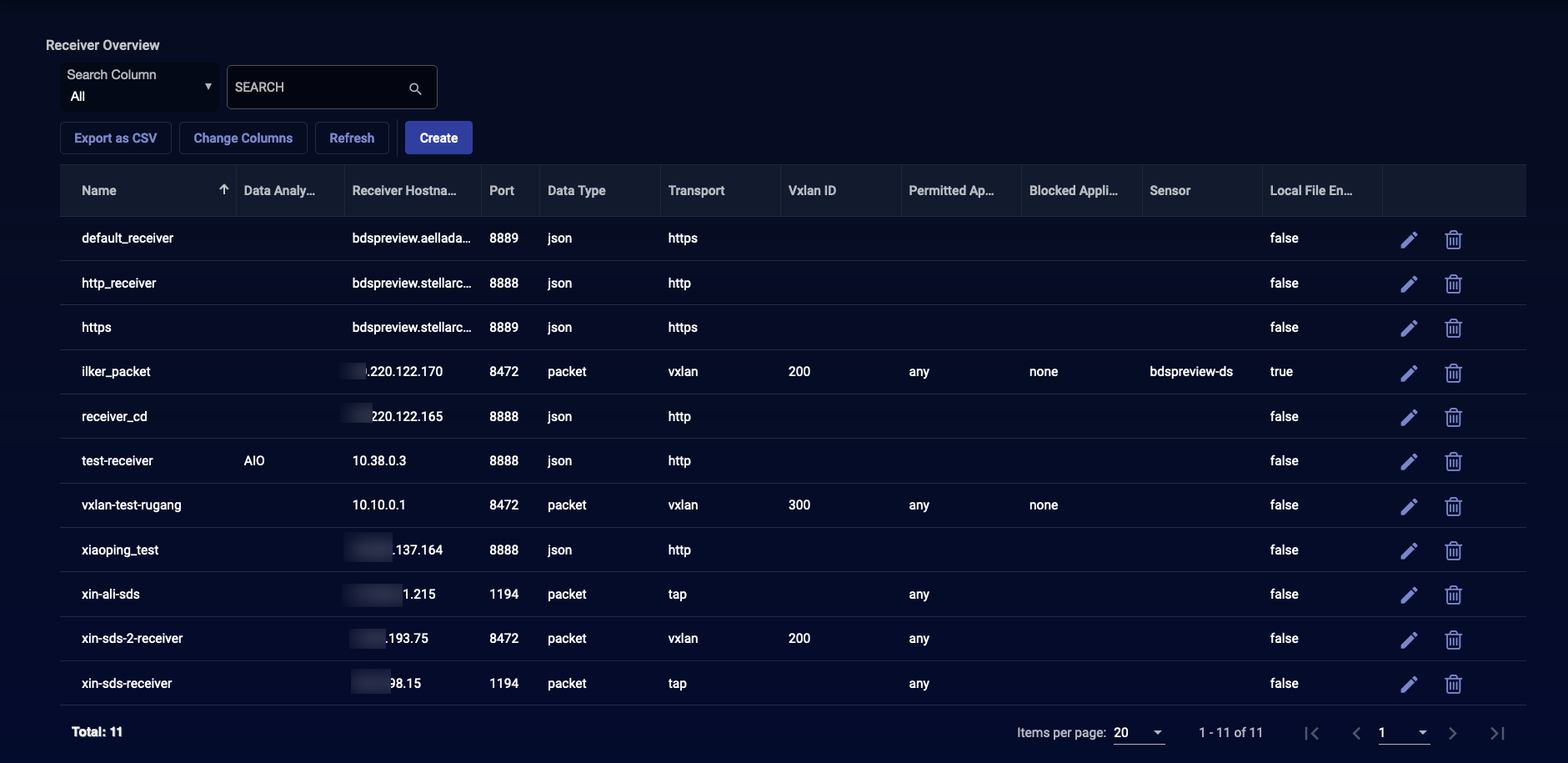
Receiver Overview
Click System | Receivers to see a list of the configured receivers.
-
Click Create to add a new receiver. A dialog box to add a receiver appears.
-
Click
 to edit the receiver on the corresponding row. A dialog box to edit the receiver appears.
to edit the receiver on the corresponding row. A dialog box to edit the receiver appears. -
Click
 to delete the receiver on the corresponding row.
to delete the receiver on the corresponding row.
Adding a JSON Receiver
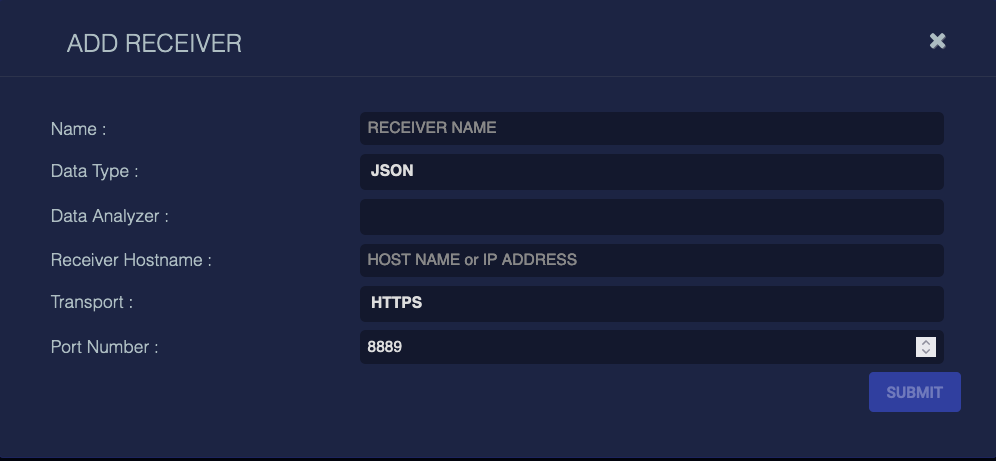
To add a JSON receiver, fill in the following fields:
-
Name– The name of the receiver. This value will be referred to by one or more sensor profiles. This field does not support multibyte characters.
-
Data Type – Choose JSON.
-
Data Analyzer – This field provides a selection list of available data analyzers. When one is selected, the IP address of the DA is entered into the following field. This field may be left blank.
-
Receiver Hostname – The DNS or IP address that will receive the packets. This field does not support multibyte characters.
-
Set this to the IP/hostname of the DP in an AIO deployment.
-
Set this to the IP/hostname of the Data Analyzer master (DA-Master) in a cluster deployment.
-
-
Transport – Either HTTP or HTTPS. When this value is changed the Port Number is set to the default value.
-
Port Number – The TCP/IP port number on the receiver host that will receive the packets.
HTTP sends packets over the network unencrypted. Depending on the physical path taken by these packets this may cause a security exposure.
Click Submit in the lower right corner of the dialog box to save the changes. Click the button in the upper right corner to dismiss the dialog box without saving the changes.
Adding a Packet Receiver
Linux Server Sensors can send packet data to legacy Security Sensors using VXLAN tunnels. This setup uses a packet-mode receiver as shown in this section. Once the receiver is set up it can be used in a profile that enables packet forwarding. The overall configuration looks like this:
-
The sending Linux Server Sensor uses a Standard Server Sensor profile configured with two receivers:
-
A JSON receiver for standard analysis tasks.
-
A Packet receiver with a Transport of VXLAN that specifies the destination for forwarded traffic in the Receiver Hostname field once Packet Forwarding is enabled.
-
The sending Linux Server Sensor also has Packet Forwarding enabled in its Standard Sensor Profile.
-
-
The receiving legacy Security Sensor has a Packet receiver with VXLAN enabled.
This configuration is only supported using a legacy Security Sensor as the VXLAN destination. You cannot use a Modular Sensor with the Sandbox and IDS features enabled as the destination.
If you configure a packet receiver with a legacy Security Sensor destination that does not have a span port configured, that sensor will not ingest files (for malware and IDS analysis) from its own traffic. For the sensor to ingest files, you must do one of the following:
- Configure another Security Sensor (or a Modular Sensor with the Sandbox and IDS features enabled) and forward traffic to that one.
- Remove the receiver (if it's not being used).
- Point the receiver at another sensor.
