Understanding Asset-Based Licensing 
As described in Licensing Overview, the DP can be licensed based on a count of the number of daily active assets. This topic provides details on asset-based licensing, including how assets are discovered, managed, and counted for licensing purposes. Refer to the following topics for details:
See also:
-
Understanding License Compliance provides details on how Stellar Cyber enforces license policies
-
The Respond | Reports | License Usage page lets you schedule and export PDF/CSV reports for Asset and Ingestion licenses
Classic Asset Counting vs. Entity-Based Asset Counting 
The 5.3.0 Stellar Cyber platform supports two asset counting models for licensing purposes:
-
Classic asset counting is based on a combination of MAC and IP addresses learned from a wide variety of sources, together with imported asset lists. If your platform was upgraded to 5.3.0 from a previous release, in most cases, it will be using classic asset counting. The exception is if you worked with Stellar Cyber Customer Success in the 5.2.0 release to try out the new entity-based asset counting model, in which case that model is still in use after the upgrade to 5.3.0.
-
Entity-based asset counting is a simplified model that relies on a combination of unique discovered IP addresses and email addresses.
-
If your Stellar Cyber platform is new in 5.3.0, it automatically uses the entity-based asset counting model.
-
For most deployments, the entity-based asset counting model results in more accurate asset counts. You can convert to the entity-based asset counting model using the instructions below.
Testing has shown that there is typically no more than a 5-10% difference in the assets counted by the two models, depending on your deployment.
-
Determining which Asset Counting Model Your Deployment Is Using
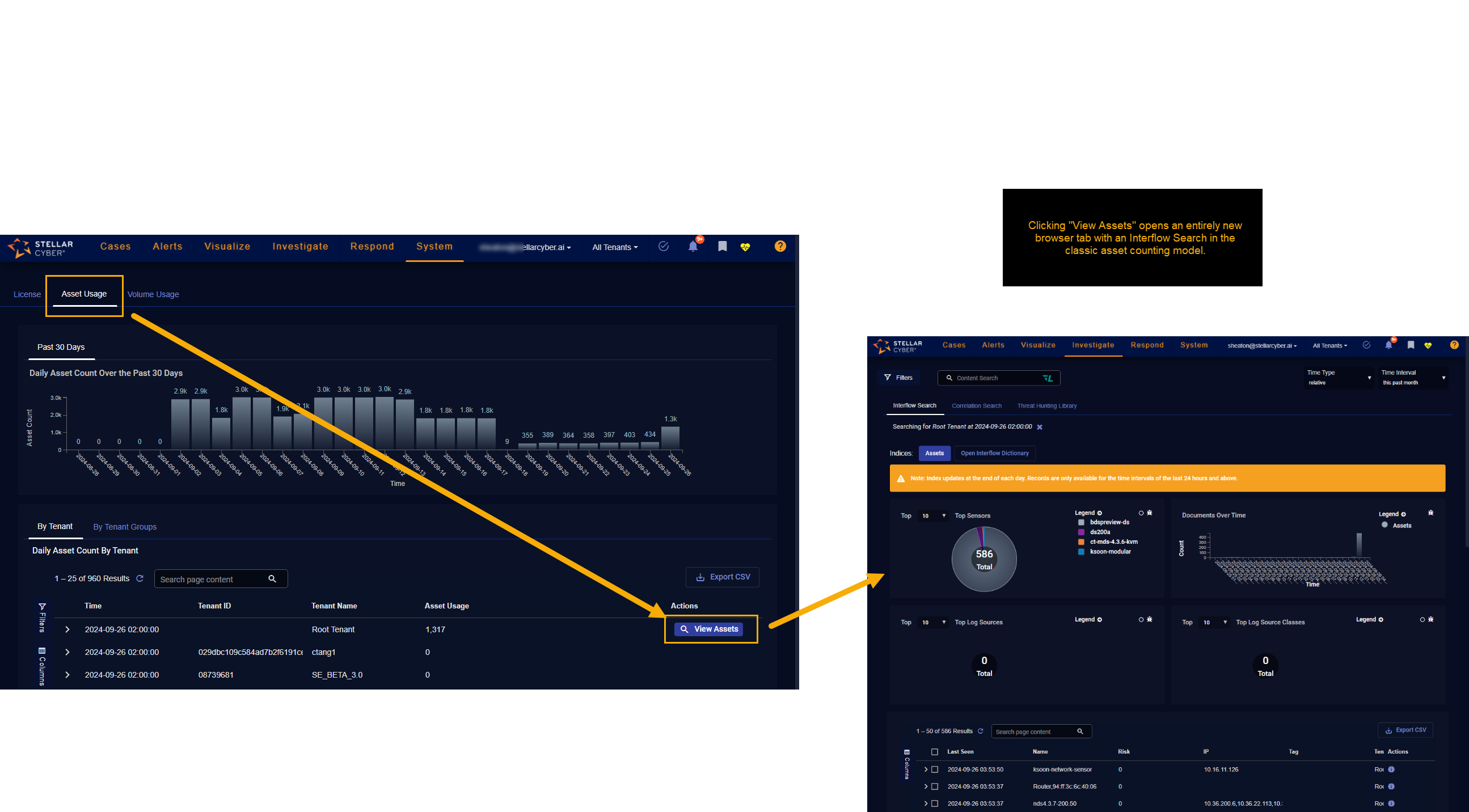
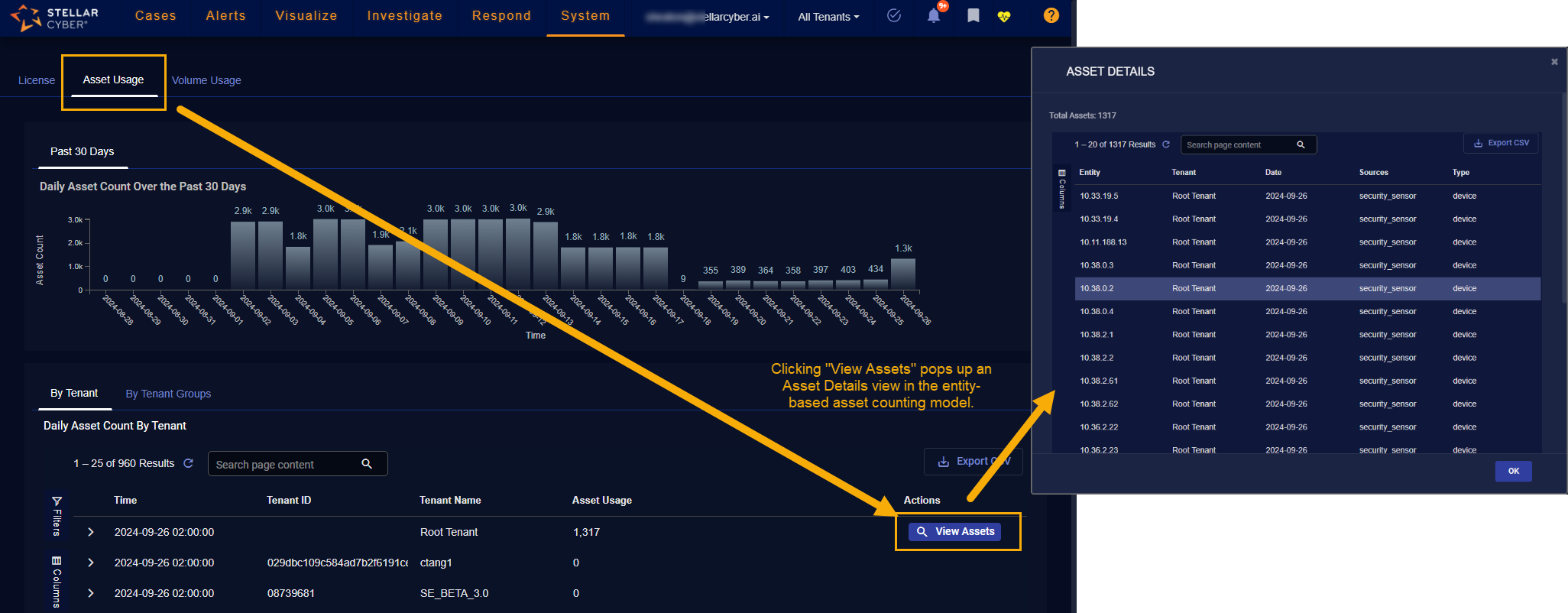
You can determine which asset counting model your deployment uses by clicking one of the View Assets buttons in the System | Licensing | Asset Usage tab's Daily Asset Count By Tenant table. This button works differently depending on whether you are using the classic asset counting implementation or the entity-based approach available in 5.3.0 and later:
-
Classic Asset Counting – If you are using the classic asset counting implementation, clicking View Assets opens a new browser ab with an Investigate | Threat Hunting | Interflow Search filtered on the Assets index for the selected tenant and time range, as illustrated below:
-
Entity-Based Asset Counting – If you are using the new entity-based asset counting implementation, clicking View Assets pops up an Asset Details view showing the entities detected for asset counting purposes for the specified tenant and time range, , as illustrated below:
Switching to Entity-Based Asset Counting
If you are on the classic asset counting model and would like to switch to the entity-based implementation, contact the Stellar Cyber Customer Success team for assistance.
