Configuring Data Enrichment 
You must have Root scope to use this feature.
Stellar Cyber uses information from a variety of sources to enrich the data collected. This page allows you to customize certain enrichment types.
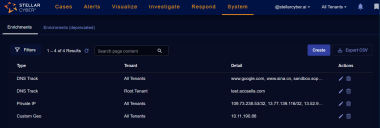
As shown in the above example, there are three types you can configure:
About Enrichments in Previous Releases
The 4.3.7 release updates Stellar Cyber's approach to enrichments, simplifying the process while also providing more per-tenant flexibility for private IP ranges. The pre-4.3.7 approach is still available in the Enrichments (deprecated) tab and is described in Enrichments in Previous Releases .
Using the Enrichments Table
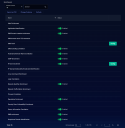
When you select the System | Data Processor | Enrichments option, Stellar Cyber displays a table of the available enrichment options that have been configured for your organization. From this table, you can Create, Edit or Delete the enrichments, and perform other, standard table functions.
Configuring Private IP Enrichments
The IP enrichment option lets you specify subnets for which IP addresses should be considered private and marked accordingly in event record fields. All other addresses (except RFC-1918 addresses) are considered public.
IP addresses described by RFC-1918 as generally-accepted "private" IP addresses do not need to be configured. They are automatically designated as private.
-
Click System | Data Processor | Enrichment. The enrichment table is displayed.
-
Click the Create button.
-
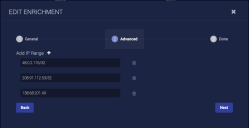
In the dialog that displays, set Type to Private IP.
-
Specify the Tenant that will be allowed to use this enrichment. You can select All Tenants or a specific individual tenant.
-
Click Next.
-
In the first row that displays, enter a standard IPv4 address / subnet. Each row represents at most one subnet. If you need another subnet for this enrichment definition, click the button to add another row. Use the button to remove rows.
-
Click Next.
-
Review the settings.
-
Click Submit.
Configuring DNS Track Enrichments
You can use the DNS Track option to track DNS resolution changes for specified domains. If one of the tracked domains resolves to a new IP address, Stellar Cyber creates an entry in the Changed Domains to IP Resolutions table in the Investigate | Threat Hunting | Threat Hunting Library | DNS Analysis page.
-
Click System | Data Processor | Enrichment. The enrichment table is displayed.
-
Click the Create button.
-
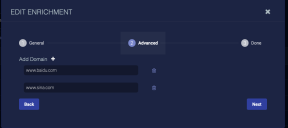
In the dialog that displays, set Type to DNS Track.
-
Specify the Tenant that will be allowed to use this enrichment. You can select All Tenants or a specific individual tenant.
-
Click Next.
-
In the dialog that displays, specify a domain. If you want to add another subnet for this enrichment definition, click the button to add another row. Use the button to remove rows.
-
Click Next.
-
Review the settings.
-
Click Submit.
Configuring Custom (IP) Geo Enrichments
You can use the IP Geo Enrichment module to configure the geolocation associated with specified IP addresses manually, overriding the geolocation obtained by Stellar Cyber from geolocation databases. This is useful in situations where you are seeing false positives for Impossible Travel and Location Anomaly alerts based on an inaccurate geolocation. This allows you to adjust information if you think that false positives have occurred.
-
Click System | Data Processor | Enrichment. The enrichment table is displayed.
-
Click the Create button.
-
In the dialog that displays, set Type to Custom Geo.
-
Specify the Tenant that will be allowed to use this enrichment. You can select All Tenants or a specific individual tenant.
-
Click Next.
-
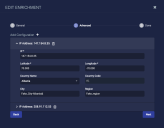
In the dialog that displays, set the following options (Options with an asterisk are required; others will appear in geolocation display information for the specified IP address.):
-
IP* – The IP address for which you would like to specify a geolocation.
-
Latitude* – The latitude for the geolocation of this IP address in decimal degrees format, from -90 to 90.
-
Longitude* – The longitude for the geolocation of this IP address in decimal degrees format, from -180 to 180.
-
Country Name – Select the country for this IP address from the dropdown menu.
-
Country Code – Set automatically based on the selected Country Name.
-
City – Specify the City for this IP address.
-
Region – Specify the Region for this IP address
-
-
Click Next.
-
Review the settings.
-
Click Submit.
Enrichments in Previous Releases 
This section describes how Enrichments worked in releases prior to 4.3.7. This approach is still available in the Enrichments (deprecated) tab in 4.3.7.