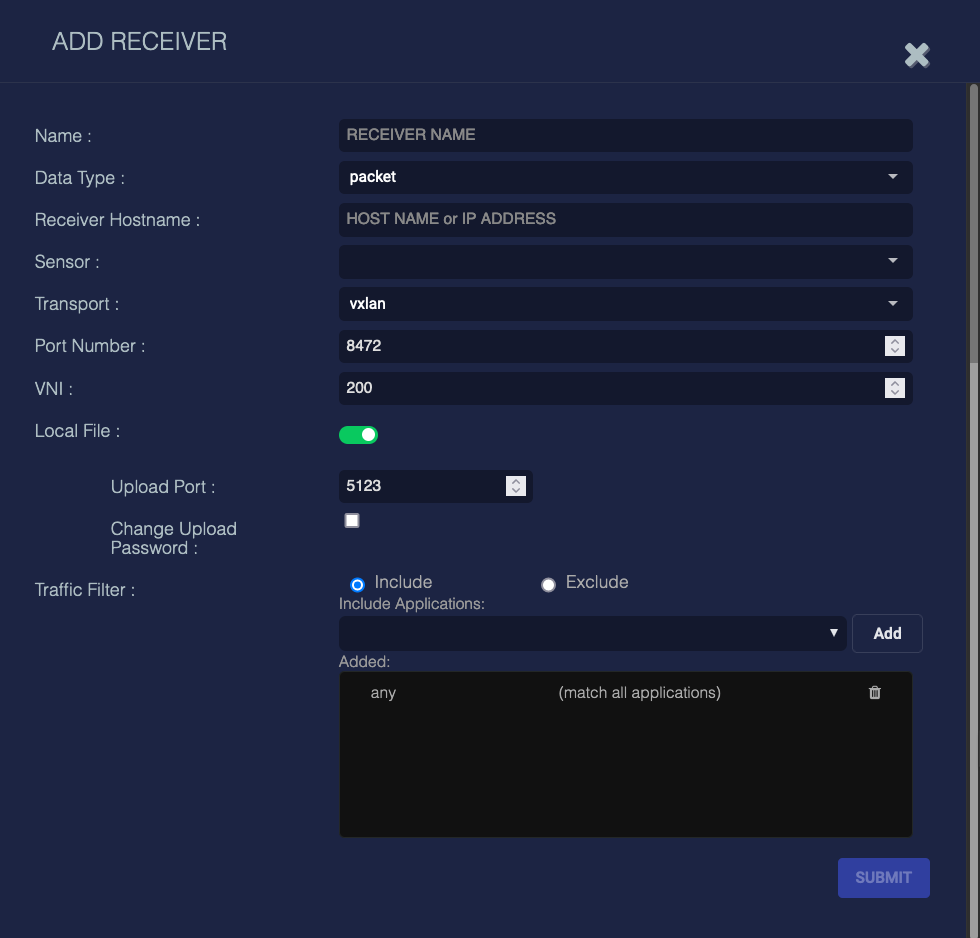
To add a packet receiver, fill in the following fields:
-
Name—The name of the receiver. This field does not support multibyte characters.
-
Data Type—Either JSON or packet. Choose packet.
-
Receiver Hostname—The DNS or IP address of the system that will receive the packets. This field is only required if the selection in the following field is "Third Party." This field does not support multibyte characters.
-
Sensor—This provides a selection of all available sensors. The selected sensor must be a security sensor or a "Third Party."
-
Transport—Currently set only to the value vxlan.
-
Port Number—The TCP/IP port number that will receive the packets. The two choices are usually 4789 or 8472.
-
VNI—The Virtual Network Interface. This value should be left at the default of 200.
-
Local File—This assembles files on the sensor and sends the files via TLS to the legacy Security Sensor. Since this action requires the sensor to process the files, enabling it can impact performance. When this field is toggled on, the additional fields for Upload Port and to Change Upload Password are displayed.
Local file assembly only works on sensors with the Network Traffic feature enabled. Enabling it disables file assembly on the associated Security Sensor. Do not enable local file assembly if there are other server sensors sending data to the Security Sensor.
-
Upload Port—The UDP port number of the target device that will receive packets. Default is 5123.
-
Change Upload Password—When checked this enables the password fields.
-
Password/Reenter Password—These fields are used to set the password that the sensor will use when sending packets to the target sensor.
-
-
Traffic Filter—Stop forwarding (filter) IDS and malware traffic for the selected applications. If the VXLAN has too much traffic, use this filter to limit the traffic sent. To configure the traffic filter:
-
Choose whether to Include or Exclude.
If you have a small subset of applications to include, choose Include. You must explicitly include all applications you want to monitor. If an application is not included, its traffic is filtered out. The default is any.
If you want to include most applications and exclude a subset, choose Exclude. If an application is excluded, its traffic is filtered out. The default is none.
-
Choose an application from the Include/Exclude Applications drop-down. Start typing and Stellar Cyber narrows down the list.
-
Click Add. The application is immediately added to the Added field. The first application you add replaces the default.
-
Add as many applications as you want.
-
Click the to remove an application from the list.
-
Click Submit. The receiver is updated.
-