Installing a Windows Server Sensor
This topic describes how to install a Windows Server Sensor in a supported target environment using the installation file downloaded from the Download Images tab in the System | Deployment | Sensor Installation page. Refer to the following sections for details:
About the Windows Server Sensor
The Windows Server Sensor (agent) runs as a Windows service in a compatible Windows Server system. The Server Sensor observes events within the Windows Server system and sends Interflow data records to the data processor.
The captured events are:
- Hardware
- Security
- System
- Windows Firewall
- Windows Defender
- PowerShell
The Windows Server Sensor provides the following key capabilities:
-
If the sensor has coverage over the domain controller, Stellar Cyber enriches data with the relationship between users and IP addresses.
-
If the sensor has coverage over the DHCP server, Stellar Cyber sees the relationship between hostnames and IP addresses, and so can track assets when the IP address changes.
-
Windows Server Sensor provides the data foundation for Stellar Cyber's machine learning alerts that use the Windows Events index.
Although you can also provide coverage of Windows logs using other visibility tools such as the ManageEngine Log Collector or Winlogbeat, the logs provided by these tools are not normalized, enriched, and stored in the Windows Events index used for machine learning alert generation (except for ManageEngine ADAudit Plus logs) and cannot be used for machine learning alert generation.
In addition, the Windows Server Sensor provides the following advantages over alternative solutions:
-
Windows Server Sensor provides easier deployment and maintenance.
-
Windows Server Sensor provides granular filtering at the edge through the Stellar Cyber user interface.
-
By using the Windows Server Sensor, you do not need to deploy another modular sensor to forward logs from ManageEngine or Winlogbeat.
-
Windows Server Sensor Processes
The Windows Server Sensor launches the following processes:
|
Name in Task Manager |
Name in Services App |
Description |
|---|---|---|
|
aella_conf_win_srv.exe |
Windows Agent Sensor Conf |
Handles Windows Server Sensor configuration |
|
aella_ctrl_win_srv.exe |
Windows Agent Sensor Ctrl |
Monitors other services, and can stop or start them based on the configuration |
|
aella_winlog.exe |
Windows Agent Sensor Logbeat |
Sends Windows events to DP |
|
aella_filebeat.exe |
Windows Agent Sensor Filebeat |
Sends log files from Windows DHCP server (if installed and running) to DP |
|
aella_fim.exe |
Windows Agent Sensor FIM |
Provides file integrity monitoring services, as configured in the Sensor Profile |
|
aella_diagnostics_win_srv.exe |
Windows Agent Sensor Phonehome |
Sends Windows Server Sensor logs to DP |
Windows Server Sensor Indices
Data collected by the Windows Server Sensor can feed the following Stellar Cyber indices:
-
Traffic (
aella-adr-*) -
Windows Event Log (
aella-wineventlog-*) -
Sensor Monitoring (
aella-ade-*)
Supported Systems 
The Windows Server Sensor is supported on Windows Server 2008 R2, 2012, 2016, 2019, and 2022 21H2 (Server Desktop Experience). The same .msi installation file supports all of these environments. The Server Sensor is only available in 64-bit.
When the system sleeps, the connection drops, and no data is collected. The connection is re-established when the system wakes. To avoid this, configure Windows to Never sleep.
The host Windows Server into which the Windows Server Sensor is installed must meet the following minimum requirements, regardless of whether it is a physical or virtual server:
| Component | Specification |
|---|---|
| Host CPU | Xeon Core 2 virtual cores (2.0 GHz or more) |
| Host RAM (GB) | 8 |
| Host SSD (GB) | 128 |
| OS | Windows Server 2008 R2, 2012, 2016, 2019, or 2022 21H2 (Server Desktop Experience) |
Update Windows Server Software Before Installing Windows Server Sensor
It's a good idea to use Windows Update to make sure your Windows Server software is up to date before installing the Windows Server Sensor. For example:
-
The Windows Server Sensor software includes the AI_ChainedPackageFile.vc_redist.x64.exe redistributable from Microsoft. Successful installation of this redistributable requires the following prerequisites from Microsoft, installed either in the order below or as part of a standalone package (KB2919355 is a prerequisite of KB2999226).