You must have Root scope to use this feature.
Stellar Cyber uses information from a variety of sources to enrich the data collected. This enrichment helps refine detections.
Enrichment Table
When you select the System | Data Processor | Enrichment option, Stellar Cyber displays a table of the available enrichment modules along with their current status, as shown below:
-
Modules that can be individually enabled or disabled are listed with a toggle in the Status column that lets you switch them between Enabled and Disabled, as shown in the figure above.
-
Modules that are required for Stellar Cyber operations are listed without a toggle switch in the Status column and cannot be disabled.
-
Modules that require configuration are listed with a Config button adjacent to their entry (for example, DNS Track and IP Geo Enrichment).
Configuring DNS Track
You can use the DNS Track module to track DNS resolution changes for specified domains. If one of the tracked domains resolves to a new IP address, Stellar Cyber creates an entry in the Changed Domains to IP Resolutions table in the Investigate | Threat Hunting | Threat Hunting Library | DNS Analysis page.
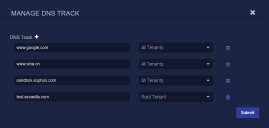
The DNS Track enrichment module is listed with a Config button in the Enrichment table that lets you add tracked domains, as shown in the example below:
To track a domain:
- Click System | Data Processor | Enrichment. The Enrichment table appears.
- Click Config in the DNS Track row.
- Click the button to add a row to the table.
- Enter the domain you want to track.
- Choose a tenant.
- Click Submit.
To remove a domain:
- Click System | Data Processor | Enrichment. The Enrichment table appears.
- Click Config on the DNS Track row.
- Click in the domain's row.
- Click Submit.
Configuring IP Geo Enrichment
You can use the IP Geo Enrichment module to configure the geolocation associated with specified IP addresses manually, overriding the geolocation obtained by Stellar Cyber from geolocation databases. This is useful in situations where you are seeing false positives for Impossible Travel and Location Anomaly alerts based on an inaccurate geolocation. Specifying the correct location for an IP address manually allows you to prevent such false positives.
Use the following procedure to assign a geolocation to an IP address manually:
- Click System | Data Processor | Enrichment. The Enrichment table appears.
- Click Config in the IP Geo Enrichment row.
- Click the + Add Configuration button.
-
Set the following options. Options with an asterisk are required; others will appear in geolocation display information for the specified IP address.
-
IP* – The IP address for which you would like to specify a geolocation.
-
Tenant* – The tenant for which this IP geolocation assignment will apply. You can select All Tenants or a specific individual tenant.
-
Latitude* – The latitude for the geolocation of this IP address in decimal degrees format, from -90 to 90.
-
Longitude* – The longitude for the geolocation of this IP address in decimal degrees format, from -180 to 180.
-
Country Name – Select the country for this IP address from the dropdown menu.
-
Country Code – Set automatically based on the selected Country Name.
-
City – Specify the City for this IP address.
-
Region – Specify the Region for this IP address
-
- Click Submit.
To remove a custom IP geolocation:
- Click System | Data Processor | Enrichment. The Enrichment table appears.
- Click Config on the IP Geo Enrichment row.
- Click in the IP address's row.
- Click Submit.
Enrichment Details
The following table lists the metadata fields that Stellar Cyber uses for enrichment, a description of the field, the source of the information, and the enrichment it's used for.
| Enrichment Field | Description | Source | Enrichment |
|---|---|---|---|
| access_mask | Permission required to access the object | - | Windows object access |
| access_subject | Process or system object that initiated access | - | Windows object access |
| aella_tuples | Unique session ID comprising source IP, destination IP and port, and app ID | - | - |
| appid_family | Application family | DP | App ID |
| appid_name | Application name | DP | App ID |
| appid_stdport | Whether or not the application is using the standard port | DP | App ID |
| attack_start_date | Timestamp of the start of the attack | - | - |
| command | Command that was run | - | Linux command |
| correlation_info | The metadata in individual events of a correlation result | - | - |
| detect_date | When the sensor detected an attack | - | - |
| detect_origin | Direction of the attack | - | - |
| detection_flag | Detection this record applies to | - | - |
| direction | Direction of the file transfer, either forward for source to destination, or backward for destination to source |
Traffic data | File transfer direction |
| domain_reputation | Reputation of the domain | - | - |
| dscp_name | Readable DSCP value | Sensor | Network identifier |
| dstmac | Destination MAC address | - | - |
| dstip_aella_flag | How to process the IP address for detections | - | - |
| dstip_tag srcip_tag hostip_tag |
Asset tag associated with the IP address | - | - |
| dstip_assetid srcip_assetid hostip_assetid |
Asset ID associated with the IP address | - | - |
| dstip_host srcip_host hostip_host |
Host name associated with the IP address | DNS/DHCP | Host/domain name correlation |
| dstip_geo srcip_geo remote_ip_geo hostip_geo |
Geographic location (country, city, etc) associated with the IP address | - | IP geo |
| dstip_geo_point srcip_geo_point remote_ip_geo_point hostip_geo_point |
Latitude and longitude associated with the IP address | - | - |
| dstip_reputation srcip_reputation remote_ip_reputation hostip_reputation |
Reputation associated with the IP address | - | Reputation |
| dstip_reputation_source srcip_reputation_source remote_ip_reputation_source hostip_reputation_source |
Source of the reputation associated with the IP address | - | Reputation |
| dstip_sig_id srcip_sig_id hostip_sig_id |
Signature ID associated with the IP address | - | - |
| dstip_type srcip_type remote_ip_type hostip_type |
Whether the IP address is public or private | - | IP type |
| dstip_username srcip_username remote_ip_username hostip_username dstip_usersid srcip_usersid remote_ip_usersid hostip_usersid |
Username and user ID associated with the IP address | AD | Username correlation |
| dstip_domain_creation srcip_domain_creation hostip_domain_creation remote_ip_domain_creation |
When the domain associated with the IP address was created | - | - |
| engid_device_class | Sensor operating system, either Windows or Linux | Sensor | Sensor information correlation |
| engid_gateway | Sensor's gateway | Sensor | Sensor information correlation |
| exec_user | User that executed the command | - | Linux command |
| hostip | IP address of the host reporting the event | - | - |
| icmp_type | ICMP message type | DP | ICMP |
| inbytes_total | Total inbound bytes in the session so far | Sensor | Network traffic metric |
| is_dga | If a DNS request is DGA | DP | Suspicious domain identification |
| login_result | Result of the login attempt | Sensor | Login |
| login_type | Application logged in to | Sensor | Login |
| login_user | Username associated with the login attempt | Sensor | Login |
| mac | MAC addresses associated with the host | - | - |
| metadata.is_tunneling | If a DNS session is potentially tunneling | DP | DNS tunneling correlation |
| metadata.request.domain_creation | Creation of a domain in the DNS request | DP | DNS domain creation |
| metadata.request.effective_tld | Effective TLD of a domain name | DP | DNS domain name TLD extraction |
| metadata.response.domain_creation | Creation of a domain in the DNS request | DP | DNS domain creation |
| metadata.response.effective_tld | Effective TLD of a domain name | DP | DNS domain name TLD extraction |
| metadata._whitelist | Whether any metadata field is whitelisted | - | - |
| netid_name | Name of a network ID | Sensor | Network identifier |
| new_dns_record | A DNS record that has not been seen before | DP | DNS records tracking |
| outbytes_total | Total outbound bytes in the session so far | Sensor | Network traffic metric |
| parent_child | Concatenation of the parent and child process names | DP | Process correlation |
| parent_proc_name | Name of the parent process | DP | Process correlation |
| process_name | Name of the process | DP | Process correlation |
| proto_name | Name of the protocol | - | - |
| remote_ip | IP address of the remote host involved in the event | Sensor | Windows PowerShell script |
| remote_port | Port of the remote host involved in the event | Sensor | Windows PowerShell script |
| smb_denied_count | Number of times access was denied in a single SMB session | DP | SMB |
| smb_username_count | Number of unique usernames used in a single SMB session | DP | SMB |
| smb_username_set | Set of unique usernames used in a single SMB session | DP | SMB |
| srcmac | MAC address of the source IP address | - | - |
| tenantid | ID of the tenant | Sensor and DP | Tenant information correlation |
| tenant_name | Name of the tenant | Sensor and DP | Tenant information correlation |
| totalbytes | Total bytes in the session so far | Sensor | Network traffic metric |
| totalpackets | Total packets since the last session update | Sensor | Network traffic metric |
| url_reputation | Reputation of the URL | - | - |
| vulnerabilities.cve | The CVE associated with a plugin or vulnerability | Database | Security scan vulnerability |
| vulnerabilities.description | Description of a Nessus vulnerability |
Database |
Security scan vulnerability |