Installing a Modular, Network, or Security Sensor in AWS
A network sensor monitors the virtual environment, the physical environment if connected to the span port of a physical switch, or the LAN segment via a mirror port on a switch. The sensor monitors network and server response times and can identify applications.
The network sensor converts that information to metadata and forwards it to the DP as Interflow. The DP can then provide security, DDoS, and breach attempt detections.
A security sensor operates as a network sensor and adds:
- sandbox
- anti-virus
- IDS
You can also tunnel traffic over VXLAN from an agent sensor, network sensor, or container sensor to the security sensor so it can inspect those environments.
A modular sensor lets you easily add the features you like to your sensor. This helps simplify your deployment and lets you manage the VM requirements for the sensors based on the modular features they use.
You can install a modular, network, or security sensor on AWS. To install you must:
Preparing
Click to see the minimum system requirements for installing a modular, network, or security sensor.
You must have:
- One IP address with access to a default gateway
- A Stellar Cyber license that can be applied to the sensor
To prepare for the installation:
- Open firewall ports as for a network or security sensor.
- Open firewall ports for log ingestion.
- Contact Stellar Cyber support (support@stellarcyber.ai) for access to the AMI. You must provide:
- AWS account name
- AWS account number
- AWS region for the sensor
Launching the AMI
To configure and launch the AMI:
Use our example as a guideline, as you might be using a different software version.
-
Log in to your EC2 Dashboard.
-
Click on AMIs, under Images.
A list of existing AMIs appears.
-
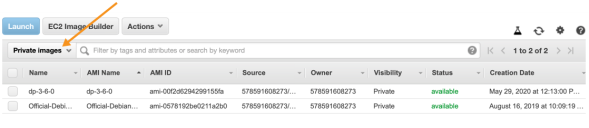
If you don't see any products, click the drop-down next to the search bar and choose Private images.
If you still don't see any products, make sure your region setting is correct.
And if you still don't see any products, contact technical support.
AMI Names for Stellar Cyber Images
For reference, the AMI names for the Stellar Cyber AMIs are as follows:
-
Modular Sensor – ModularSensor-4-x-y
-
Network Sensor – NetworkSensor-4-x-y
-
Security Sensor – SecuritySensor-4-x-y
In all cases, the x-y refers to the minor version numbers of the sensor software (for example, ModularSensor-4-3-5).
-
-
Click the check-box to the left of the AMI. The Launch button activates and the details appear.
-
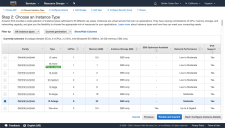
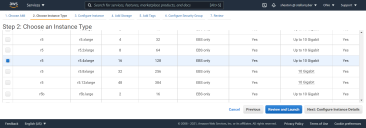
Click Launch. The Choose an Instance Type page appears.
- Choose a t2.2xlarge or higher type. Smaller instance types are not supported.
-
Click Next: Configure Instance Details. The Configure Instance Details page appears.
We recommend keeping the default settings.
-
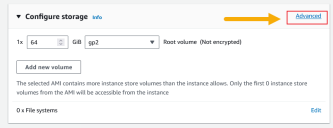
Click Next: Add Storage. The Add Storage page appears.
We recommend keeping the default settings.
As an option, you can encrypt your storage volume as follows:
-
Click the Advanced button in the Configure Storage panel.
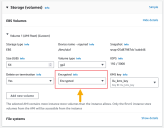
-
Set the Encrypted dropdown in the EBS Volumes settings to Encrypted.
You can also convert an existing sensor's unencrypted storage volume to use encryption.
-
-
Click Next: Add Tags. The Add Tags page appears.
Stellar Cyber does not use tags.
-
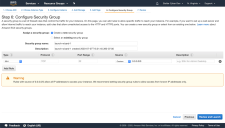
Click Next: Configure Security Group. The Configure Security Group page appears.
You can ignore the warning at the bottom of the page.
Security groups define which local ports and remote hosts can reach the sensor. AWS enables SSH by default.
- Enter the Security group name.
-
Click Add Rule. A new row appears. Configure inbound rules to allow your sensor to communicate with the DP.
If you already added rules on a prior installation, you can choose Select an existing security group to see a list of the existing groups.
-
Click Review and Launch. Make changes if necessary.
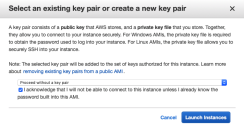
- Click Launch. The Select an existing key pair screen appears. Stellar Cyber is configured with a user name and password, so does not need a key pair.
- Choose Proceed without a key pair.
-
Click the check-box to acknowledge.
-
Click Launch Instance.
You can launch the image but you cannot copy it. This means that the VM must be deployed in the AWS region where the image was authorized.
The VM is now running in the AWS cloud.
Connecting the Sensor to the DP
To connect to the DP:
- Log in to your new sensor. The default username/password is aella/changeme. You are immediately prompted to change the password.
-
Change the password.
After you change the password, your session closes automatically. When you log back in with your new credentials, the prompt changes to DataSensor>.
-
Set the host name. The host name is displayed in Stellar Cyber and should be unique for each sensor:
set hostname <new hostname> -
If necessary, set the proxy HTTP server:
set proxy http://<proxy IP address:port> -
Optionally assign the tenant (if you skip this, the sensor is assigned to Root Tenant):
set tenant_id <Tenant ID from Stellar Cyber> -
Use the
set cmcommand to specify the IP address to reach the management interface of the Data Processor. For a DP cluster, this is the IP address of the DL-master's management interface. For a single DP deployment, this is simply the DP's management IP address. You can specify either an IP address or a hostname. For example:set cm 192.168.44.10or:
set cm example.company.comIf you specify a hostname rather than an IP address, the system attempts to verify the hostname with the DNS server. If the DNS server is not reachable, the system reports the error and lets you either proceed with the configured hostname or quit. This way, you can specify a hostname for the
set cmdestination in an offline environment without access to a DNS server. - Verify with the
show cmcommand. You should see the IP address of the DP listed as the CM Controller and the Status should be Established. -
Use the
show timecommand to view the time zone.During installation, the timezone for sensors are automatically set to UTC+0. Since the logs for some security products may only include the local time without a timezone, Stellar Cyber recommends that you set the sensor timezone to the same timezone as your security product.
-
Log out with the
quitcommand.
The sensor automatically contacts the DP to register itself.
Authorize the Sensor
You must authorize the sensor when it appears in the network.
You can authorize multiple sensors at a time. So if you're installing multiple sensors, install them all, then authorize them all at once.