Working with the Connectors Table
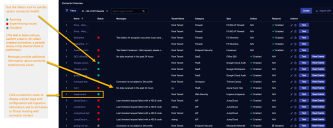
Stellar Cyber can connect to other resources in your network. This allows you to collect information from your IdP, endpoint security, vulnerability scanners, and other systems, as well as to push actions to your firewalls. The connectors table lists all connectors that have been configured.
The table itself behaves like all other Stellar Cyber tables. You can change the displayed columns, sort by columns, and export the displayed list, for example. This table also includes a Last Activity column, which the timestamp for the last successful activity for that connector. ![]()
For a list of connectors and their supported functions, refer to: Connector Types & Functions.
Use this topic to understand how to:
- Add a new connector
- Edit an existing connector
- Test a connector
- Delete a connector
- Analyze connector details / statistics
- View full connector details
For guidance ingesting log data, refer to Ingesting Logs.
Adding and Editing Connectors
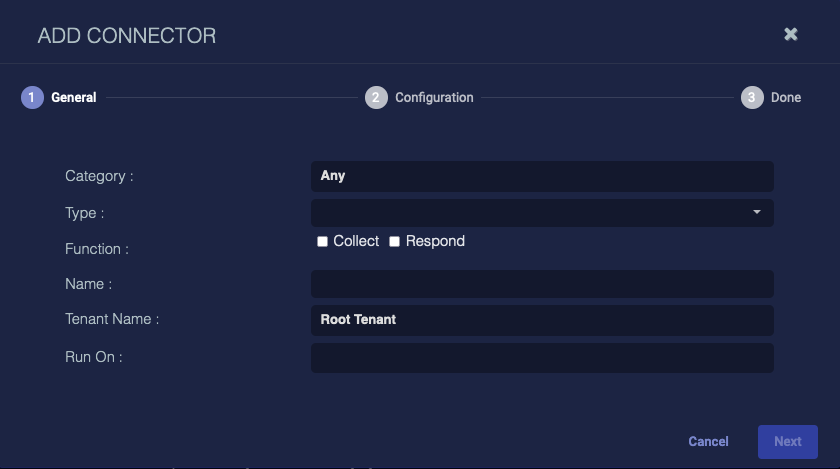
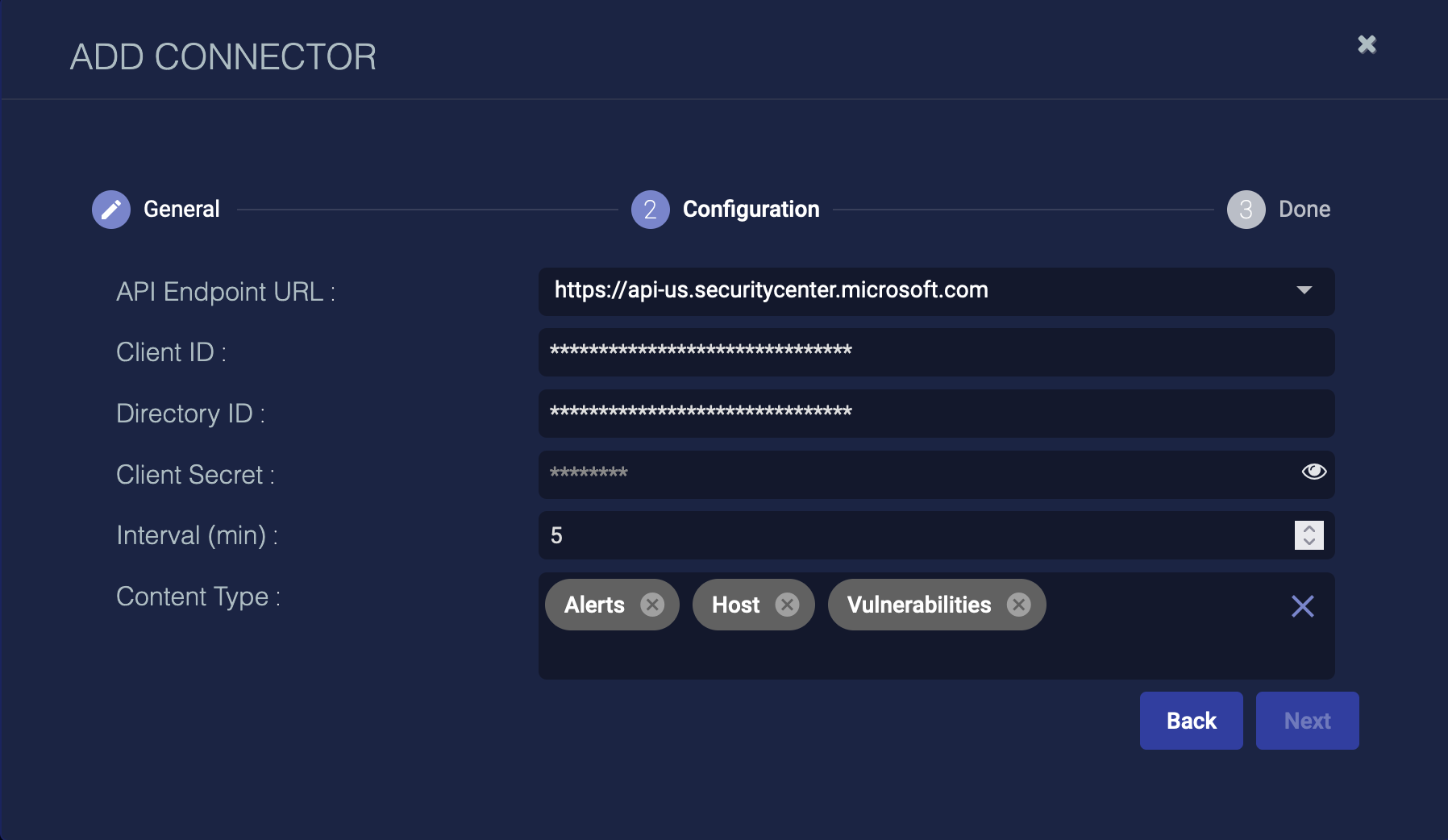
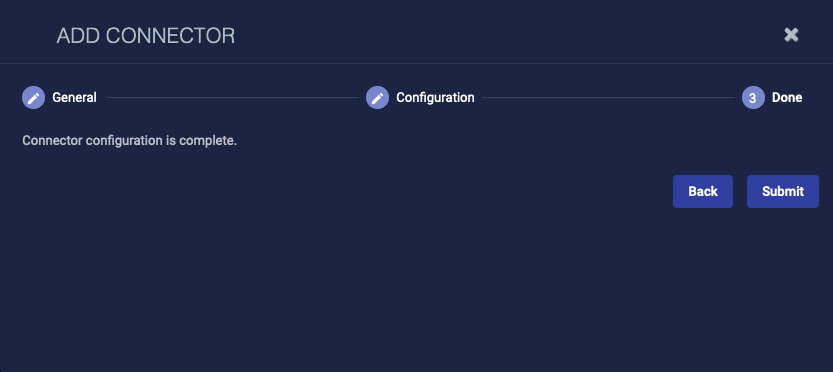
Adding and editing provide the same configuration options; the only difference is that you can't edit the General configuration options. Click Create to create a new connector or ![]() to edit an existing connector. After you have obtained the credentials for your external service and configured API or other access for Stellar Cyber community, there are three basic steps to configuring a connector in Stellar Cyber.
to edit an existing connector. After you have obtained the credentials for your external service and configured API or other access for Stellar Cyber community, there are three basic steps to configuring a connector in Stellar Cyber.
For detailed steps on obtaining credentials, configuring, and testing specific connectors, select your connector from the Connector Types & Functions.
For a quick overview, click through the slides below:
Testing a Connector
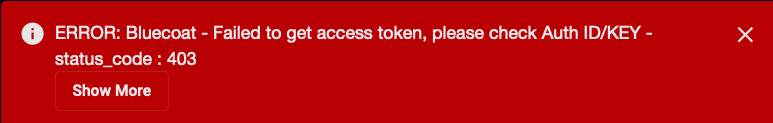
When you add (or edit) a connector, we recommend that you run a test to validate the connectivity parameters you entered. (The test validates only the authentication / connectivity; it does not validate data flow).
-
Click System | Integrations | Connectors. The Connector Overview appears.
-
Locate the connector that you added, or modified, or that you want to test.
-
Click Test at the right side of that row. The test runs immediately.
Note that you may run only one test at a time.
Stellar Cyber conducts a basic connectivity test for the connector and reports a success or failure result. A successful test indicates that you entered all of the connector information correctly.
To aid troubleshooting your connector, the dialog remains open until you explicitly close it by using the X button. If the test fails, you can select the button from the same row to review and correct issues.
The connector status is updated every five (5) minutes. A successful test clears the connector status, but if issues persist, the status reverts to failed after a minute.
Repeat the test as needed.
Deleting a Connector
To delete a connector you must first remove it from the data analyzer profile (firewall and vulnerability scanner connectors are not included in data analyzer profiles, so can skip these steps):
-
Click System | Data Processor | Data Analyzer Profile.
-
Click the
 button next to the profile containing the connector. The EDIT DATA ANALYZER PROFILE screen appears.
button next to the profile containing the connector. The EDIT DATA ANALYZER PROFILE screen appears. -
Find the connector in the Added field under Optional Data Source.
-
Click next to the connector. The connector is immediately removed.
-
Click Submit. The profile is saved, and the connector is no longer in use.
When the connector is removed from all data analyzer profiles, you can delete it:
-
Click System | Integration | Connectors.
-
Click next to the connector you want to delete. A confirmation dialog box appears.
-
Click OK. The connector and configuration information are immediately deleted.
If you see a warning that Data source is in use, cannot be deleted, the connector is still in a data analyzer profile. Remove it from all profiles.
Analyzing Connector Details
Connectors send statistics to the DP, quantifying the data being sent and its source once per minute. This data is stored in the Sensor Monitoring (aella-ade) index on the DP. You can analyze this data using the Threat Monitoring interface (see procedure below). ![]() , from which you can also jump to the Threat Monitoring interface, with context. Access Connector Details by clicking the name of the connector from the connector list.
, from which you can also jump to the Threat Monitoring interface, with context. Access Connector Details by clicking the name of the connector from the connector list.
-
Log in to Stellar Cyber.
-
Navigate to Investigate | Threat Hunting.
-
Click the Indices dropdown and make sure that the Sensor Monitoring index is selected.
-
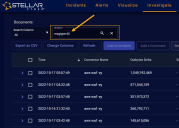
Scroll down to the Document table, enter msgtype:40 in the Search field, and press Enter to filter on just this msgtype. This is the msgtype that quantifies ingestion by connector.
-
The table updates to show all entries passing the global filters at the top of the display for Message Type 40. You can add the Connector Name column to see where the data came from.
The other key fields to look for are as follows:
-
engid_name—the name of the connector
-
http_code—the return code from the API
-
in_bytes_delta—the size of the events pulled
-
in_records_delta—the number of events sent to the DP
-
out_bytes_delta—the size of the messages pulled
-
out_records_delta—the number of events sent to the DP
-
Viewing Full Connector Details
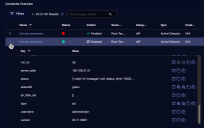
Click the down arrow on the Connector Overview page to view full details for a connector.
Some of the fields are as follows:
Fields do not display if they are None or if they do not apply.
-
category—the connector category, for example, idp, email, firewall
-
content_type—the content type of the logs, for example, ["events"] or ["threats"]

-
interval—the configured interval
-
log_type—the type of log, for example, ad (Active Directory) or proofpoint_tap
-
run_on—the device on which the connector runs, for example, dp (Data Processor)
-
status—the information about the status:
{"code":3,"message":"No data received in the past 24 hours","status_time":"2023-11-02 11:24:26"}
-
code—the status code from 0 to 4 as follows:
CONNECTOR_HEALTHY_CODE = 0
CONNECTOR_NOT_ADDED_TO_DA_CODE = 1
CONNECTOR_ACTIVITY_FAIL_CODE = 2
CONNECTOR_NO_DATA_CODE = 3
CONNECTOR_TEST_FAIL_CODE = 4
-
message—the status message associated with the code
-
status_time—the status timestamp
-