Malware Sandbox
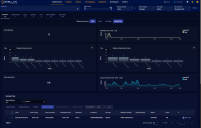
Stellar Cyber sensors can identify malware traveling through the network and arriving at specific hosts. You can use the Visualize | Predefined | Malware Sandbox page to see and analyze these observations. Use the category tabs at the top of this page to filter for specific malware types; the tabs have a count of event records for that category.
-
Overview – (Default) This category is the sum of all the other categories of malware
-
Ransomware – Malware that demands payment to undo damage
-
Trojan – Malware that appears as legitimate software
-
Spyware – Malware that is intended to reveal secret information
-
PUA – Potentially unwanted applications, such as adware
-
Other Malware – Uncategorized malware
-
Good Files – Files that were detected but are known to be benign
For details on alert types and actions you may consider, review the Alert Types. Stellar Cyber also provides an interactive tool that lets you look up alert types by data source, alert name, event type, or source index.
Dashboard Actions
You can perform the following actions on this dashboard:
-
Edit
-
Clone
-
Export as PDF/CSV
See the Dashboard Actions page for details on each action.
In addition, from the Overview tab, you can upload files for analysis.
The file upload is described in the File Upload section.
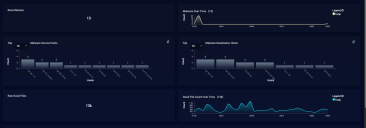
Data Graphs
The center portion of the screen shows graphic summaries of the events currently selected. An example of this is shown in the following images.
The information in this section includes:
-
Total Raw Malware—A count of all malware events for the current category and search results settings
-
Malware Over Time—A line graph that plots the time that malware was detected
-
Malware Source Hosts—A bar graph of the top hosts that deliver malware
-
Malware Destination Hosts—A bar graph of the top hosts that receive malware
-
Total Raw Good Files—A count of all good files seen within the current search results
-
Good File Count Over Time—A graph showing when the files were detected
File Upload
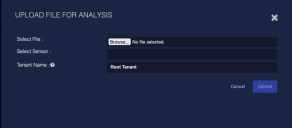
To upload files to be analyzed:
-
Click Upload File. The Upload File for Analysis screen appears.
-
Click Choose File to choose the file to be uploaded.
This field does not support multibyte or special characters. For example, the filename cannot include any of the following characters – (, ^, &, %, ^, &, $, %, ^, #.
-
Choose the tenant that will be identified in the JSON. Uploaded records are tagged with the selected tenant's name. This is useful if you're a root admin uploading a file for a tenant.
Note that the Tenant Name selected here does not need to be the same as the sensor's tenant. The dropdown lists all available tenants.
-
Choose the sensor that will do the analysis.
-
Click Upload. The file is uploaded.
-
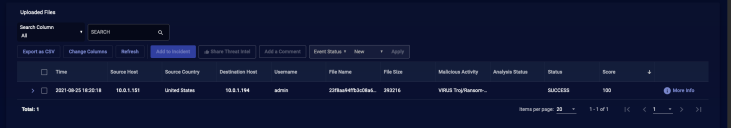
A green file upload was successful message appears when the upload finishes.
The results appear in the Uploaded Files table.
Depending on the files you uploaded and the sensor's workload, it can take up to 10 minutes to complete the analysis. Entries in the Uploaded Files table support the same options as the events table, described below.
See the Tables page for more information on working with tables.