User Reported Phishing Email Alerts
Note: The automatic triage of user-reported phishing is available as part of the Early Access Program (EAP) and is only supported on Stellar Cyber in SaaS deployments. If this feature doesn’t appear in your version of the platform, contact your account manager to inquire about taking part in the Early Access Program and enabling this functionality.
When users report suspicious emails—typically via a "Report Phishing" button in their mail client—these submissions initiate an automated phishing triage workflow within the Stellar Cyber Platform. Reported emails are first collected in a centralized mailbox on your email system, which then forwards them to a Stellar Cyber–provisioned inbox that's unique to your tenant.
The phishing email triage agent, embedded in the Stellar Cyber Platform, retrieves each reported email and performs AI-driven analysis to assess its risk. The agent parses the email to extract observables and enriches them through three sources: its own internal processing logic, direct integration with the Stellar Cyber Threat Intelligence Platform, and third-party threat intelligence services. Based on this multi-source analysis, the agent determines a verdict and generates a structured alert in the Stellar Cyber UI. Each alert includes triage results, a threat score, and enriched observables—providing your analysts with actionable insight for investigation and response.
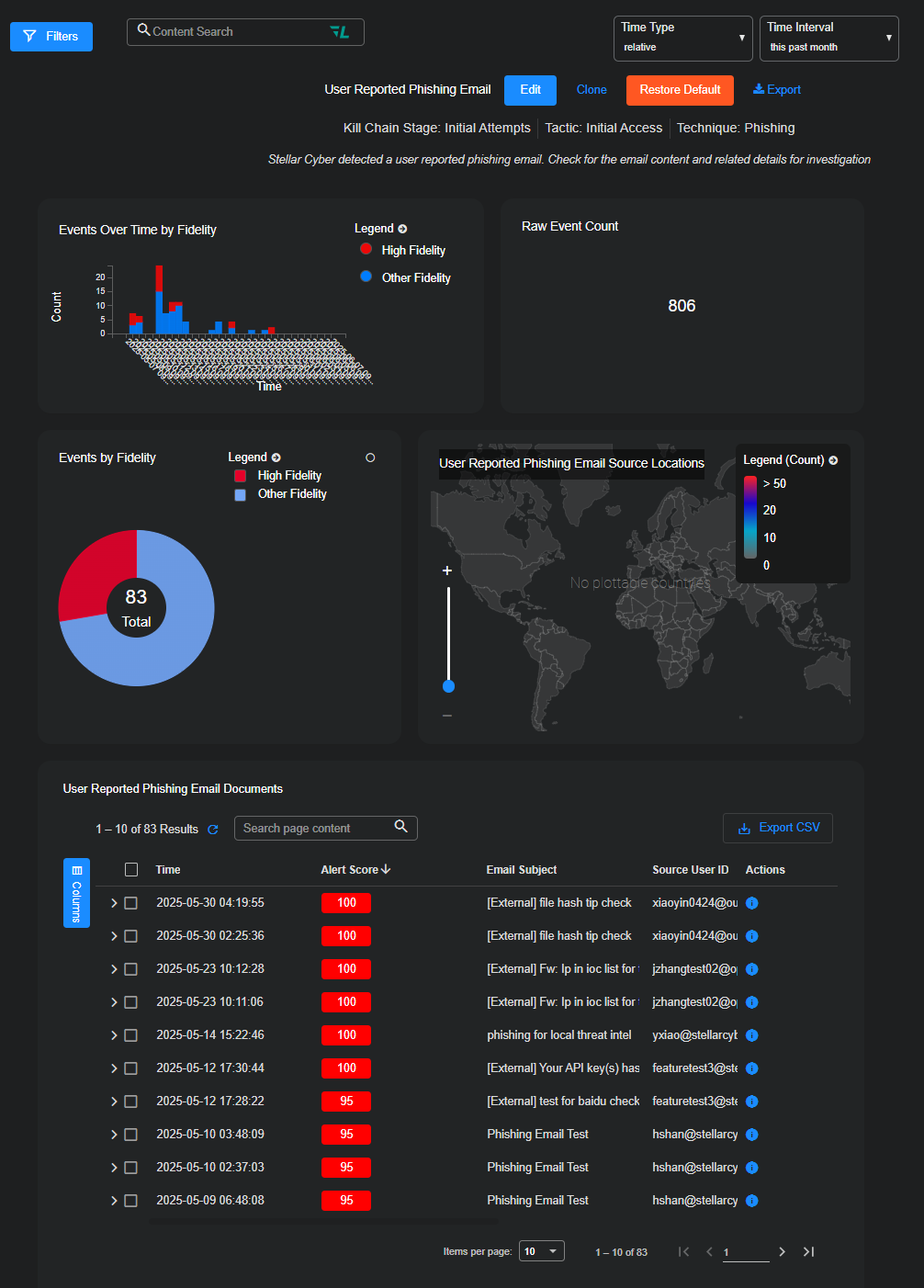
To view these alerts, go to the Alerts page and select View for a User Reported Phishing Email alert. Stellar Cyber displays the Alert Details page with visual summaries, a detailed documents table, and an expandable side panel with complete contextual and forensic data. The entries in this table are individual alerts, each one the result of a user-reported phishing email.