Clean Up Existing 4.3.x Installations in Windows Server 2008 R2 or 2012 R2 Before Installing 5.0.x
Stellar Cyber recommends that you fully uninstall any 4.3.x Windows Server Sensors from Windows Server 2008 R2 or 2012 R2 environments before installing the 5.0.x software. Note the following:
-
Use the uninstall procedure provided in Uninstalling the Server Sensor.
-
Make sure you check the following boxes during the uninstall:
-
Remove Data Files
-
Remove Scheduler Task
-
Remove Stellar Syswatcher
-
-
When the uninstallation completes, manually delete the C:\ProgramData\StellarCyber folder.
PowerShell Not Required
PowerShell is not required for Windows Server Sensor installations.
Exclude Server Sensor from AV/EDR Scanning
Stellar Cyber recommends that you prevent potential conflicts by configuring any anti-virus or EDR software installed on the same host as the Server Sensor to exclude the Server Sensor installation directories from scanning. The directories to exclude for a Windows Server Sensor are as follows:
|
Server Sensor Type |
Folders/Files to Exclude from AV/EDR Scanning |
|---|---|
| Windows |
C:\ProgramData\Stellarcyber C:\Program Files\Aella C:\Windows\Stellar_syswatcher.exe (sensors running pre-4.2.2 versions) |
Possible False Positives from FireEye PROCGUARD
During installation of the Windows Server Sensor, it is possible that FireEye PROCGUARD may report the following alert – Attempted LSASS access by aella_conf_win_srv.exe detected. After investigation, Stellar Cyber has determined that this is a false positive and that the aella_conf_win_srv.exe service does not interact with C:\\Windows\\system32\\lsass.exe on the host machine.
Open Firewall Ports
The sensor requires open firewall ports in order to communicate.
Obtaining the Windows Server Sensor Installer
You download the installation file for the Windows Server Sensor from the System | Deployment | Sensor Installation page. Use the following procedure:
Only users with the Deployment | Sensor Installation | Sensor Image Download privilege assigned to their profile in the System | Role-Based Access Privileges interface can download images.
-
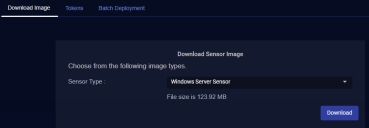
Navigate to System | Deployment | Sensor Installation | Download Image.
-
Set the Sensor Type dropdown to Windows Server Sensor.
The display updates to show you the size of the files to be downloaded.
-
Download.
The system downloads the .msi installation file to the system's Downloads folder.
The next step is to use the Tokens tab to obtain the token you will use to install the downloaded sensor, as described below.
Obtaining a Token for the Installation
Tokens are required to authorize and configure the installation of a sensor image downloaded from the DP in the System | Deployment | Sensor Installation page. Tokens point the installed sensor to the correct DP, assign the specified tenant, and authorize the sensor installation.
Use the following procedure to obtain a token in the Tokens tab:
-
Navigate to System | Deployment | Sensor Installation | Tokens.
-
If a token already exists for the target tenant for the sensor installation, Copy it to the clipboard or Download it as a file.
-
Copy the token if you plan on pasting it into an msiexec command or the installation wizard's dialog box.
-
Download the token as a file if you plan on referring to it in the msiexec command, hosting it at a URL, or pointing to it in the installation wizard's dialog box.
Refer to Assigning Tokens for a summary of the different ways in which tokens can be applied to a sensor installation.
-
-
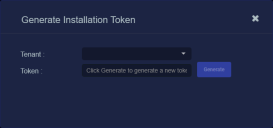
If there is not already an unexpired token for the target tenant, click the Generate button.
The Generate Installation Token dialog appears:
-
Select the tenant for the token from the Tenant dropdown. This is the tenant to which all sensors authorized with this token will be automatically assigned. The dropdown lists all tenants configured for your organization in the System | Tenants page.
-
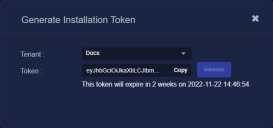
Click the Generate button.
The system generates the token and displays its contents in the Token field. The dialog also updates to display the expiration date for the token, as illustrated below.
-
You can use the Copy button to copy the token to the clipboard immediately, or simply close the dialog and retrieve the token from the Tokens tab later on.
Installing the Windows Server Sensor
You can install the Windows Server Sensor using any of the following techniques. Each technique requires the use of the token you obtained in the previous section to authorize and configure the installation.
|
Single Installation Using Wizard |
This is the simplest scenario, where you are installing a single Windows Server Sensor interactively on a target machine using the GUI-based installation wizard. Refer to Installing the Windows Server Sensor Using the Wizard. |
|
Single Installation from Command Line |
You can also install a single Windows Server Sensor using an msiexec command and the .msi installer downloaded from the Download Images tab in the System | Deployment | Sensor Installation page. The proper syntax for the msiexec command, including a selected token, is provided in the MSI File Installation section of the Batch Deployment tab in the Sensor Installation page. Refer to MSI File Installation. |
|
Bulk Installation Using a Script |
You can create your own scripts for bulk installations using the msiexec command provided in the MSI File Installation section of the Batch Deployment tab in the Sensor Installation page. As described in About Tokens, the same token can be reused to authorize multiple sensor installations for the same tenant. Refer to MSI File Installation. |
|
Bulk Installation Using GPO |
You can also use Microsoft Group Policy Object (GPO) to deploy the Window Server Sensor to multiple systems at once. You do this by using the GPO Bulk Installations tool in the Batch Deployment tab in the Sensor Installation page. This tool helps you download a zip file containing a batch file preconfigured with a selected token. You can use the contents of the zip file to generate an MST file that can be used with GPO to deploy the Window Server Sensor to multiple systems at once. Refer to GPO Bulk Installations |
Installing the Windows Server Sensor Using the Wizard
Use the following procedure to install the Windows Server Sensor interactively using the wizard:
During the installation, a Windows command prompt window may appear. Do not close this window manually – the installation wizard closes it automatically when the installation is complete.
To avoid installation issues, complete any pending updates for the host Windows machine before upgrading the Server Sensor.
-
Open the folder where you downloaded the .msi installation file from the Download Image tab in System | Deployment | Sensor Installation.
-
Right-click the .msi file and select Properties from the context menu that appears.
-
Select Unblock in the Security section.
Some Windows systems automatically block downloaded files.
-
Select OK.
-
Double-click the .msi file to open it and start the installation. Accept any system warnings presented by User Account Control
-
Click Next on the Welcome screen.
- Choose the path for the installation when prompted by the wizard and click Next.
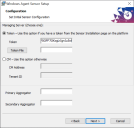
-
Select the Token option and supply the token to be used for the installation. You can use either of the following techniques:
-
Paste the token you copied from the Token tab in the System | Deployment | Sensor Installation page into the Token field.
-
Select Token File and navigate to the location of the token file you downloaded from the Token tab in the System | Deployment | Sensor Installation page.
The figure below shows a token pasted into the Token field:
Do not use the CM options. These options are only used with Stellar Cyber platforms that do not have an "s" in their version number. If your Stellar Cyber platform includes the Sensor Installation page and the Tokens tab, use the Token option with the token file you already obtained.
-
-
(Optional) Configure a Primary and Secondary aggregator:
- Primary Aggregator – If you are configuring this Server Sensor to forward data to an aggregator before it is sent to the DP, you can enter the primary aggregator's IP address here.