After switching from the classic model to the entity-based model, make sure to refresh the table content in the System | Licensing | Asset Usage tab's Daily Asset Count By Tenant table so that it reflects the field names and data for the entity-based model.
Entity-Based Asset Counting
The sections below describe the new Entity-Based Licensing implementation used for fresh deployments of Stellar Cyber 5.3.0. This implementation is also available for customers who arrived at Version 5.3.0 by upgrade.
Entity-Based asset counting introduces several key improvements over the classic asset counting model by simplifying the process and leveraging only high-confidence sources for attributing entities against the subscribed license count.
This simplified model produces more consistent results and also reduces the system overhead required to determine entity counts, allowing the entity-based license model to scale beyond what could previously be support with the classic asset counting model.
If you are still using classic asset counting, refer to this section for instructions.
Overview of Entity-Based Licensing
For licensing purposes, entities are defined as the combination of unique devices and users discovered across the environment on any given day. Entities counted for licensing purposes are also referred to as assets.
Keep in mind that this definition of an asset for licensing purposes is different from the security assets found under Asset Analytics.
Asset discovery is performed differently for licensing than it is for security workflows:
-
Asset Discovery for Licensing – Designed for simplicity, leveraging only high-confidence sources for attributing entities against the subscribed license count..
-
Asset Discovery for Security Workflows – Resolved through a more complex process to catch corner cases useful for analysts.
Refer to MAC or IP-Identified Assets for details on how assets are discovered for security workflows.
Asset Discovery in the Entity-Based Model
The design goal for asset-based licensing in the entity-based model is to count assets with the simplest method possible. The design relies on simplicity because it is easy to understand, predict, trust, and scope. Although certain corner cases won’t be counted perfectly due to this simplicity, this is by design.
The total number of licensed assets per tenant per day is the total number of unique devices (measured by internal Source IP addresses) plus the total number of unique users (measured by email addresses). From a high level, these are counted as follows:
-
Devices – any private IP address observed in the sample window (either from a trusted data source or inferred from observed traffic; see below for details).
-
Users – any logical account with a valid email address as an identifier observed in the sample window, including accounts assigned to non-human actors such as service accounts.
Device Discovery in the Entity-Based Model
Devices can be identified either from trusted data sources or inferred from certain types of network data. The total device entity count is the sum of all unique IP addresses from both sets of data, as described below.
Trusted Endpoint Data Sources
Some data sources, such as EDR solutions, provide an inventory of their assets. In this model, the discovered hosts’ private IP addresses are reported as assets. Data from a managed list of sources that are known to produce less accurate results is excluded from consideration. For example:
IF (msgtype == "Asset Record" AND msg_origin.source IN trusted_data_source)
AND NOT (msg_origin.category == "firewall" OR msg_origin.category ==
"traffic"):
return(asset)Inferred Devices (From Sensors, Firewalls, VPNs, and Traffic)
For data originating from sensors, firewalls, and other network devices, asset IP addresses are inferred from network flow data, subject to the following rules:
-
The IP address must belong to one of the following groups:
-
Private address spaces defined in RFC-1918
-
CGNAT address space defined in RFC-6598
-
Customer-defined IP ranges
-
-
The IP address must be observed to send traffic twice within a sample period.
User Discovery in the Entity-Based Model
Users are identified either from trusted user data sources or inferred from observed activities from specific productivity platforms. The total count is the sum of all unique email addresses from these sources.
For data originating from Microsoft 365 or Google Workspaces, user entities are extracted from activity logs in connected Microsoft 365 and Google Workspaces environments.
Microsoft 365
For user entities discovered using email addresses from Microsoft 365, either the UserId or MailboxOwnerUPN field must be a valid email address.
Google Workspaces
For user entities discovered using email addresses from Google Workspaces, the following must all be true:
-
The email field is a valid email address
-
The profileId field has a value
-
The owner and calendar_id fields are not populated (this omits certain accounts created by third party applications that have integrated with Google Directory or Google SSO).
User Discovery Pseudocode
Stellar Cyber uses filtering logic to ensure that identified users represent real user accounts (is_valid_user_account) and not an alias or something of no security value. The simplified logic for user discovery is as follows:
IF (msg_origin.category == "identity" OR msg_origin.category ==
"office_suite" OR msg_origin.category == “directory”):
IF (record.is_valid_user_account()):
return(record.email)Each data source has a different implementation of is_valid_user_account(). Stellar Cyber studies each data source and employs conservative discovery methods. For example, the implementation for Google Workspace is as follows:
// Exclude non user records like 3rd party calendar apps
IF (gsuite.actor.profileId.exists()
AND gsuite.email.is_valid_email()
AND NOT event_detail.owner.exists()
AND NOT event_details.calendar_id.exists()):
return(True)About Asset Count Timing
The Asset Discovery process happens in real time as new data comes into the system. Each day at 11:59 PM UTC, Stellar Cyber counts the total of all the unique assets (devices and users) per tenant for that given day. Importantly, if an IP address is discovered across multiple sources on a given day, it is only counted once for that day. The results are reported in the System | Licensing | Asset Usage page.
Asset Counting Example
The following example shows how this works for a sample customer with two tenants:
-
Tenant A has a Crowdstrike connector and a Modular Sensor deployed
-
Tenant B has an Office 365 connector and three Windows Server Sensors deployed
Tenant A Asset Data
Tenant A has the following asset data from it sources on Day 1:
-
CrowdStrike Connector
-
Assets – 192.168.0.1, 192.168.0.2
-
-
Modular Sensor
-
Discovered one traffic event sourced from 192.168.0.3 and ten traffic events sourced from 192.168.0.1
-
Tenant B Asset Data
Tenant B has the following asset data from its sources on Day 1:
-
Office 365 Connector
-
Valid Users - bob@tenantb.com, alice@tenantb.com
-
-
Windows Server Sensors
-
Deployed on three devices – 192.168.0.1, 192.168.0.2, 192.168.0.3
-
Total Day 1 Discovered Assets
The total number of discovered assets across all tenants on Day 1 is 8, as summarized in the table below:
|
Day |
Tenant |
Asset |
Type |
Sources |
|---|---|---|---|---|
| Day 1 | Tenant A | 192.168.0.1 | Device | CrowdStrike, Modular Sensor |
| Day 1 | Tenant A | 192.168.0.2 | Device | CrowdStrike |
|
Day 1 |
Tenant A |
192.168.0.3 |
Device |
Modular Sensor |
| Day 1 | Tenant B | bob@tenantb.com | User | Office 365 |
| Day 1 | Tenant B | alice@tenantb.com | User | Office 365 |
| Day 1 | Tenant B | 192.168.0.1 | Device | Windows Sensor |
| Day 1 | Tenant B | 192.168.0.2 | Device | Windows Sensor |
| Day 1 | Tenant B | 192.168.0.3 | Device | Windows Sensor |
| TOTAL ASSETS |
Tenant A & Tenant B |
8 |
n/a |
n/a |
Checking Entity Counts in the API
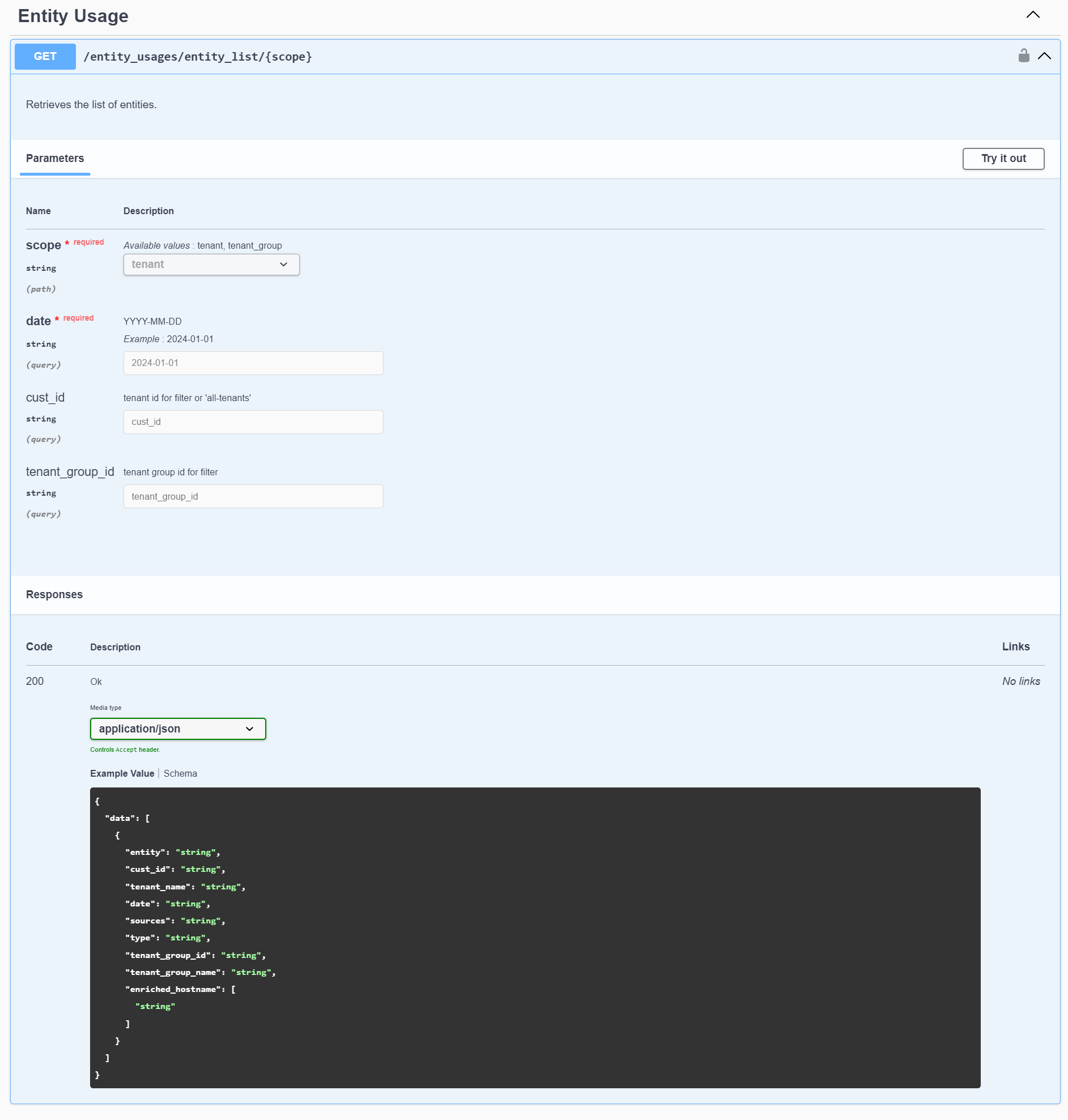
You can use the Entity Usage endpoint in the Stellar Cyber API to check entity-based asset counts. The Entity Usage endpoint is available here:
/connect/api/v1/entity_usages/entity_list/tenant?date=<YYYY-MM-DD>&cust_id=<tenant id>
For example, the following endpoint retrieves the entity usage for the tenant with the ID of 088428cf6adf4920b8dfde8636124c6b on October 22, 2024:
/connect/api/v1/entity_usages/entity_list/tenant?date=2024-10-22&cust_id=088428cf6adf4920b8dfde8636124c6b
You can also work with the Entity Usage endpoint in the reference material from the API's swagger.json file, as illustrated below:
Frequently Asked Questions on Entity-Based Asset Counting
The following section provides answers to frequently asked questions on Entity-Based Asset Counting.
You can also click here to open a downloadable PDF summarizing entity-based licensing and these frequently asked questions.
How are devices with multiple IP addresses handled?
If you have a device with multiple IP addresses, each unique IP address is considered to be a unique entity for asset counting purposes. Each unique IP address often has a unique set of applications listening on the address, even when it is assigned to a host with other IP addresses. Each unique IP address has a unique fingerprint and security profile and is treated as a unique entity. The logical association at the host level is only used contextually.
Many devices on my network use DHCP. Is each device counted multiple times for each IP lease it receives?
Yes, each observed IP that meets the criteria listed above is counted as a unique entity. Stellar Cyber recommends the following approaches to limit this:
-
Eliminate double-counting by using IP reservations with DHCP where possible.
-
Set DHCP lease periods to at least 24 hours to limit this to only counting devices twice
My network consists of many mobile devices. When a device switches wireless access points, it may receive a new IP address. Are these counted as unique entities?
Yes, each observed IP address that meets the criteria listed above is counted as a unique entity. Stellar Cyber recommends configuring 802.1x session persistence to reduce the number of duplicate entities. This can also be configured to eliminate double-counting when a device changes connectivity mediums (for example, a devices switches from a wired to a wireless connection).
I have multiple sites with overlapping IP spaces. Are each site’s IPs counted independently?
No. If two separate sites with overlapping IP spaces are sent to the same Data Processor (DP), two devices with the same IP address are counted as a single entity. Because this can cause confusion in correlation models, Stellar Cyber recommends using globally unique IP spaces where possible. In cases where this is unavoidable, we recommend deploying a separate Data Processor on each site to ensure the address spaces do not collide in correlation models.
I use auto-scaling groups. Is each ephemeral instance’s IP counted uniquely?
Yes. Each unique observed IP is counted as a unique entity. Stellar Cyber recommends configuring the auto-scaling group to use sequential IP addressing in specific ranges to ensure double-counting does not occur. If you are using DHCP, choose a scheme that reissues the lowest available address in the pool.
I use eBPF to monitor network traffic from Kubernetes. Are the IP addresses of my containers counted as entities?
Yes. Each container’s IP address (including shared addresses on virtual interfaces) is considered a unique entity. Stellar Cyber recommends using predictable addressing in Kubernetes to avoid double-counting.
I have multiple domains registered in Microsoft 365 and users have email aliases in each domain. Are these counted multiple times?
Yes, if activities are observed for the same user but with duplicate email addresses, the number of unique email addresses is used to determine the entity count. Stellar Cyber recommends encouraging your users to use only the primary domain for authentication – all subsequent actions will be associated with a single identifier.
Are service accounts counted as entities?
If the service account has a valid email address, it is counted as a user entity. In most cases, monitoring these non-human user accounts is important (for example the AWS root account). The presence of a valid email address is the simplest determining factor and this is used by the asset counting model.
Classic Asset Licensing
This section describes the classic Asset Licensing implementation used in previous versions of Stellar Cyber. This implementation is still in use for customers who arrived at Version 5.3.0 by upgrade and have not explicitly converted to entity-based asset counting.
Classic Asset Licensing Overview
Asset licensing is based on the following processes:
-
Asset Discovery – The discovery of assets based on all available data sources
-
Asset Management – The continuous management of assets seen in a deployment
-
Asset Licensing Counting – Daily counts of active assets for purposes of comparing to license limits
Asset Discovery and Asset Management are the same processes that build data shown under Investigate | Asset Analytics, in addition to supporting license counting.
Classic Asset Discovery
Stellar Cyber uses a passive discovery service to identify assets from observed data. Assets can be discovered via data collected by any of the following:
-
Network Sensors
-
Log Forwarders
-
Linux and Windows Server Sensors
-
Connectors (some)
At a high level, any device with an observed MAC address or internal IP address is identified and tracked as an asset. The discovery service uses data extracted from Dynamic Host Configuration Protocol (DHCP) and Domain Name Service (DNS) traffic to keep its running list of assets up to date, as well as to eliminate any duplicates when an asset has multiple MAC or IP addresses.
To improve the accuracy of asset counting, the discovery process does not count destination IP addresses that have not sent packets. This prevents the counting of, for example, IP addresses that were sent SNMP or ICMP requests but did not respond.
Classic Asset Management
The asset discovery process results in a list of assets tracked with the following data:
-
MAC Addresses
-
IP Addresses
-
Hostnames
How Stellar Cyber Uses Incoming Asset Data to Create and Updates Assets (Classic)
Different data sources provide different asset information, often reporting more than one value for a given field. For example, an EDR agent may report that a server has one MAC Address, two IP Addresses, and one Hostname while network traffic may show only one IP address and no associated MAC Addresses or Hostnames.
Stellar Cyber tries to define an asset as a single device, making logical sense of the different addresses and hostnames received in asset data from different sources. However, because of differences in infrastructure and networking, there are always corner cases and seeing those corner cases in the data is expected.
In general, Stellar Cyber uses the following logic to determine whether incoming asset discovery data is used to update an existing asset or create a new one:
-
Ifincoming asset discovery data shows a MAC Address that is already in Asset Management, use the asset discovery data to update its associated IP Addresses and Hostnames, if available. -
Elseif the asset discovery data shows a Hostname that is already in Asset Management, use the asset discovery data to update its associated IP Addresses, if available. -
Elseif the asset discovery data shows an IP address that is already in Asset Management, use the asset discovery data to update other linked IP Addresses, if available. -
Else, add the asset discovery record to Asset Management.
Example
Consider an existing Asset Management record with the following data:
-
<MAC Addresses: [ABC], IP Addresses: [123], Hostname: []>
In this case, if newly received asset discovery data shows the same MAC address associated with IP Address 456 and Hostname XYX, Stellar Cyber uses Rule 1 in the previous section to update the record as follows, adding the newly discovered IP address and hostname:
-
<MAC Addresses: [ABC], IP Addresses: [456, 123], Hostname: [XYZ]>
Router Identification
In addition to tracking IP addresses, MAC addresses, and hostnames, Stellar Cyber also looks for situations where a high number of IP addresses are associated with only a few MAC addresses and classifies such assets as routers.
Pruning Dormant IP Addresses
Because of the dynamic nature of IP address assignment through mechanisms such as DHCP, Stellar Cyber phases IP addresses without associated MAC addresses or hostnames out of Asset Management after three days of inactivity (default value; configurable). This is the only scenario where Stellar Cyber phases an asset out. You can prevent IP address assets from being phased out by marking them as static in the Investigate | Asset Analytics | IP Identified Assets page.
You can tell which assets are subject to pruning in the Investigate | Asset Analytics page's primary views:
-
MAC Identified Assets – These assets have a MAC Address tracked and are not deleted after discovery.
-
IP Identified Assets – These assets do not have a MAC Address tracked and are phased out after a specified number of days of inactivity (three, by default) if not marked as static.
Classic Asset License Counting
Every day, Stellar Cyber takes a snapshot of the assets that were active during the previous day and reports the results in the System | Licensing | Asset Usage page. An asset is considered active if it was seen in one or more data sources during the previous day.
Keep in mind that the total number of assets reported in the System | Licensing | Asset Usage page is typically less than the sum of the assets shown in the MAC Identified Assets and IP Identified Assets pages. This is because the Asset Usage page reports only those assets that were active the previous day, while the MAC Identified Assets and IP Identified Assets pages report both active assets and ones that were seen previously but were not active during the previous day. Only those assets that were active the previous day count against your licensed total.
Asset license violations are reported as follows:
-
Stellar Cyber reports a violation of the asset license if the count of active assets during a given day exceeds the license limit by 10% or more.
-
Stellar Cyber reports a more serious violation if the count of active assets exceeds the license limit by 10% or more for five days in a row.
-
Stellar Cyber reports a monthly violation if the count of active assets exceeds the license limit by 10% or more for 10 or more days in a given month (not necessarily consecutive days).
Frequently Asked Questions on Classic Asset Licensing
How can assets be filtered out to prevent them from being counted against my licensed total?
The only way to filter out an asset to prevent it from counting against your licensed total, is to set filters to remove that asset before ingestion for each data source where it could be discovered. Because only active assets are counted towards your licensed total on any given day, rarely-discovered assets won’t have a major effect on average daily counts.
Filtering Assets Out
How can assets be filtered out to prevent them from being counted against my licensed total?
The only way to filter out an asset to prevent it from counting against your licensed total, is to set filters to remove that asset before ingestion for each data source where it could be discovered. Because only active assets are counted towards your licensed total on any given day, rarely-discovered assets won’t have a major effect on average daily counts.
Asset Counting and License Violations
Every day, Stellar Cyber takes a snapshot of the assets that were active during the previous day and reports the results in the System | Licensing | Asset Usage page.
Keep in mind that the total number of assets reported in the System | Licensing | Asset Usage page is typically less than the sum of the assets shown in the MAC Identified Assets and IP Identified Assets pages. This is because the Asset Usage page reports only those assets that were active the previous day, while the MAC Identified Assets and IP Identified Assets pages report both active assets and ones that were seen previously but were not active during the previous day. Only those assets that were active the previous day count against your licensed total.
Asset license violations are reported as follows:
-
Stellar Cyber reports a violation of the asset license if the count of active assets during a given day exceeds the license limit by 10% or more.
-
Stellar Cyber reports a more serious violation if the count of active assets exceeds the license limit by 10% or more for five days in a row.
-
Stellar Cyber reports a monthly violation if the count of active assets exceeds the license limit by 10% or more for 10 or more days in a given month (not necessarily consecutive days).