At the top of the Alert Details page, four visual widgets provide a quick overview of alert volume and characteristics:
-
Events Over Time by Fidelity – Displays alert trends over time, broken down by fidelity level (High Fidelity vs Other).
-
Raw Event Count – The total number of correlated raw events that contributed to this alert type.
-
Events by Fidelity (Pie Chart) – Graphical summary of alert fidelity distribution (e.g., number of high-fidelity alerts).
-
Source Locations Map – Shows geolocation data of source IPs, when available. A legend indicates the volume range per region.
These widgets help you assess the scope, trust level, and origination of reported phishing activity at a glance.
If you want to rearrange these widgets and the table below them, select Edit, drag them into different positions on a grid layout, and the Save your changes.
User Reported Phishing Email Documents Table
Beneath the widgets is the User Reported Phishing Email Documents table, which lists individual alert instances and their key components:
-
Time – Timestamp indicating when the alert was created.
-
Alert Score – Numeric severity rating (typically 100 for critical phishing alerts).
-
Email Subject – The subject line from the reported email.
-
Source User ID / User Email – The user who reported the phishing message, along with their email address.
-
Actions – Selecting the More Info icon opens the Alert Details side panel, where you can perform in-depth investigation.
Row Expansion: Selecting the arrow to the left of a row expands it to reveal its property metadata. You can then use the Quick Filters or Search for Details field to locate specific fields.
Alert Details Side Panel
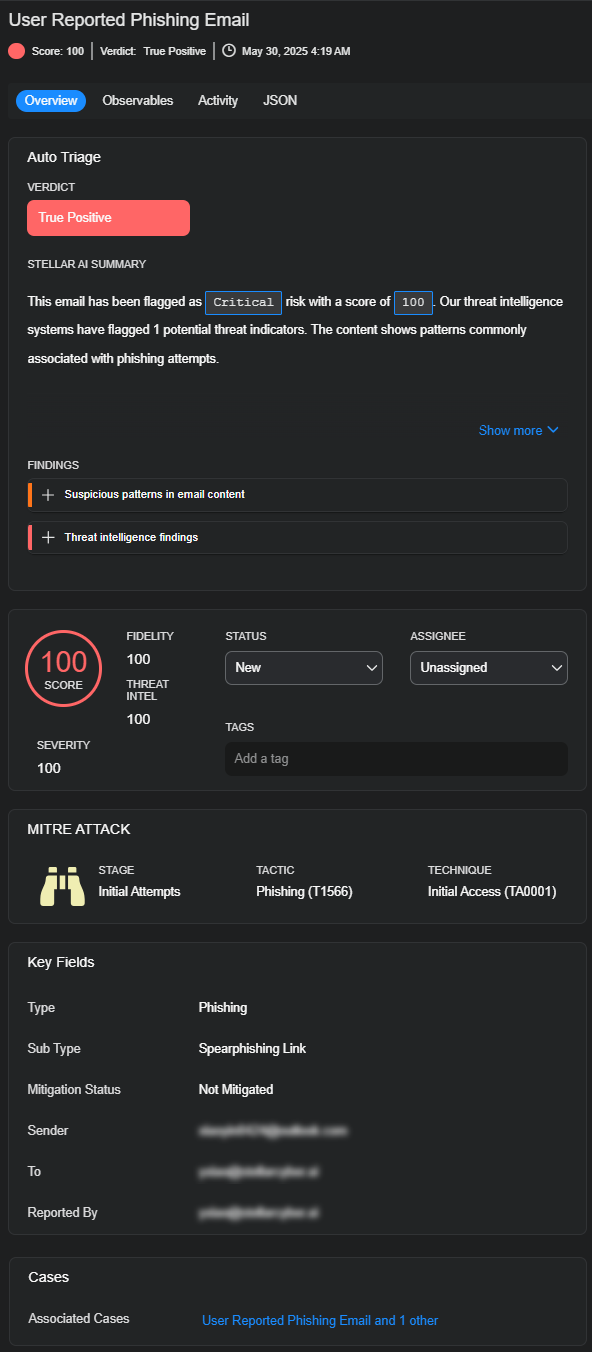
The Alert Details side panel for a User Reported Phishing Email alert consists of four tabs: Overview, Observables, Activity, and JSON. Together these four tabs provide both a high-level summary and a detailed technical breakdown so you can investigate and respond to alerts efficiently and accurately.
To expand the side panel to a full-page view, select the Maximize icon at the top of the panel. When expanded, the Overview tab appears on the left in a persistent display while the Observables, Activity, and JSON tabs appear on the right so you can switch between them and view their content while keeping the Overview tab open as well.
Overview tab: This tab provides a summarized view of the classification, severity, and threat intelligence findings of the alert.
-
Verdict – A verdict is the classification that Stellar Cyber assigns to a suspected phishing attempt after analyzing evidence gathered during the automated security investigation. It represents its judgment about the nature of an alert or case following the triage process.
There are four different verdict values and the state during review before a verdict is rendered:
-
