Creating New Alert Types
In addition to the alert types provided by Stellar Cyber, you can create your own custom alert types. Once you've created a custom alert type, you can add it to an automated threat hunting playbook.
-
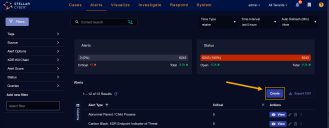
Display the Stellar CyberAlerts page.
-
Click the Create button.
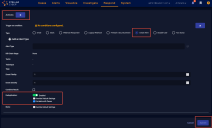
The Create an Alert Type dialog box appears:
-
Supply the following information in the Create an Alert Type dialog box
-
Alert Type – Required. Supply a unique, alphanumeric name for the custom alert type.
-
Tenants – Required. Either set to All Tenants or select the tenant groups and tenants that will have access to this custom alert type. Refer to Which Custom Alert Types Can I See and Act Upon? for information on how your tenancy determines which alert types you can see.
-
Kill Chain Stage – Select the XDR Kill Chain stage to which the custom alert type belongs from the dropdown.
-
Tactic – Select the tactic for the custom alert type from the dropdown. The available tactics are filtered according to the selected Kill Chain Stage.
-
Technique – Select the technique for the custom alert type from the dropdown. The available techniques are filtered according to the selected Kill Chain Stage and Tactic.
If you set a value for any one of the Kill Chain Stage, Tactic, or Technique fields, you are required to set all three. The dialog box will not let you select an invalid combination of these values.
-
Tags – Select tags for the custom alert type from the dropdown.
Tags are required if you do not set values for the Kill Chain Stage, Tactic, and Technique fields.
-
-
Click Submit to add the custom alert type to the list.
Your custom alert type will only appear in the list right away if the Show alert types without hits option is enabled at the top of the table. Because you just created the alert type, it likely won't have any hits yet.
Adding the Custom Alert Type to a Playbook
Once you've created a custom alert type you can add it to an Automated Threat Hunting playbook. You can either do this directly from the Respond | Automation page, or you can drill to a pre-filled template for a new playbook using the custom alert type as follows:
-
Create the custom alert type using the procedure in the previous section.
-
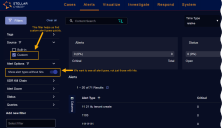
Ensure that the Alert options | Show alert types without hits option in the Filters panel is enabled and locate your new custom alert type in the Alerts table.
You can make it easier to find custom alert types by setting the Source filter in the Alert Types panel to Custom as in the figure below.
-
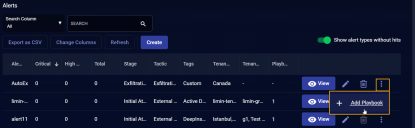
We just created the custom alert type named AutoEx. Now we can click its three-dot menu
 and use the + Add Playbook option to launch the standard ATH Playbook workflow with the template pre-filled to use our custom alert type.
and use the + Add Playbook option to launch the standard ATH Playbook workflow with the template pre-filled to use our custom alert type.
When you start a playbook using this technique, the template is automatically pre-filled with the Actions section populated based on the alert type's settings:
-
Type is set to Create Alert
-
Alert Type is set to the selected alert type.
-
Kill Chain Stage, Tactic, Technique, and Tags are all pre-filled based on the custom alert type's settings.
Editing Custom Alert Types
You can edit a custom alert type using its standard Edit button at the right of its entry in the Alerts table. Keep in mind, however, that once a custom alert type is assigned to a playbook, you cannot delete its assigned Tenants or Tenant Groups.
Which Custom Alert Types Can I See and Act Upon?
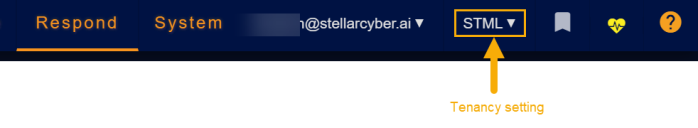
Stellar Cyber's policy is to restrict access to different objects based on ownership and tenancy. In general, you can only see and act upon custom alert types that were created by or assigned to a tenant or tenant group to which you are logged in as. Start by checking your Tenancy at the upper right of the display. For example, the user below is logged in with the STML tenant.
You can always see alert types set to All Tenants. From their, your tenancy determines which custom alert types you can see and act upon, as follows:
-
If you are logged in with a tenant and the tenant owns the alert type.
-
If you are logged in with a tenant and the alert type's tenant list includes the tenant.
-
If you are logged in with a tenant and a tenant group in the alert type's tenant group list contains the tenant.
-
If you are logged in with a tenant group and the alert type's tenant group list includes the tenant group.
-
If you are logged in with a tenant group and a tenant in the tenant group owns the alert type.
-
If you are logged in with a tenant group and a tenant in the alert type’s tenant list is in the tenant group.
About Deduplication for Custom Alerts
To reduce noise and focus attention, Stellar Cyber automatically deduplicates multiple instances of the same custom alert that fire within a small window of time (five minutes, by default). Stellar Cyber performs this deduplication by discarding fields that are always different between separate alerts, calculating a hash, and monitoring future events for matches.
You can override the default settings for deduplication of alerts created as part of an ATH Playbook and specify your own time window. Refer to Create Alert Action . ![]()
Certain fields are always different between two Interflow records, even if those records represent multiple iterations of the same alert. Because of this, they are discarded before the hash used to identify duplicate alerts is calculated. For that reason, the following fields are not considered when calculating the hash used for deduplication:
Exact matches between:
-
stellar_index_id
-
stellar_uuid
-
timestamp
-
timestamp_utc
-
write_time
-
xdr_event
-
index
-
id
-
type
Fields containing the following substrings:
-
stellar
-
time
-
date
-
index
About Correlating Alerts with Cases
The raw type of Automated Threat Hunting (ATH) custom alerts can be correlated with cases. A custom alert type is raw if there is no aggregation or correlation.
In addition, the following built-in correlation alert types use ATH correlation rules for detection and are correlated with cases:
-
Exploited C&C Connection
-
External/Internal Exploited Vulnerability
Alerts are correlated with cases if the Correlate with Cases checkbox is selected. The resulting deduplicated alerts are included in cases.
To correlate alerts with cases: