Vendor-Related Metadata
When Stellar Cyber ingests data, some of the information is stored in standardized fields (example: srcip) within the Interflow record. The table below shows a set of the standard fields that you may find helpful for identifying vendor-specific data in the searches or queries that you build.
| Metadata Field | Purpose | Examples |
|---|---|---|
| msg_origin.vendor |
Vendor associated with the data |
trendmicro |
| msg_origin.source | Vendor's product name associated with the data | trendmicro_cloudone |
| msg_origin.category |
Overall data category |
endpoint |
|
msg_origin.processor.name |
For connectors, this is the same as msg_origin.source |
trendmicro_cloudone |
|
msg_origin.processor.type |
For connectors, this is always log_collector |
log_collector |
| msg_class | Sub-category of data applicable to multiple content types from a vendor |
trendmicro_cloudone_computers |
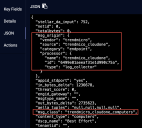
These metadata fields can be viewed in the JSON tab.
Vendor-Specific Data
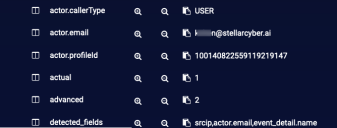
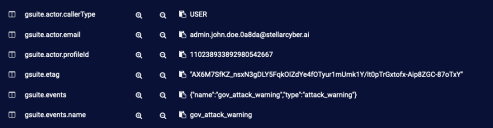
In addition to standard metadata fields in the Interflow record, Stellar Cyber dynamically creates fields to store vendor-specific data. In earlier releases, these were created with their functional field name, so a search for the value would benefit from a compound query such as: msg_origin.source:gsuite AND actor.email:badguy@someco.com. Later releases have these fields nested under the vendor name, which simplifies searches - the previous example could be found using gsuite.actor.email:badguy@someco.com.
| Example Interflow without vendor label | Example Interflow with vendor label |
To learn which fields may be useful for your queries, expand the Interflow details in views such as the Investigate | Threat Hunting Documents table. Locate the vendor name and note the fields. Repeat this with different Interflow rows, since Stellar Cyber does not typically create the fields if the incoming value is blank.