True Positive: This verdict is for a security event that accurately identifies a real threat or malicious activity.
-
Benign True Positive: This is for an event that’s correctly identified as legitimate but non-malicious, such as a penetration test or legitimate software activity.
-
False Positive: A benign event was incorrectly flagged as a threat.
-
Inconclusive: The available evidence is insufficient to determine whether the event is malicious or benign.
-
Pending: The event has not yet been reviewed; this is the default status prior to classification.
-
-
Score and Severity – Displays the risk level as a numeric score, such as 100 for a critical threat.
-
Stellar AI Summary – Explains why the system generated the alert based on its analysis.
-
Findings – Findings are the key insights derived from the automated security checks performed during the triage process. Each one contributes to the overall classification of an alert and is supported by specific pieces of evidence. Findings are structured and categorized to enhance clarity and traceability.
In every case, Stellar Cyber provides a concise explanation of the identified issue, such as a suspicious behavior, failed validation, or known threat indicator. These insights collectively justify the final verdict assigned to the alert. Every finding corresponds to a distinct type of security check and is accompanied by a security value, which reflects its relative importance or associated risk level.
-
Metadata: This includes workflow details like status, assignee, and tags; MITRE ATT&CK classification, including the tactic (Phishing) and technique (Initial Access); and email details such as sender, recipient, reporter, and any associated investigation cases.
Observables tab: Observables are the individual data artifacts that can be detected on a system or network and might indicate malicious activity, policy violations, or other security-relevant behaviors. They serve as foundational elements of analysis—building blocks that underpin the creation and context of each alert.
This tab shows detailed technical information of the observables extracted from the email that triggered the alert:
-
Preview – Safely displays the email subject, sender, recipient, and body.
-
Domains & URLs – Lists email sender domains and any web links found in the message. It also includes threat scores and intelligence about the links, such as when they were first and last seen.
-
Headers – Shows the original email headers used for tracing the email’s delivery path.
-
Attachments – Provides file names and threat assessment data from integrated tools. Includes hash values (MD5, SHA1, SHA256) and links to external virus scanners like VirusTotal.
-
Raw Message – Displays the full original structure of the email (MIME content) for in-depth inspection.
Activity tab: This tab records all actions taken on the alert, including system updates and analyst comments.
-
All – Combines all recorded entries from both the Comments and History in a single view.
-
Comments – Shows notes entered by analysts during their review.
-
History – Lists system-generated updates, such as when the alert status changes (for example, from "New" to "In Progress") and when tags or assignments are modified.
Each entry includes a date, time, and the name of the user or process that made the change.
JSON tab: The JSON tab presents the full structured data for the alert using JSON format, which is a standard for storing and sharing technical information. It displays the complete data record that Stellar Cyber used to create the alert and includes technical fields such as the email source, alert provider, severity level, and MITRE ATT&CK tactic and technique identifiers. This tab is a particularly useful reference for automating workflows, validating individual data fields, or exporting structured alert information. If the JSON content is too long to display in its entirety, a “Show more” option is available to expand and reveal the full record.
Recommended Actions in Response to Email Phishing
In addition to reviewing the analysis in the Stellar Cybertellar Cyber UI, consider taking the following actions to respond effectively to validated instances of email phishing. You can perform the first action through ATH playbooks in the Stellar Cyber Platform. The remaining actions must be carried out using features in your email service or integrated security tools.
-
Notify Stellar Cyber users – Trigger an automated notification to yourself or other Stellar Cyber users through an ATH playbook. This ensures that relevant security personnel are immediately aware of the phishing incident and can take further steps as needed.
-
Isolate the email – Quarantine the phishing email to prevent recipients from opening or interacting with it. Act quickly to limit exposure and reduce the chance that others in your organization engage with the message.
-
Delete the email – Remove the phishing message from all affected inboxes. This eliminates the risk of users accessing the email after initial detection and helps contain the incident.
-
Search for similar messages – Use search tools in your email system to identify other messages that match the characteristics of the phishing email, such as sender address, subject line, or embedded URLs. This helps you assess the scope of the attack and find additional users who may have been targeted.
-
Notify affected users – Alert users of your email service who received or interacted with the phishing email. Provide clear instructions on what to do next, such as avoiding links, deleting the message, or reporting suspicious activity.
-
Block sender – Add the sender’s email address or domain to a blocklist within your email platform. Apply the block at the user level or organization-wide, depending on the risk level and your internal policy, to prevent similar emails from being delivered in the future.
-
Reset password – If a user’s credentials may have been compromised—especially if the phishing email included a credential harvesting link—require the affected user to reset their password. Enforce multifactor authentication where possible to reduce the likelihood of account misuse.
-
Block URL – Block any malicious URLs identified in the phishing message to prevent users from accessing harmful content. Coordinate this effort with your firewall, secure web gateway, or DNS filtering solution to ensure that the block is enforced across your network.
Manage Phishing Email Triage
After a user reports a phishing email and your mail system forwards it to the Stellar Cyber inbox, phishing email triage agent automatically retrieves the message, parses it to extract observables, enriches data using threat intelligence sources, and creates an alert. Each alert includes a threat score, observables, findings, a system-assigned verdict, and a static screenshot of the email body—enabling safe visual inspection without risk of triggering embedded threats.
You can review alerts from user-reported phishing emails directly in the Alerts panel. Use filters to identify relevant events by alert type, verdict, severity, or associated observables. Select an alert to open its detailed view, where you can examine the findings, preview the static screenshot, and assess the enriched indicators. The correlation ID enables navigation to related data across Threat Hunting, Interflow, and other investigation views.
Stellar Cyber generates one alert for every phishing report, even if multiple users report the same email. Each alert also results in the automatic creation of a case. You can access these from the Case Management interface, where you can assign ownership, add comments, or attach additional alerts manually if needed. Case records include a timeline of investigative activity and support collaborative tracking throughout the incident lifecycle.
While the Early Access Program (EAP) version of the phishing triage feature does not support direct response actions, you can configure ATH playbooks to route alerts, notify analysts, or assign cases automatically. For validated threats, follow the standard response procedures in your organization to contain exposure and inform affected users.
To maintain an effective triage process, regularly monitor phishing alerts, review open cases, and ensure that your analysts understand how to use correlation IDs, case views, and alert summaries. With these tools, you can manage phishing reports efficiently while preserving full visibility and control throughout the triage workflow.