-
Secondary Aggregator – If you are configuring this Server Sensor to forward data to an aggregator, you can enter the secondary aggregator's IP address here.
The wizard does not prevent you from specifying a Secondary Aggregator if the Primary Aggregator is left empty. However, a Secondary Aggregator specified without a Primary Aggregator is ignored and not applied to the installation.
-
Select Install to begin the installation.
The installer installs the Server Sensor, displaying a confirmation dialog box when complete.
-
Select Finish.
The Server Sensor is installed as a service.
You can verify the installation using any of the following techniques:
-
Check the System | Sensors tab in the user interface to see that the sensor has registered itself successfully.
-
Open the Services app and look for the Windows Agent Sensor Ctrl entry.
-
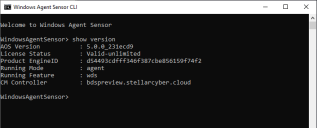
Access the Server Sensor's CLI and run the
show versioncommand. Verify that theCM Controllerfield lists the DP from which you downloaded the token for the sensor.
Assigning a Token to the Server Sensor from the CLI
As described in Assigning Tokens, you can apply a token to an installed sensor from the sensor CLI with the set token command. This can be useful if you need to change a token from the CLI after the Server Sensor has already been installed. Refer to the table below for a summary of the available techniques:
You only need to use one of the options in the table below. These are just different ways to do the same thing – apply the token.
|
Option 1. Copy and Paste the Token String |
Copy the token string from the Tokens tab and paste it into the CLI command. The syntax is as follows:
|
|
Option 2. Upload the Token as a File to the Sensor |
Download the token as a file from the Tokens tab, upload it to the sensor, and reference it in the
For example, the following command points to the
This technique only works for Server Sensors. There isn't a way to upload the token.text file to a newly installed modular sensor virtual machine. |
|
Option 3. Host the Token on an HTTP Server |
Download the token as a file from the Tokens tab, upload it to an HTTP server, and reference it in the
You can also use an HTTPS server. In that case, the specified URL must also include the username and password for the server. |
Configuring the Server Sensor in the CLI
Applying a token to the Server Sensor automatically configures it with the correct IP address of its managing DP and its tenant assignment. It also authorizes the Server Sensor. These are all settings that required manual configuration in previous versions and are no longer required.
However, it is still useful to access the sensor's CLI to verify its operation and change any necessary settings. To run the Server Sensor's CLI, find the Windows Agent Sensor Command Line Interface entry in the Windows Start Menu. If it does not appear at first, use the Find function.
After starting the Windows Server Sensor CLI, a terminal window appears as below. This window lets you enter CLI commands to the Server Sensor. Enter the show version command to verify the sensor's operations. In response, the sensor displays output similar to the following:
Using a Proxy with the Windows Server Sensor
If your Windows Server Sensor does not have direct access to the Internet, you can configure it to use an HTTP proxy for connection to the DP.
Your HTTP proxy must allow SSL on TCP ports 443 and 8889. The set proxy <proxy> test command described in the procedure below verifies that the necessary ports are open.
You configure the Windows Server Sensor to use an HTTP proxy in the CLI. The procedure is as follows:
The CLI prevents you from entering non-printable characters as part of the username or password for the proxy, as well as the proxy itself.
-
First, we'll use the set proxy <proxy> test command to verify that our proxy is reachable and that SSL is accepted on both TCP 443 and 8889.
Enter the <proxy> in the following format:
http://[username:password@]<proxy_ip>[:<proxy_port>]Stellar Cyber recommends that you always test a proxy successfully before setting it.
The following example shows an unsuccessful test for a proxy server on 10.1.2.3:8081, followed by a successful test for the same IP address on port 8080:
CopyWindowsAgentSensor> set proxy http://user:pass@10.1.2.3:8081 test
Test HTTP/HTTPS proxy: http://user:pass@10.1.2.3:8081
Failed testing dev-demo.stellarcyber.cloud:443, err: timed out
WindowsAgentSensor> set proxy http://10.1.2.3:8080 test
Test HTTP/HTTPS proxy: http://10.1.2.3:8080
Passed testing dev-demo.stellarcyber.cloud:443
Passed testing receiver-dev-demo.stellarcyber.cloud:8889 -
Once you've verified that your proxy is working correctly, you can set it with the same command but leaving out the test parameter. For example:
CopyWindowsAgentSensor> set proxy http://10.1.2.3:8080
Succeed setting proxy
Other Proxy Commands
The following additional commands are useful when working with proxies:
-
Removing a Proxy –
unset proxy -
Showing Configured Proxies –
show proxy -
Review set proxy Syntax –
set proxy ?
Troubleshooting a Proxy
This section lists some error messages you may see when configuring a proxy along with troubleshooting tips for each.
Your first line of defense when troubleshooting a proxy is the show proxy command. You can use this to verify the current proxy configuration and ensure that things are set up the way you intended them to be.
-
Failed testing xxx.stellarcyber.cloud:443, err: timed outThis error message can appear when the sensor can not reach the proxy server. Check your proxy configuration with show proxy.
-
Failed testing xxx.stellarcyber.cloud:443, err: [Errno 10061] No connection could be made because the target machine actively refused itThis error message indicates that the sensor could reach the proxy server but the proxy server did not accept the connection. Check whether the proxy service is up and running on the specified port and if there are any firewalls along the way that might be rejecting the connection.
-
Failed testing receiver-xxx.stellarcyber.cloud:8889, code 403This error message is most likely triggered because of the proxy server's configuration. For example:
-
The proxy server may not allow port 8889 for SSL connections.
-
The proxy server may not allow clients to connect to the
receiver-xxx.stellarcyber.cloudhost.
-
-
Failed testing receiver-xxx.stellarcyber.cloud:8889, code 503This error message usually indicates that the proxy server could not get a response from
receiver-xxx.stellarcyber.cloud:8889(that is, the destination DP).
Sending DHCP Server Logs to a Device Sensor
If the sensor has coverage over the DHCP server, you can send the DHCP server logs to a modular sensor with the log forwarder feature enabled so that they can be used to enrich assets with DHCP data. Configure this feature in the CLI as follows:
-
Use the following command to forward DHCP logs to a specified modular sensor:
set dhcp_log enable ip <sensor ip address>For the
<sensor ip address>, supply the IP address of a modular sensor with the log forwarder feature enabled in its sensor profile.To use this feature, you must open port 5044 for DHCP beats in any firewalls between the Server Sensor and the receiving modular sensor.
- Verify the data entry with the
show versioncommand. - Enter the
quitcommand to close the CLI.
Uninstalling the Server Sensor
Stellar Cyber recommends that you remove the Windows Server Sensor using the Change button in the Programs and Features control panel instead of the Uninstall button.
Using the Change button gives you access to the following additional uninstall options that ensure the program and all its data are removed completely:
-
Remove Data Files
-
Remove Scheduler Task
-
Remove Stellar Syswatcher
If you are planning on reinstalling the Server Sensor, Stellar Cyber recommends that you leave these items unchecked.
If you want to uninstall completely, you should check these boxes.
During the uninstallation, a Windows command prompt window may appear. Do not close this window manually – it closes automatically when the uninstallation is complete.
About Sysmon in this Release
The Windows Server Sensor installation does not download and install the stellar_syswatcher (Microsoft Sysmon64) service due to potential system crashes in certain operating systems (Windows 2008R2 and 2012, although possibly others).
You can install the latest version of Sysmon (v13.31 at this writing) manually if you want the Windows Server Sensor to report Sysmon events to the DP. However, Stellar Cyber strongly recommends that you test your installation in a non-production environment to verify operations before moving to production.
