Understanding the Legacy Kill Chain
Previous versions of Stellar Cyber organized the interface around the Lockheed Martin Kill Chain described in this topic. This organizing principle has been replaced by the XDR Kill Chain. You can still use the Dashboard | Legacy Dashboard option to view Stellar Cyber through the lens of the Lockheed Martin Kill Chain. However, Stellar Cyber strongly recommends you move to the new, MITRE | ATT&CK-compatible, XDR Kill Chain.
A central concept to implementing the Stellar Cyber mission is the Security Kill Chain, adopted from the original technology papers developed at Lockheed Martin.
The resulting methodology is both simple and powerful. This can be summarized as follows:
- Security events can be sorted into six categories, identified by the nature of the activity detected.
- The categories are generally (but not strictly) progressive in nature. In other words, an event might be related to a prior event in a lower level on the kill chain but sometimes is not.
- Each kill chain category has a different type of effect on the network and/or the host systems which are affected.
- Associated with each kill chain category is also a category or type of investigation and appropriate response.
- In addition to being assigned a kill chain category each security event can also be scored with regard to severity and fidelity.
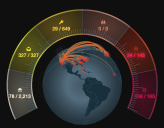
In the Stellar Cyber UI, the kill chain is featured prominently in several locations. The first is the Kill Chain Tachometer on the Home Page dashboard.
Note that a color is assigned to each segment. This color is applied in many other places in the UI.
The attributes of each segment of the kill chain are described in the following sections.
The tools and methods available to attackers are constantly changing. In the descriptions that follow, the examples represent only a few instructive possibilities of what a security event at any given point in the kill chain. Stellar Cyber is designed to adapt over time, keeping up with the real network to detect new types of malicious activity.
Reconnaissance
An attacker is looking for a way into the network or the hosts connected to the network. Typical methods will include:
- Port scanning
- Brute force login attempts
- Phishing
- Probes of known security holes
Often these types of attacks do not need a specific response because they are most often not successful or result in any useful information.
Stellar Cyber will still record these attacks to fill its database of known attackers and correlate it with data feeds of known attackers. This is useful if another security event appears later in the kill chain.
Delivery
The delivery phase refers to transmitting malware into a system. This can happen through several techniques:
- Copy operation (
rcp,rsync, etc.) via SSH after account access is established - HTTP transfer using tools such as
wgetorcurl - Delivery by email
- Removable memory device
When they occur these events may or may not be related to a reconnaissance event. Stellar Cyber uses machine learning and other resources to score the event's severity and fidelity. This scoring assists in determining the best response.
Exploitation
After delivery, an attacker's malware will generally attempt to gain access to the system. If the delivered malware does not already have administrative-level privileges to the system it will typically attempt to acquire them.
Installation
After sufficient access is acquired, the attacker's malware will often attempt to permanently install a backdoor that the attacker can use. In the process the software may attempt to hide itself in various ways to avoid detection, including system log and file system manipulation.
Types of malware that might be installed include:
- Webshell installation on a compromised web server
- Viral agent
- Keyboard loggers
Once installed, the attack can move on to the next phase.
Command & Control
This phase involves the owner of the malware establishing an illicit communication channel to the infected system. Nearly any protocol can be used and is most often selected to a) appear as normal traffic as much as possible, and b) be allowed by any firewalls or routers in the path.
For systems that do not have a public IP address, the communication link will have to be initiated by the infected system.
Actions & Exfiltration
When sufficient control is established, the intruder can use the infected system as desired, either by direct access or by pre-programmed time release. It is in this phase that the damage that was originally intended is done. This can include:
- Collect and transmit sensitive user information
- Trigger ransomware
- Reconnaissance on other systems both internal or external
- Destroy systems
- Modify data