ATH Example: Blocking a Port Scanning Source IP 
This topic describes how to create an ATH playbook that notifies you when a source IP is detected pinging a specified destination IP on more than 20 destination ports. This is known as port scanning and is a common technique used to identify open ports on a target host.
This example also provides a demonstration of how to use nested calculations in an ATH playbook.
Configure the Alert
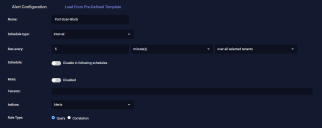
We will create an alert that runs a query every 5 minutes on the Traffic index.
To create the alert:
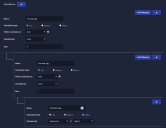
- Navigate to Respond | Automation and click the Create button to add a playbook.
- Enter a name for the playbook. We entered Port-Scan-Block.
- Set the Schedule type to interval.
- Set it to run every five minutes over all selected tenants.
- Leave Mute disabled.
- Choose the tenants and tenant groups on which to run. We chose All Tenants.
- Set the index to Traffic.
- Leave the Rule Type as Query.
Build a Query
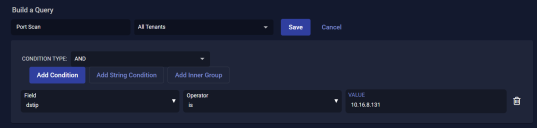
We want a query that looks for new documents with a dstip of 10.16.8.131. This is the IP address that we are concerned is the target of port scan attacks.
To build the query:
- Click New Query. The screen changes to Build a Query.
- Enter a Query Name. We used Port Scan.
- Leave Condition Type set to AND and click Add Condition.
- Select dstip from the Field dropdown.
- Leave the Operator set to is.
- Set Value to 10.16.8.131.
- Click Save to save your query.
Add Calculations to the Query
Next, we will build a series of nested calculations that ensure we're matching the top five source IP addresses that are pinging 10.16.8.131 on more than 20 destination ports.
To add the nested calculations:
-
Click Calculations to enable them, changing the slider to green.
-
Click the + button to add a calculation.
-
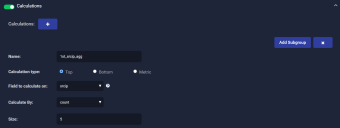
Our top-level calculation matches the top five source IP addresses sending to 10.16.8.131:
-
Click Add Subgroup to add a nested calculation for the top destination IP address.
-
Supply a Name. We used 2nd_dstip_agg.
-
Leave Calculation type set to Top.
-
Set the Field to calculate on dropdown to dstip.
-
Leave Calculate By set to count.
-
Set Size to 1. We are looking for just one dstip in this query (10.16.8.131). If your query is for multiple dstips, you can set this to a larger size.
Here's where we are now:
-
-
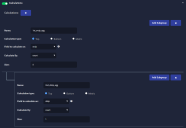
Click Add Subgroup to add a third nested calculation that matches source IPs sending to more than 20 destination ports.
-
Supply a Name. We used 3rd_dstport_agg.
-
Set Calculation type to Metric.
-
Set the Field to calculate on dropdown to dstport.
-
Set Calculate By to unique count of dstport.
-
Here's how our playbook looks with all three calculations added:
Configure a Condition
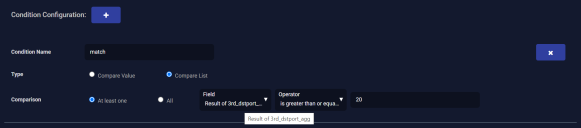
We are looking for hosts pinging 10.16.8.131 on more than 20 ports. To do this, we add a condition that triggers if the count of our third calculation (Result of 3rd_dstport_agg) is greater than or equal to 20.
To configure this condition:
- Enter a Condition Name. We entered match.
- Select Compare List for the Type.
- Set the Comparison to At least one.
- Set Field to Result of 3rd_dstport_agg.
- Set Operator to is greater than or equal to 20.
Configure Actions
Finally, you must configure a Firewall/Security Switch action to block the IP address when the match condition you configured in the previous section is detected. Refer to Configuring Firewall/Security Switch Actions for details on configuring this type of action. When you have finished, click Submit to add your new playbook to the list.