Use the following procedure to download Sysmon from Microsoft, install it manually, and verify operations:
-
Install the Windows Server Sensor using the instructions earlier in this topic.
-
Download the latest version (v13.31) of Sysmon from Microsoft and extract it to the system where you want to install it.
-
Install Sysmon64 with the stellar_syswatcher.xml configuration file.
-
Restart the winlogbeat service.
If you install sysmon after the Windows Server Sensor, you must restart the winlogbeat service so that it works with Sysmon. If you install Sysmon before the Windows Server Sensor, Sysmon works with winlogbeat without a restart.
-
Verify that Sysmon events are received properly in the DP's aella-adr index.
Install Sysmon64 with stellar_syswatcher
After downloading and unzipping the installer for Sysmon64 to the target system, you can install it as follows:
-
Open a command prompt as an administrator (right-click the cmd.exe file in Windows Explorer and choose Run as administrator).
-
Change directories to the directory where you unzipped the Sysmon64.exe installer.
-
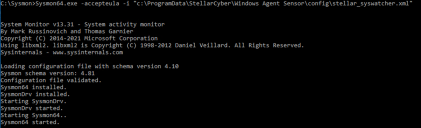
Install Sysmon64.exe with the stellar_syswatcher.xml configuration file using the following command:
Sysmon64.exe -accepteula -i "c:\ProgramData\StellarCyber\Windows Agent Sensor\config\stellar_syswatcher.xml"
In response, the system installs and starts the Sysmon64 utility:
Restart the winlogbeat Service if the Windows Server Sensor is Already Installed
-
If you install Sysmon after the Windows Server Sensor, you must restart the winlogbeat service so that it works with Sysmon.
-
If you install Sysmon before the Windows Server Sensor, Sysmon works with winlogbeat without a restart.
Verify Sysmon64 Installation
You can verify that Sysmon64 was installed correctly by performing the following tasks:
-
Open the Task Manager (Ctrl-Alt-Del -> Task Manager) and verify that the Sysmon64 service appears in the list.
-
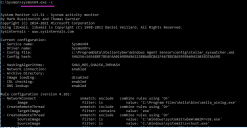
Return to the command prompt and run sysmon64.exe -c to view its current configuration. Verify that the configuration you see matches the configuration shown below:
-
Open the Windows Event Viewer and navigate to the following path in the left navigation pane:
Applications and Services Logs | Microsoft | Windows | Sysmon | Operational
-
Verify that Network connection detected (Event ID 3) events appear in the list as highlighted in the figure below:
Verify Sysmon Events are Received on DP
You can verify that the manually installed Sysmon64 service is successfully sending events to the DP with the following procedure:
-
Connect to the DP managing the Windows Server Sensor and navigate to System | Collection | Sensors.
-
Take note of the name of the sensor where you installed the Sysmon64 service. For example:
-
Navigate to the Investigate | Threat Hunting page.
-
Set the Indices dropdown to Windows Events.
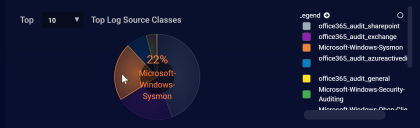
-
Locate the Top Log Source Classes panel and verify that it includes Microsoft-Windows-Sysmon, as in the figure below:
-
Click the button next to the entry for Microsoft-Windows-Sysmon in the Legend to use it as a filter. For example:
-
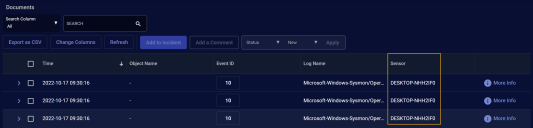
Scroll down to the Documents table.
-
Use the Change Columns button to add the Sensor column to the display if it is not already there.
-
Sort by the Sensor column and scroll to the entries for the sensor you identified at the start of this procedure to verify that it passes the Sysmon filter. For example: